Using ContentBarrier
- Refining ContentBarrier Configurations
- How ContentBarrier Filters Internet Content
- Using Schedules
- Recording Internet Usage
- Other Filtering Options
- Using Logs
Refining ContentBarrier Configurations
You've seen how to use the ContentBarrier Setup Assistant to create and configure your users, in the section Using the Setup Assistant. You can also make changes to these configurations from ContentBarrier's main window, which provides access to more detailed configuration options, as well as an overview of your users' settings and a summary of their past activities.
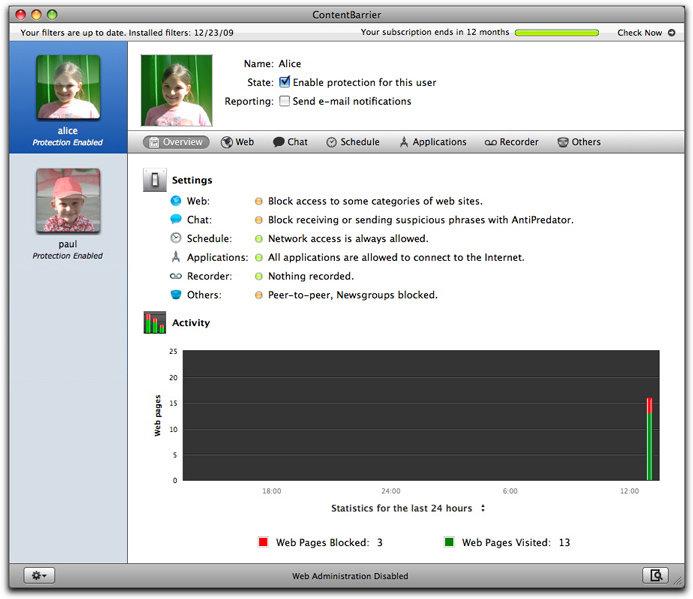
The above screen displays whenever you launch ContentBarrier, and its contents correspond to the user selected in the Users list. It shows you the following:
- User information: at the top of the screen, you see the user's name, whether that user's Internet access is being filtered, and whether you're receiving reports on that person's Internet usage. You also see a silhouette for the user, or a photo, if you have set one.
- Filter settings: the middle section shows the current settings for each of ContentBarrier's filters. A colored dot next to each one gives you information about the type of filtering: green means there are no restrictions or monitoring, orange means there are some restrictions, and red means access is being blocked or tracked. Texts next to each filter icon give you more information about the filter and its settings.
- Usage report: the bottom section shows a usage report for the user, such as how many web pages they have visited and how many have been blocked. By default, the chart shows statistics from the past 24 hours, but by clicking on the text Statistics for the last 24 hours you can change it to 7 or 30 days. Note that the number of web pages displayed is usually more than the actual number of pages visited, because most web pages are made up of multiple elements, each of which comprises a request to a web server. Each request is counted.
You can also access the log for the selected user by clicking the Log button, which looks like this:

For more on logs, see Using Logs later in this manual.
How ContentBarrier Filters Internet Content
ContentBarrier separates its filtering functions into four categories: Web, Chat, Applications, and Other. In addition it has the ability to record users' actions without their knowledge ("Recorder"), and you can limit Internet access entirely according to a schedule that you set ("Schedule"). Each of these six tools is represented by a button underneath the user's information in ContentBarrier's main window.
Next, we'll discuss each of these tools in detail. You can return to the Overview screen at any time by clicking the Overview button.
Web Filtering
ContentBarrier gives you three options to prevent the selected users from accessing certain web sites. They are: Allow access to all web sites, Block selected categories of web sites, and Only allow selected web sites. Each has its own screen of configuration options that resembles the screens you saw during the setup process, except with more options.
The Allow access to all web sites option is the simplest, as there are no settings: if you select this radio button, the selected user can view any web site.
The Block selected categories of web sites choice is ContentBarrier's default. It provides the most options, which are divided into five tabs: Categories, Trusted Web Sites, Blocked Web Sites, Keywords, and Advanced.
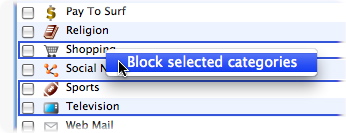
When you check this radio button, the Categories tab is selected and you see a list of web site categories with the Alcohol, Gambling, Hacking, Racism, Sex/Pornography, and Violence categories turned on - that is, blocked from this user. To prevent this user from browsing web sites in other categories, check their boxes; to allow access to categories, uncheck their boxes. (Filtering is done by analyzing keywords in web pages, as well as by a list of web sites maintained by Intego and updated regularly via NetUpdate.)
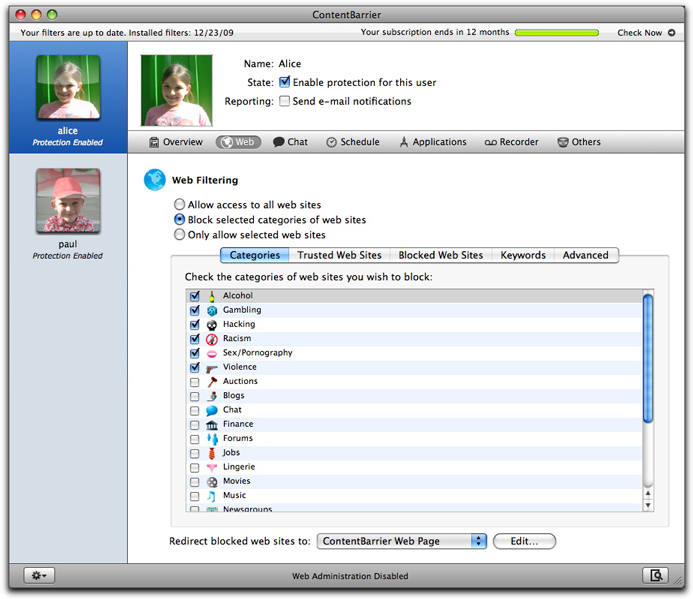
You can also change whether a category is blocked for this user by clicking a category while holding down the Control key, then choosing Block selected categories or Allow selected categories from the contextual menu. By clicking multiple categories while holding down the Shift or Command key, you can block or allow multiple categories at once.
