Malware + Recommended + Security News
WireLurker Malware Infects Macs, Attacks Non-Jailbroken iPhones
Posted on
by
Derek Erwin
The handwriting is on the wall and it’s been there for many years now. Apple devices and Macs can get malware, just like any other machine. There. Somebody had to say it.
For a while now, people have felt a sense of security because they’re on an operating system that doesn’t inspire hundreds of thousands of new malware attacks per day. But the total number of malicious threats crawling around the Internet waiting to infect your Mac is less important than this simple fact: It only takes one to ruin your day.
Virus hunters have uncovered a new family of Mac malware, called “WireLurker,” which they say has infected hundreds of thousands of Apple devices already.
WireLurker malware affects Apple devices and attacks iOS devices as well—and here’s the kicker: This is the first malware that can infect iPhones that have not been jailbroken.
Before we go any further, let’s cut to the chase: No, you aren’t at risk of infecting your Mac or iOS device with this current malware—unless you do some really risky things (see “What Apple users do to get infected by WireLurker” section below). This malware depends on you personally bypassing a whole bunch of built-in security contained in both Macs and iOS devices. In some ways this is akin to having 15 deadbolts on the front door of your house yet leaving the door wide open when you leave for work.
How WireLurker attacks non-jailbroken iPhones
WireLurker can install third-party applications on non-jailbroken iPhones and can attack iOS devices through Mac OS X computers by way of USB connections or USB cables, according to security researchers at Palo Alto Networks:
“WireLurker was used to trojanize 467 OS X applications on the Maiyadi App Store, a third-party Mac application store in China. In the past six months, these 467 infected applications were downloaded over 356,104 times and may have impacted hundreds of thousands of users.”
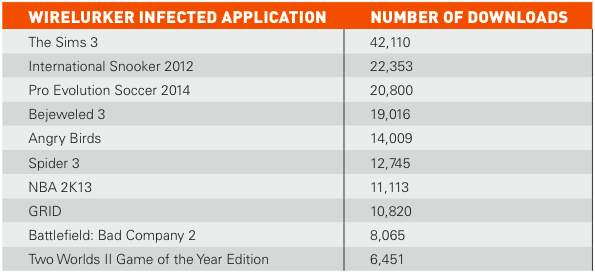
Image credit: Palo Alto Networks
Once computers are infected, WireLurker spreads to non-jailbroken iOS devices that connect to the Mac over USB, rewriting existing programs on the device through binary file replacement. The malware uses a popular library called libimobiledevice to interact with iOS devices through USB connections. “This third-party open source software library implements the iTunes protocol stack for communication between a computer and iOS device,” according to the researchers white paper.
Everything I've read so far in the WireLurker white paper seems not only completely plausible, but easy to pull off with libimobiledevice.
— Jonathan Zdziarski (@JZdziarski) November 6, 2014
Is WireLurker malware a high-risk threat?
While the malware has been in the wild for the better part of the last half-year and is only gaining attention now, reports have made the threat sound particularly scary. But are you at risk of infection?
Apple reported this morning that they have effectively blocked the infected applications targeting users in China.
“We are aware of malicious software available from a download site aimed at users in China, and we’ve blocked the identified apps to prevent them from launching,” Apple said in an email to Reuters.
Without more details, what this likely means is that Apple has stopped accepting that specific unsigned, untrusted certificate. It’s a simple thing for them to do, and they probably don’t even have to roll out an OS X update to do it.
The next time an infected iPhone checks in, that certificate gets added to the list of blocked certificates. This is part of Apple’s standard process to avoid companies from selling and distributing apps outside the App Store. By turning off the certificate, that specific problem goes away.
That being said, the developer of WireLurker malware can probably create another, but they will need an enterprise account to do so, which takes a few more jumps, and the enterprise account that created the previous certificate has probably been disabled as well. Our conclusion is that Apple plugged this particular exploit, but it’s doubtful that they closed the hole. It’s very likely that Apple is working on closing the hole with whatever security update comes out next.
How can you know if your Mac/iPhone is infected?
While the payload for WireLurker appears to have changed several times so far, you can search for the following files/directories on your Mac to determine whether or not you may be infected:
- /Library/LaunchDaemons/com.apple.globalupdate.plist
- /Library/LaunchDaemons/com.apple.machook_damon.plist
- /usr/bin/globalupdate
- /usr/local/machook (This directory is created by the malware and may possibly contain copies of the files that were copied to the other above directories.)
So a good question at this point is what can you do if you’re infected?
After analyzing the malware, following is our guide explaining what actions Apple users must take in order to get infected, and what to do if WireLurker infects your computer.
What Apple users do to get infected by WireLurker
Fortunately, unless you do some very risky things, WireLurker is a low risk threat and there isn’t much to worry about. So what are the risky things you have to do?
