Recommended + Security & Privacy + Security News
Apple Criticised for Not Patching OS X Yosemite Zero-Day Vulnerability
Posted on
by
Graham Cluley

A German security researcher, Stefan Esser, has published details of a zero-day vulnerability in OS X that could allow a malicious hacker to escalate their privileges, opening opportunities for them to hijack complete control of innocent users’ Macs.
And despite releasing the details of this latest OS X security hole without informing Apple beforehand, Esser seems to have no regrets.
To be nerdy for a second, the security flaw appears to lie in new features introduced in OS X Yosemite and the upcoming OS X El Capitan, and relate to how Apple altered its dynamic linker code in OS X 10.10 to support the new DYLD_PRINT_TO_FILE environment variable.
Whilst not considered as critical as remote code execution vulnerabilities, privilege escalation bugs are still serious — a malicious hacker who has already broken into a computer system can use the exploit to give themselves system-level powers.
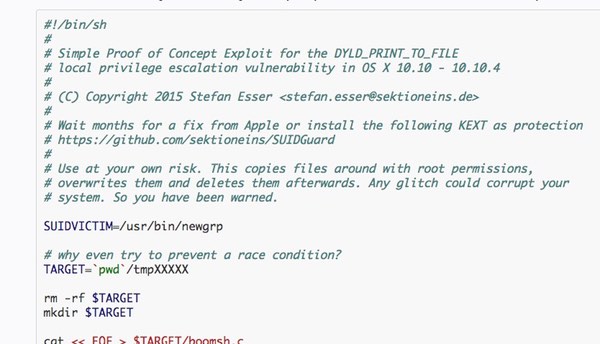
Esser published full details of the security hole, including proof-of-concept exploit code, on his blog.
The proof-of-concept code Esser has published is, he warns, dangerous because it installs a root shell onto Mac computers. For understandable reasons, we won’t link directly to it from this article.
Stefan Esser works for security audit firm SektionEins, and has previously found numerous software vulnerabilities, as well as analysing the so-called “UnFlod Baby Panda” malware that targeted jailbroken iPhones and iPads.

But what has really helped give Stefan Esser — also known as i0n1c — a name for himself are the flaws he has found in Apple’s software, and his low opinion of the quality of Apple security.
I think it would be fair to say that Apple and Esser have a frosty relationship.
Just take a glance at the posts Esser made on his his Twitter account after he announced the flaw if you don’t believe me:
“Imagine how much money one could make if Apple cared about security and paid bug bounties…”
“No need to smoke pipes to get root on OS X”
“Same exploit should work btw on *jailbroken* iOS 8 iPhones to get root from mobile user.”
“Of course there are the usual comments like: “why didn’t you contact Apple?” – feel free to work for free and do it yourself.”
Esser’s full disclosure certainly isn’t popular with everyone, including participants in a Reddit thread about his publishing of the flaw.
Take this response, for instance, from Reddit’s yepthatguy2:
It’s not about Apple. It’s about people who happen to use Apple’s products. The publication of this vulnerability doesn’t hurt Apple (much). It mostly just hurts users.
And if your answer is “That’s your fault for using Apple’s products”, then please direct me to the computer system that has zero security holes.
Meanwhile, back on Twitter, Esser proved himself to be unrepentant when quizzed about why he hadn’t emailed Apple’s security team about the flaw:
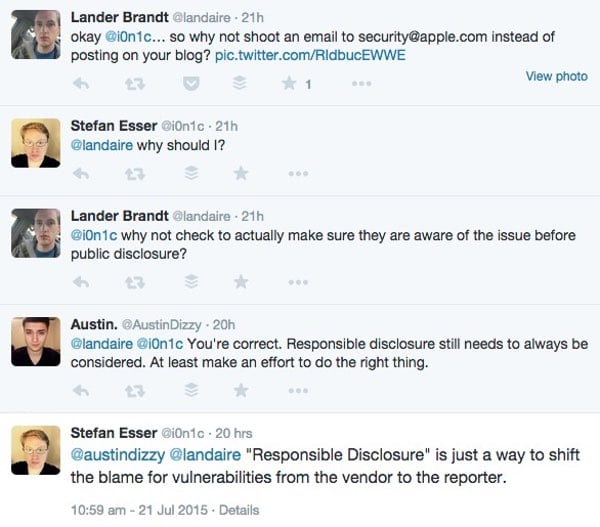
 But what has really got the security researcher’s goat is the discovery that the beta version of Apple’s upcoming version of OS X, El Capitan, does *not* have the same bug.
But what has really got the security researcher’s goat is the discovery that the beta version of Apple’s upcoming version of OS X, El Capitan, does *not* have the same bug.
In Esser’s view, this is a sign of the company’s irresponsible behaviour — working on a vulnerability fix that was shipped with the El Capitan beta in June, but apparently not bothering to backport it for the latest official version of OS X.
So Apple was informed about said bug months ago and as usual did the irresponsible to fix it for some beta half a year in the future only.
Apple is indeed worse than Adobe.
So Apple has working fix + released it in June with El Capitan beta, but did not backport. Has intention to fix in September.
To mitigate the threat, Esser’s firm SektionEins has released a kernel extension that protects computers by “stopping all DYLD_ environment variables form being recognized by the dynamic linker for SUID root binaries.”
The source code of that tool can be downloaded from GitHub.
I guess we should be grateful that, at the very least, an unofficial fix has been in released alongside details of how to exploit the flaw — but it’s clear that the vast majority of Mac users will not use it.
Let’s all hope that Apple responds appropriately, with a security update for all affected OS X users. And yes, I mean those of us using the latest version of OS X Yosemite.
Was Stefan Esser and his company SektionEins right to publish details of the vulnerability without informing Apple privately first? Would a co-ordinated disclosure of the flaw have been safer for the Apple community? Or is Esser performing a valuable service that keeps Apple’s engineers on their toes?
Leave a comment with your point of view below.