Next, you can choose to allow your user to access certain web sites, regardless of whether they fall into a forbidden category, by clicking on the Trusted Web Sites tab. To add a web site to this list, click the plus sign at the bottom of the screen, which puts "www.example.com" into the list. This is just a placeholder: to change it to the site of your choice, double-click that line and type the site for which you want to allow access.
Note that all subdomains will be allowed, so allowing google.com also allows www.google.com, maps.google.com, and news.google.com. However, the opposite isn't true: If you allow only www.google.com, the user will be unable to reach google.com (without the www).
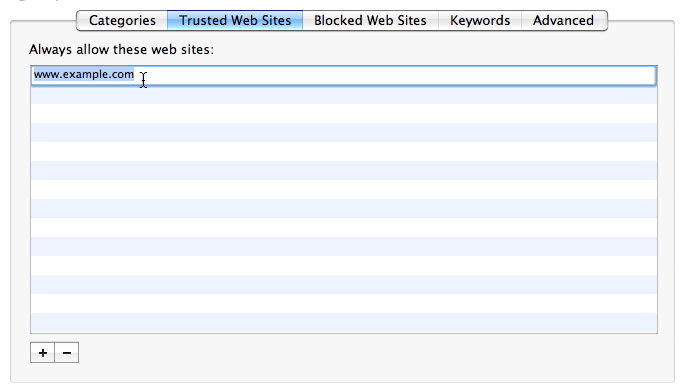
To remove a site from the list, click it and either press the Delete key or click the minus sign at the bottom left of the list.
You set up Blocked Web Sites and Keywords in exactly the same way as you set up Categories, after clicking on the appropriate tab. They function as their names suggest:
Users can never reach a site that you've listed on their Blocked Web Sites, even if it doesn't fall into any forbidden categories.
If you've created any entries in a user's Keywords list, that user can't reach any site on which that word appears.
In the event of a conflict - if you've listed the same web site listed in both the Trusted Web Sites and Blocked Web Sites lists, for example - ContentBarrier will block the site.
Last in the Block selected categories of web sites section is the Advanced tab. It has two settings:
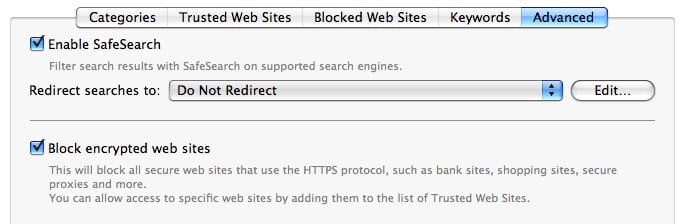
- Enable SafeSearch, which prevents the user from seeing questionable sites in the search results of several popular search engines, such as Google and Yahoo, which offer a SafeSearch feature. You can go one step further and prevent your user from performing any kinds of searches on these sites by selecting a web page listed on the Redirect searches to: popup menu. (You can add your own web page - or a local file on your computer - to that popup menu by clicking Edit….)
- Block encrypted web sites prevents the user from reaching any site that uses the HTTPS protocol, as is common in sites where money or confidential information changes hands. Checking this box will effectively stop nearly all online shopping, although it will also block other sites.
The third option for controlling access to web sites is Only allow selected web sites, which has two tabs:
- White List, which works in exactly the same way as the Trusted Web Sites list described above; and,
- Searches, which lets you filter with Safe Search enabled, as described above, on search engines that offer this feature.
Regardless of how you decide to block (and allow) access to sites, the popup menu at the bottom of this window gives you a choice of what happens when your user attempts to reach a blocked site.
By default users will be sent to a web page that tells them why ContentBarrier has blocked their access.
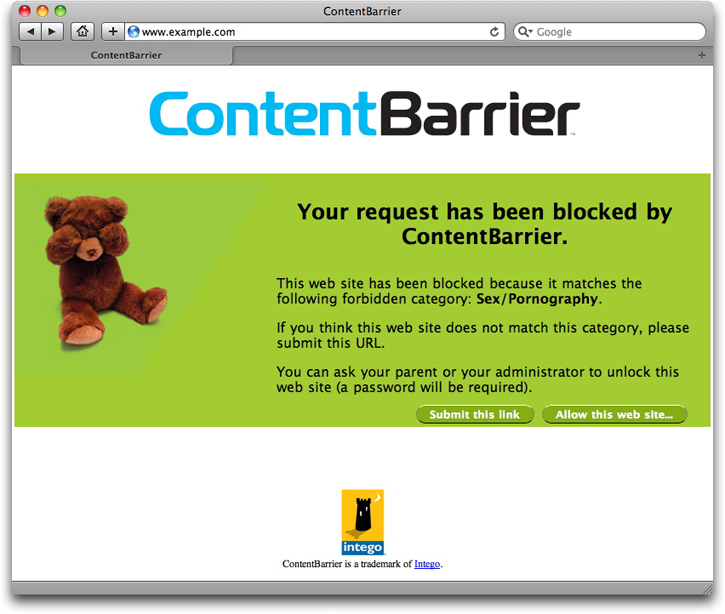
To give this user access to the page - if it was incorrectly blocked, for example - click the Allow this web site… button at the bottom of the page. A dialog box comes up with options to give access to the entire domain (example.com in this case), just the specific web page the user attempted to access, or any web page containing a specified text.
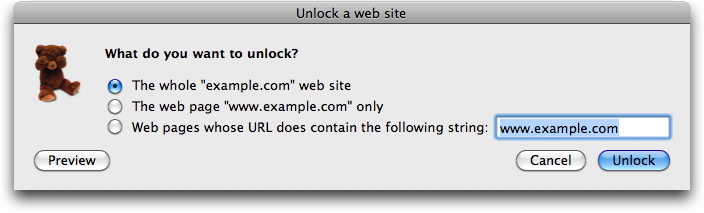
Clicking either Preview or Unlock requires you to enter an administrator's password, preventing ordinary users from unlocking sites without permission. (The only thing a non-administrative user can do from here is click Cancel, leaving the site blocked.)
If you click Preview, a window appears that displays the requested page so you can check to see if it's safe; you'll see the choices given above. Unlock provides access to the page, site, or pages containing the specified text, depending on which of these you have checked.
If you feel a web site was blocked unjustly, you can click Submit this link, which will send a report to Intego. Intego will examine the page and see if we feel it should not be blocked.
Chat Filtering
ContentBarrier lets you filter or block chat sessions, and offers a powerful function to protect your children when using chat programs such as iChat, ICQ or AIM instant messaging software. The AntiPredator function filters chat texts for predatory language - that is, language asking for personal information about the user. This includes such questions as "are you home alone?" and "what is your phone number?".
To enable chat filtering, select the user you wish to control in the left column, then click the Chat button. As with web filtering, you have three options: Allow all chats and Block all chats (which need no explanation), and Block suspicious phrases with AntiPredator, which we'll examine.
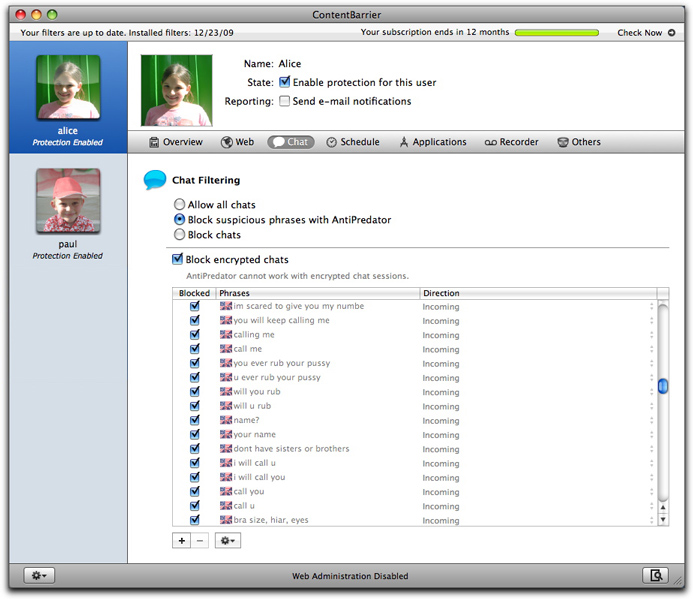
ContentBarrier's AntiPredator comes with a set of basic text strings as filters for incoming data, and several languages are available. You can choose to display all filters, filters in a specific language, or just custom filters that you add to the list either by:
- Pressing your keyboard's Control key while clicking on a phrase, or,
- Clicking the Action menu (with a gear depicted on it) below the list of phrases.
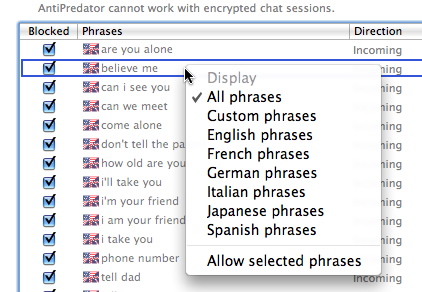
By default, all the AntiPredator phrases are active when you turn on chat filtering. You can disable any of them if you wish by unchecking them; by selecting them and clicking the Action menu and choosing Allow selected phrases; or by clicking them while pressing your keyboard's Control key and choosing Allow selected phrases.
While ContentBarrier contains an extensive list of text strings to be filtered, you can also add your own words and phrases. You could add, for example, your address or phone number, as well as any other personal information you feel should be protected.
To add a filter for either Incoming or Outgoing data, click the + button. A new line displays at the top of the filter list. Enter the word, phrase or sentence you wish to filter, and enable it if desired by checking the box to its left.
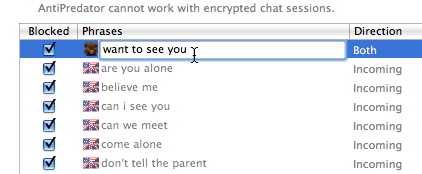
Click the menu in the Kind column and select whether you want this text to be filtered for incoming chats, outgoing chats or both.
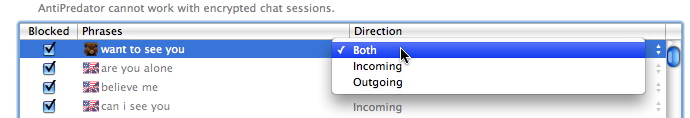
It is best to filter the shortest possible texts. ContentBarrier looks for the exact text you have entered in the filter, and, if the user types it differently, it will not be blocked. For example, rather than enter "my phone number is 555-1999", it is best to enter just "555-1999".
Using Schedules
ContentBarrier lets you set a schedule for each of your users that allows them to access the Internet only on certain days and for a certain length of time. To access schedule settings, click the Schedule button in the ContentBarrier button bar.
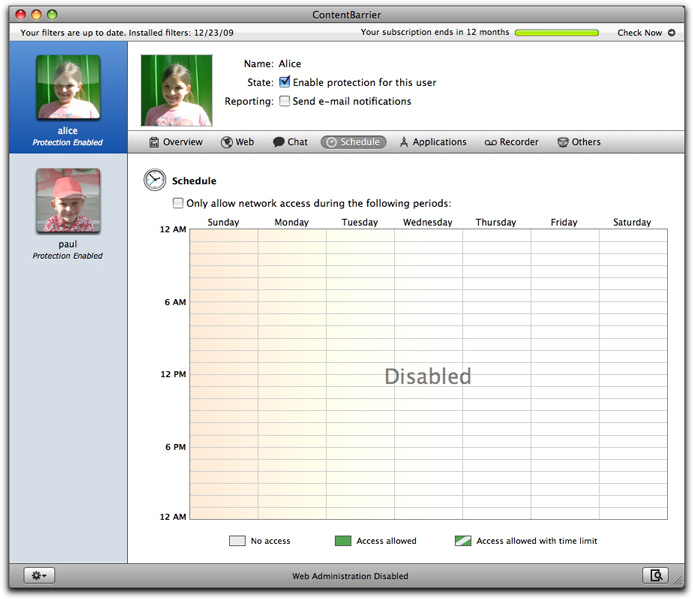
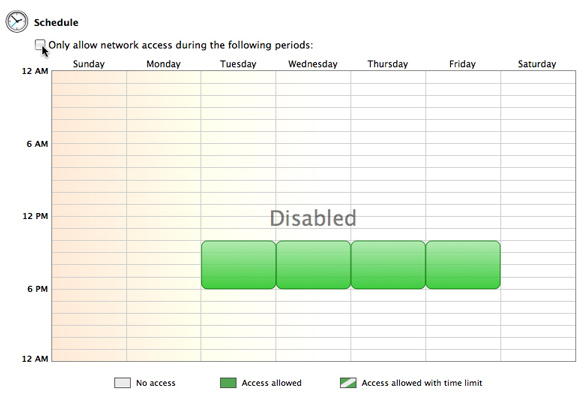
By default, all users are granted Internet access at all times. To restrict access to times you'll specify, click Only allow access during the following periods.
When you first see the timetable, all the cells are blank, representing that the selected user is not allowed to access the Internet at any time. To grant Internet access at given times, click the time cells in the timetable - each cell represents one hour. You can click individual cells, or you can click and drag to cover longer periods.
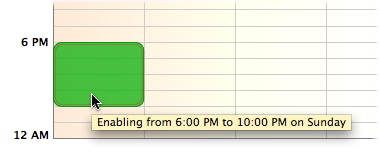
As you click cells, tooltips display showing the periods that you are enabling or disabling. You can allow or block access for any hour-long period on any day of the week in this manner.
If you wish to allow or block access to an entire day, or if you simply want to reset access for a day to change settings from scratch, you can click the name of a day. This resets the entire day to green, allowing access for that day. Click again to block access for that day.
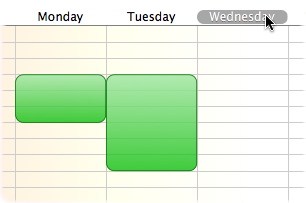
You can also click and drag in any direction to change cells. If, for example, you want to block access when a child comes home from school until suppertime, you would first enable all times, and then drag from 2pm on Monday to 6pm on Friday to disable those times.

A user attempting to connect to the Internet using a web browser during a forbidden period will see an alert:

However, attempts to connect to the Internet with other applications might not cause an alert to be displayed; in some cases, access will simply be blocked. Some applications will display their own alerts, saying that they could not connect to the Internet.
You can also allow Internet access for a limited period of time in between specific hours-for example, half an hour between 6pm and 9pm. To do so, first enable that time period by clicking and dragging to create a green access block; then, press the Control key while clicking that time period, and choose Add Time Limit….
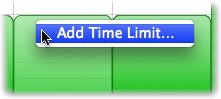
A dialog will appear, allowing you to set the amount of combined Internet access permitted during that period.
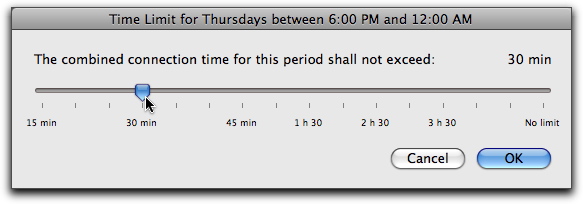
Drag the slider to the time limit you want to allow. After you click OK, your choice will appear as a striped green area on the time chart, specifying the amount of time allowed.
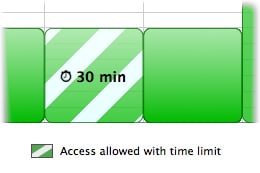
To change the amount of time available in a time limit, move the cursor over one of the sections with a time limit, hold down the Control key, and click. Choose Edit Time Limit… from the menu.
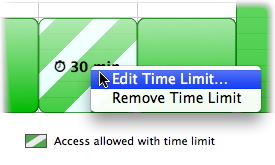
The time limit dialog displays again. Change the time limit by dragging the slider, then click OK to save your changes; alternately, click Cancel to keep the previous time limit.
To remove a time limit, move the cursor over one of the sections with a time limit, hold down the Control key, and click. Select Remove Time Limit from the menu. The time limit is removed.
When a user has a time limit, ContentBarrier automatically displays a small controller allowing them to start and stop their Internet access period. Since you may want your children to be able to use their Mac, but not the Internet, this allows them to control the periods when they can access the Internet. The controller looks like this:
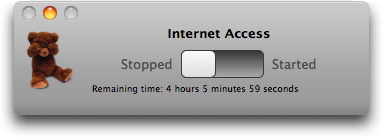
To start or stop a session, just drag the slider to Started or Stopped. Below the slider is the remaining time.
To remove the controller from the screen, you can click the yellow button; the controller is then minimized into the Dock. Clicking the controller's icon returns it to the screen so the user can start or stop their Internet access period.
To turn off all schedules and therefore allow Internet access at all times - with all of ContentBarrier's other filters in place, of course - uncheck the Only allow access during the following periods box. If you've set any schedules, the word "Disabled" will appear in the middle of the time grid as a warning that those schedules won't be in effect.
Application Filtering
ContentBarrier gives you the option of allowing users to only access the Internet with specific applications. Rather than filter web access by category, for example, you can prevent a user from using any web browser. You can choose which applications can access the Internet; all other applications are blocked. To set up application filtering, click the Applications button on the ContentBarrier button bar, then check Only allow the following applications to connect to the Internet.
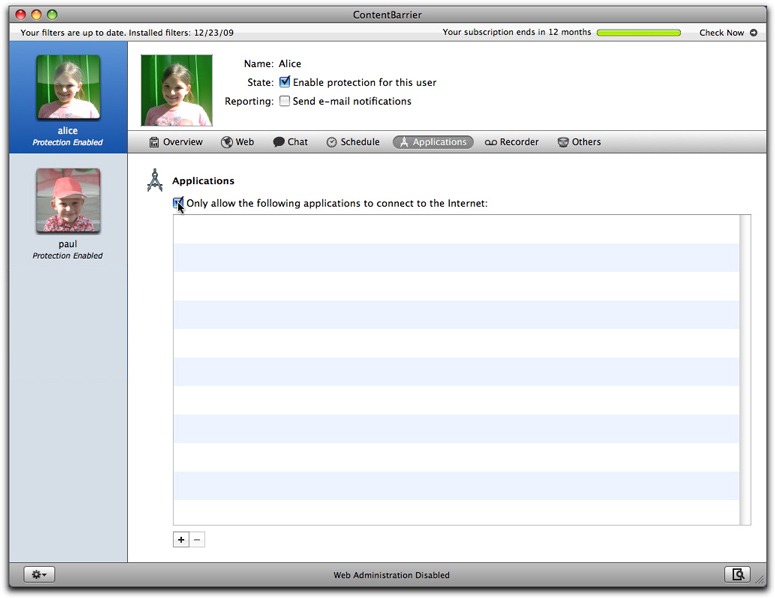
Application filtering will supersede all other ContentBarrier filtering rules. If, for example, you do not add a web browser to the application list, then web filtering will have no effect: all web sites will be inaccessible, as no program that accesses them is available. However, ContentBarrier's other filtering rules apply to all applications added to this list. So if you choose to allow a user to access the Internet with a web browser, then ContentBarrier's active web filtering categories will filter web sites visited.
To add applications to the list, click the + button and navigate to your Applications folder. You can also drag applications from a Finder window into this list. As you add applications, they display in the list.
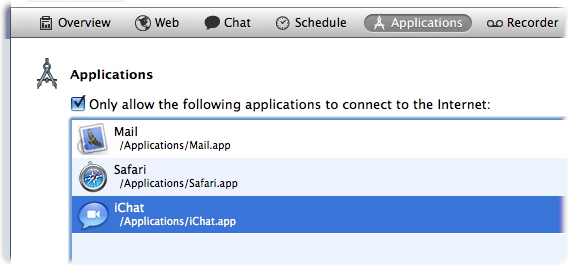
To remove an application from the list, click it to select it, then either click the - button or press the Delete key.
If, at any time, you want to stop using application filtering for a given user, simply click their name in the Users list, click the Applications button, then uncheck Only allow the following applications to connect to the Internet.
When ContentBarrier blocks an attempt to access the Internet by a non-approved application, it displays a warning. You can change this behavior in the Reporting preferences, as is described in the section, Setting Log Preferences.
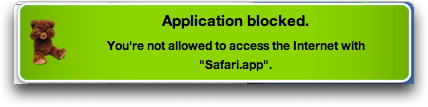
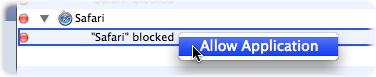
Note: some applications may use "helper" applications when they connect to the Internet. One example is Apple's iChat, which requires that iChatAgent access the Internet. If you add iChat to the list of allowed applications, this will not add iChatAgent. To add the latter helper application, go to your user's log, click Applications, then find which applications have been blocked. (There may be others.) Click the disclosure triangle next to an application or helper application you want to allow, then hold down the Control key and click on its name. A contextual menu displays with one option: Allow Application. Choose this and the application in question will be added to the list of allowed applications.
You may also want to check the logs from time to time; many applications that you might not expect need to connect to the Internet. Apple's Address Book, for example, makes an Internet connection, as does Help Viewer, the application that provides Mac OS X help. Your users will probably tell you which applications are blocked, but you can always see them, then allow them, from the log.
Recording Internet Usage
ContentBarrier lets you keep track of what your users have been doing by secretly taking pictures of what's on their screens and recording what they type into a hidden log. To access the Recording controls, click the Recorder button in ContentBarrier's button bar.
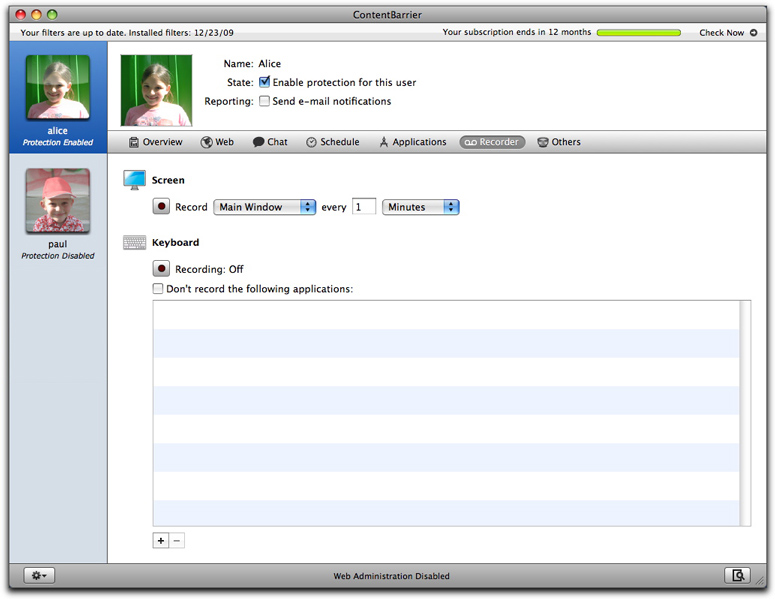
To turn on screen recording, click the Record button underneath Screen. ContentBarrier will then take a screenshot of either the Main Window, that is, the frontmost one, or of everything on the computer, including a second monitor, if one is connected, if you select All Screens from the popup menu. You can also decide how often these screenshots will be created, from one per minute to one per 999 hours. (One reason to direct ContentBarrier to take less-frequent screenshots is that a large number of graphics can take up a lot of hard disk space.)
To record all typing done by the selected user, click the Record button underneath Keyboard. You can then exempt the keyboard from being recorded in certain applications by checking the Don't record the following applications box and adding those applications to the list by either clicking the + button and navigating to them via the Mac OS X dialog box, or dragging and dropping the application from the Finder into the list. (Note that all text typed is recorded, with the exception of passwords typed into a standard password text field.)
You can see these graphics and text files created by these recordings by looking at ContentBarrier's log, as is described in the section, Using Logs.
Other Filtering Options
While chatting and web browsing are two of the most popular Internet activities, ContentBarrier also provides filtering for other types of Internet access. To adjust settings for these, click the Others button.
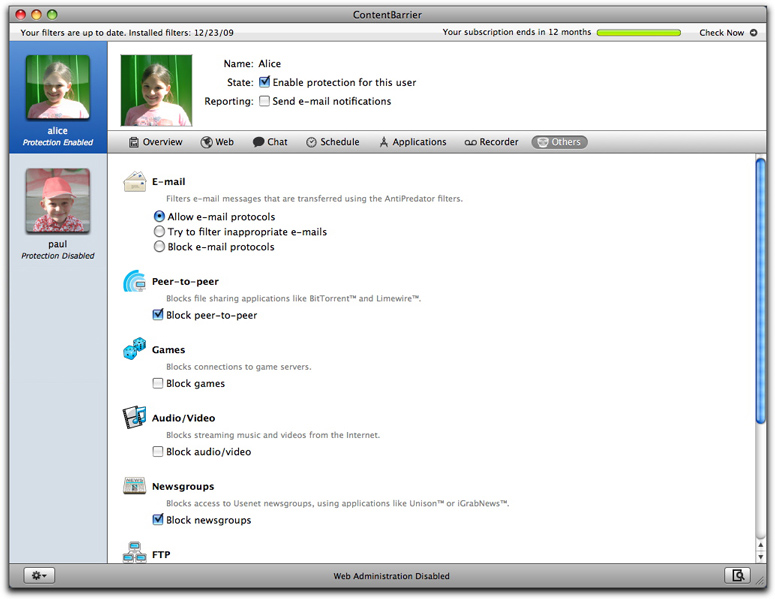
E-mail Filtering
ContentBarrier allows you to apply its built-in content filters to e-mail messages that are transferred through any e-mail program.
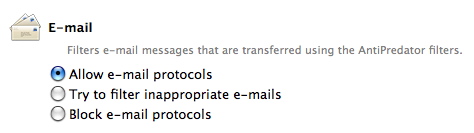
Your three options for e-mail filtering are:
- Allow e-mail protocols: all e-mail will be allowed through.
- Try to filter inappropriate e-mails: ContentBarrier will scrutinize the contents of incoming and outgoing e-mail and block those that it believes are dangerous. ContentBarrier uses the entire list of AntiPredator phrases for this filtering; even if you have only activated certain phrases in the Chat Filtering preferences, those choices do not affect e-mail filtering.
- Block e-mail protocols: forbids all e-mail from coming through standard e-mail programs. Note, however, that this setting will not affect e-mail delivered in other ways, for example on message boards or web sites.
Peer-to-Peer Filtering
ContentBarrier can filter peer-to-peer software, which is often used to share files over the Internet. To activate peer-to-peer filtering for a selected user, check the Block peer-to-peer box.
There are no options for peer-to-peer filtering; It is either active or inactive.
Game Filtering
ContentBarrier can filter common protocols used by online games such as World of Warcraft and Quake. To activate game filtering for the selected user, check the Block games box.
This setting will only block those games that access a server in a way that ContentBarrier can identify: standalone games and those played within a web page will not be affected.
There are no options for game filtering; It is either active or inactive.
Audio/Video Filtering
ContentBarrier can filter streaming audio and video, which is audio or video content that is played back live, rather than after downloading. To activate streaming filtering for a selected user, check the Block audio/video box.
There are no options for audio/video filtering; it is either active or inactive.
Newsgroup Filtering
ContentBarrier can filter Usenet newsgroups, which offer discussion forums using a specific protocol and software. To activate newsgroup filtering for a selected user, check the Block newsgroups box.
This setting will only block newsgroups that are accessed through such software, and will not affect those that are displayed on a web page. However, you can block those web sites by checking the Newsgroups category in the Web filtering screen. (For more information, see the section, Web Filtering.)

There are no options for newsgroup filtering; it is either active or inactive.
FTP Filtering
ContentBarrier can filter incoming or outgoing "file transfer protocol", or FTP, which is commonly used for exchanging files among computers. To activate FTP filtering for a selected user, check the Block FTP box.
This setting will only block file transfers that take place using FTP's default port 21 and SFTP's default port 22, either through an FTP program or through a web browser pointed at URLs that begin with "ftp://". It will not stop files transferred using other methods, such as HTTP download or peer-to-peer programs.
There are no options for FTP filtering; it is either active or inactive.
SSH Filtering
ContentBarrier can filter incoming or outgoing "secure shell", or SSH, which is commonly used for logging into remote computers. To activate SSH filtering for a selected user, check the Block SSH box. This setting will block communications that take place using SSH's default port 22.
There are no options for SSH filtering; it is either active or inactive.
Volume Filtering
ContentBarrier can stop your users from mounting external hard drives, iPods, USB thumb drives, CDs, DVDs or other volumes, thereby preventing them from introducing new software or content onto the computer via hardware that's directly connected to it. To activate Volume filtering for a selected user, check the Block volumes box.
There are no options for Volume filtering; it is either active or inactive.
Using Logs
ContentBarrier provides a complete log of all Internet activity for each user. To view the log, either:
- Choose Window > Log;
- Press Option-Command-L; or,
- Click the Logs button at the bottom-right of the main screen.

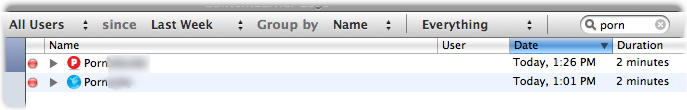
When you first open the Log, it shows a record of all users' Web access attempts for the past week.
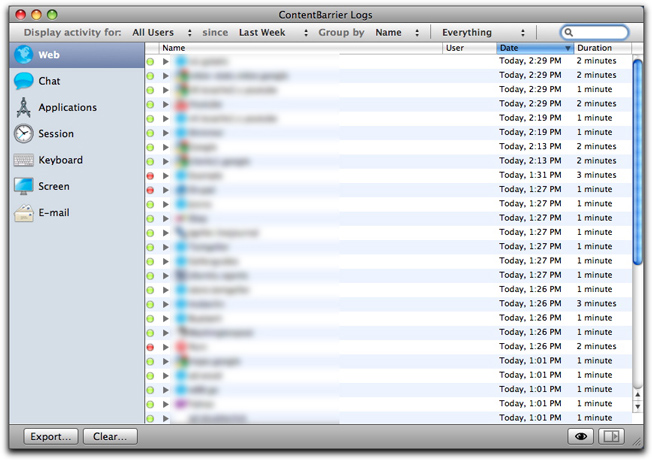
You can filter log entries by clicking the popup menus in the bar at the top of the window.

Criteria are:
- Display activity for: select the name of a specific user, or leave it on the default setting, All Users.
- since: choose from Last Week, Last Month, or Forever.
- Group by: makes ContentBarrier reorganize list entries according to user name or the date of attempted Internet access.
- Everything or Blocked Items: tells ContentBarrier to show all either all Internet access or only those that ContentBarrier has blocked.
You can also search for specific log entries by typing the desired text in the search box at the top of the window; as you type, all entries disappear except for those matching your search. To show all log entries again, click the "X" next to the search string.
Setting Log Preferences
Some of ContentBarrier's logging behavior is determined by settings in its preferences, which you access by choosing ContentBarrier > Preferences…, or by pressing Command-, and then by clicking the Reporting icon.
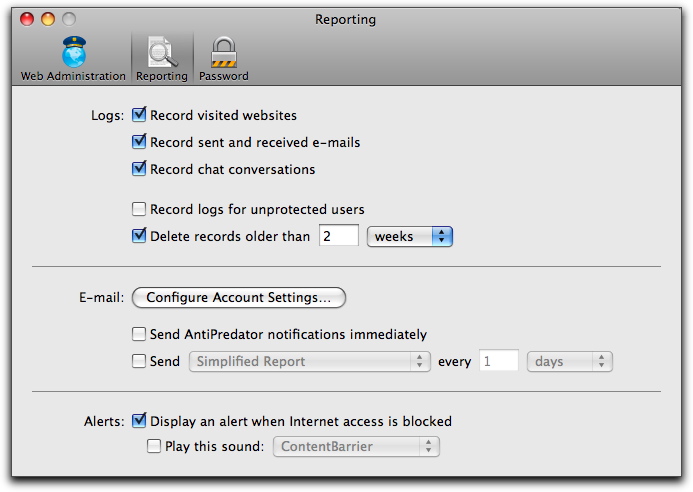
The options are:
- Record visited websites: if this is checked, ContentBarrier keeps a list of all visited websites in its log. Otherwise, ContentBarrier only records those websites that are blocked or filtered.
- Record sent and received e-mails: records all e-mails sent and received by users.
- Record chat conversations: records all chats and instant message conversations.
- Record logs for unprotected users: keeps track of Internet usage by users whose access isn't restricted in any way. By default this is turned off.
- Delete records older than…: allows you to throw away logs beyond a certain age to preserve hard drive space or improve security. By default, logs are kept for two weeks.
- E-mail: the Configure Account Settings… button brings up a window in which you specify where you'd like e-mailed reports to be sent.
- Send AntiPredator notifications immediately: if you check this, ContentBarrier will send you an e-mail whenever it detects "predatory" text strings in chat.
- Send reports: when checked, you'll receive a report of the type specified periodically, with the frequency you specify.
- Alerts: these two checkboxes let you determine whether users are alerted of blocked access with a floating alert, a sound, or both. (Users are also alerted to ContentBarrier's activity by being redirected when they attempt to access a forbidden web site.
Viewing Logs
The Log window's left-hand column lists types of log entries: Web, Chat, Applications, Session, Keyboard, Screen, and E-mail.
Clicking any of these log types displays only those entries. For example, clicking Session tells you of times when your user attempted to use the Internet, while Applications tells you which programs attempted to connect to the Internet.
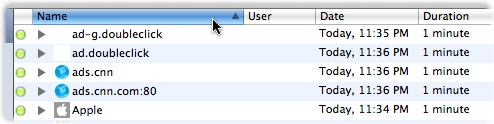
Each line in the Log contains five different pieces of information: a colored icon, a disclosure triangle, the Name of the site attempted, the User who attempted to access that site, the Date of the attempted access, and the Duration of the visit.
Icons are either green (showing successful Internet access attempts) or red (showing attempts that were blocked). Red icons do not necessarily indicate that an entire page was blocked; they may display when parts of a page were blocked.

- Name refers to the domain of the site attempted (for web sites), without anything after the first "/". To the left of the name is a disclosure triangle that you click to expose the specific pages on a given domain that one of your users attempted to reach. For example, if a user tried to reach both http://www.example.com/index.html and http://www.example.com/games/shootemup, both pages will appear grouped under example.com. These individual items are called Log entries.
- User shows who attempted to access the Internet. User names display after you click a disclosure triangle to display the different parts of a web site that were accessed or blocked.
- Date shows the date, relative to today, that the most-recent attempt occurred.
- Duration shows how long this Internet access attempt lasted.
By default, log entries are sorted according to the last attempted access. You can re-sort the log according to any of the five criteria by clicking the appropriate header at the top of the column. Click again, and the column re-sorts in the opposite order.
You can preview log entry in several ways:
- Double-click a log entry;
- Choose a log entry by clicking it once, then press the space bar; or,
- Choose a log entry, then click the Quick Look button at the Log window's bottom right.

ContentBarrier will connect to the Internet to show you what the web page looks like. This preview is "live" - that is, you see the page as it exists right now.
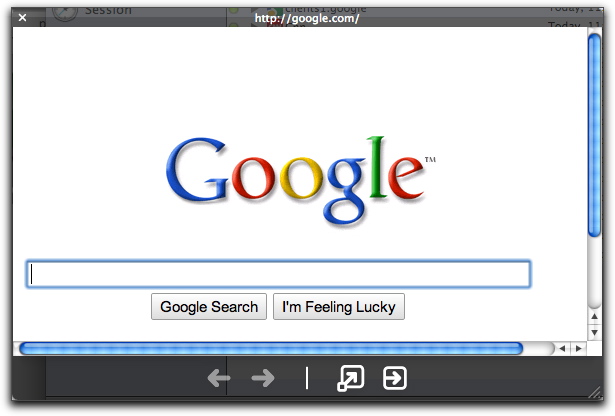
It is possible, at times, that a web site might not be available; if so, double-clicking will not display the site. Also, some of the elements of a web page are merely parts of a page, and will display as such.
The icons at the bottom of this window control how you see these previews. They are:
- Left arrow: go to the previous entry.
- Right arrow: go to the next entry.
- Vertical line: a visual separator-does nothing.
- Diagonal arrow in a box: view the entry as a full-screen image. (Press the Escape key to dismiss the full-screen image.)
- Right arrow in a box: export the image or text to a file.
You can dismiss this window at any time by either clicking the "X" in its upper-left corner, or by pressing the Escape key.
Clicking a disclosure triangle next to an application's name lets you view specific, individual entries in a popup window as described above, and with the same controls.
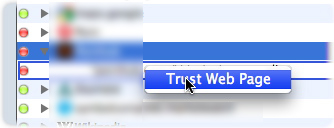
When viewing log entries for web sites, you can quickly allow or block web sites that are listed in the log by holding down the Control key and clicking a log entry. Select Trust Web Page or Block Web Page from the contextual menu that displays, and ContentBarrier adds that site to the list of allowed or blocked sites.
Similarly, you can allow a blocked application to access the Internet by clicking its log entry while pressing the Control key, and then choosing Allow Application.
Keyboard and Screen Logs
Two of the Log entry types - Keyboard and Screen - have extra information to help you see how your users have accessed the Internet. For the Log to track such entries, you must first turn on screen and/or keyboard recording: see the section, Recording Internet Usage for further information. (Note that all text typed is recorded, with the exception of passwords typed into a standard password text field.)
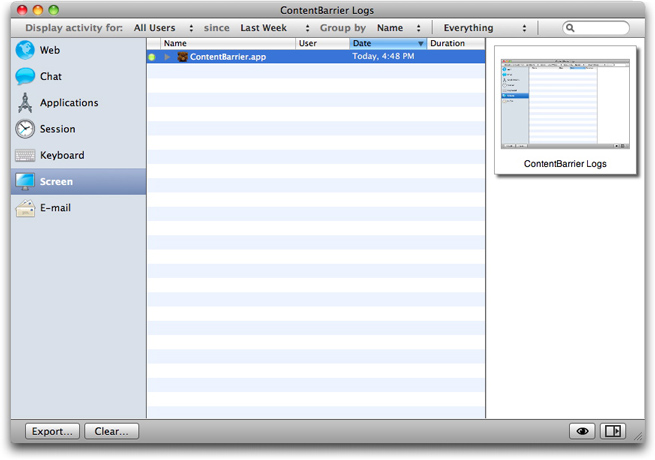
Keyboard and Screen Log entries are grouped according to the application being used so, for example, all text typed into Microsoft Word appears under a "Microsoft Word" listing. Clicking the name of any application shows you all the activity that occurred while that application was being used in the right column. You can hide this column at any time by clicking the bottom-right button.

As with other log entries, you can see a visual snapshot of the user's actions by double-clicking an application, or selecting it and then clicking the Quick Look icon in the bottom right corner. A quick look window appears, letting you page through all screen shots or keyboard captures made while that application was being used.
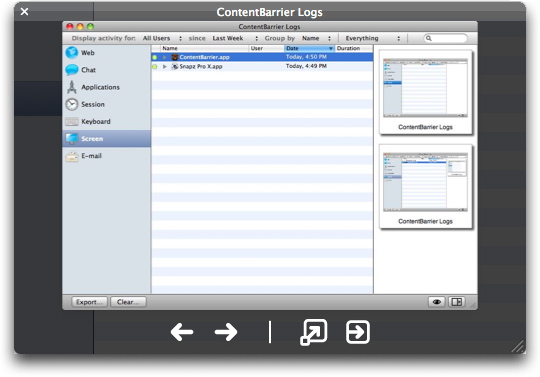
Exporting Log Reports
You can export ContentBarrier logs as HTML files to view them later in a web browser, or as text files. To do so, select one or several log categories (Web, Chat, Applications, etc.), then click the Export… button at the bottom left of the Log window. A sheet displays where you choose a name for the log, a location to save the file, and the format.
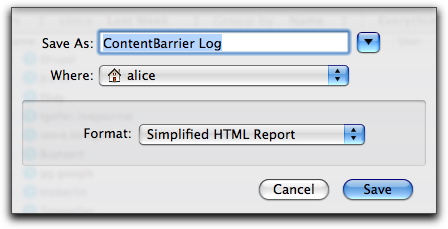
ContentBarrier lets you choose from three types of reports when you export logs. They are:
- Simplified HTML Report: shows global elements from the selected categories; what you see before clicking a disclosure triangle. For example, for web sites, only the name of the site is shown, not the actual URLs of pages visited or blocked. For keystroke recording, only the name of the application is shown, and not the actual text recorded.
- Complete HTML Report: shows all ContentBarrier activity in detail. All selected categories show all activity.
- Complete Plain Text Report: shows the same information as the Complete HTML Report, but in a format that's useful for further analysis (in, for example, a spreadsheet or custom-programmed application).
Click Save to export the log in the selected format.
To erase all information stored in the log for all users, click the Clear… button at the bottom of the Log window.