Step 1: Download an installer containing the trojan from the Malyadi App Store, a third-party Mac application store in China. While there have been hundreds of files infected at the Maiyadi App Store that have been downloaded hundreds of thousands of times, all of the files have turned out to be pirated copies of other apps.
Prevention Step 1: We cannot stress enough the dangers of installing pirated software and apps—WireLurker infections are the consequences of risky behavior. Your best method to prevent infection is to not download pirated apps from App stores located in other parts of the world, especially from countries dealing with a high volume of malware.
Step 2: Launch the infected installer/application you downloaded from the Malyadi App Store.
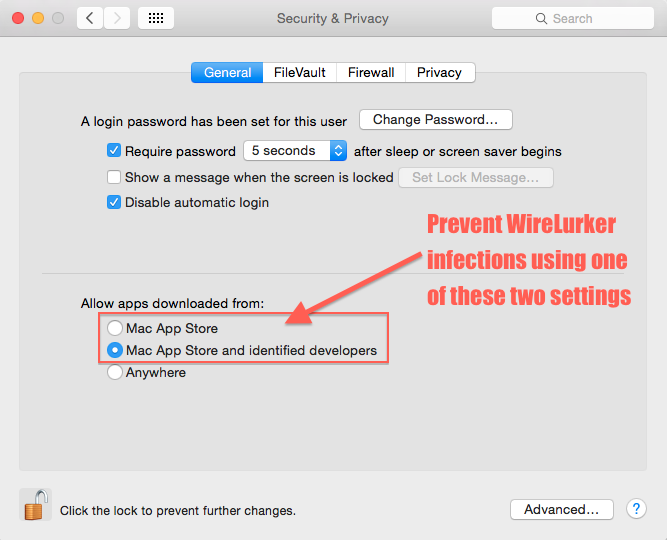
Prevention Step 2: Go to System Preferences > Security & Privacy (General tab). Make sure “Allow applications downloaded from:” is set to “Mac App Store” or “Mac App Store and identified developers.” None of the infected files pass either of these steps, so Mac OS X won’t let you run them without explicitly bypassing this security measure, something you should never do.
Step 3: Attach your iOS device to the infected Mac via the USB to Lightning connector (or the older USB to Apple 30 Pin connector). Unlock your iPhone, and set it to trust this new computer.
Prevention Step 3: Don’t connect your iOS device to a computer via USB that you bypassed step 2 on.
At this point, the iOS device can be mounted on the Mac, and any malware that is running on the Mac has access to certain files on your iOS device. If in step 2 you entered your Administrator Username & Password giving the WireLurker root access, then the malware has even more access to files on your iOS device. And if you do development and your iOS device is paired to the computer in development mode, the computer has even more access.
Now this is where WireLurker starts to get interesting. If the malware is running on a Mac that you use iTunes to sync to the iOS device with, and apps that you have on your iPhone are also on your computer, WireLurker will modify the application stored on the Mac and try to send the app back to the iOS device.
At this point, however, the malware infected application is still useless since its signature no longer matches the signature download from the Mac App Store, so there is no way to run the app on your iOS device.
Step 4: On your iOS device, accept the install of the unsigned (hence unknown) provisioning profile. The only way WireLurker can run on your iOS device is to accept this profile.
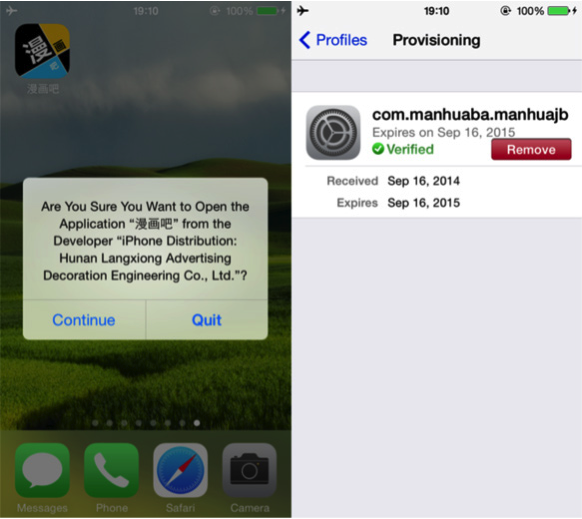
Image credit: Palo Alto Networks
Prevention Step 4: There’s a simple way to prevent this: Don’t accept random provisioning profiles that show up on your iDevice for no apparent reason. Any questions?
Now, assuming you have been putting yourself at greater risk of infection through step 4, the only data WireLurker has access to at the moment is data stored within the infected application. In other words, if Pages is infected, it has access only to the Pages data. It’s impossible for the malware to get beyond the app sandbox without doing another risky thing, which we explain in step 5.
Step 5: Allow the infected application to have access to your Camera, Contacts, Location, and other areas is dangerous. If all of a sudden an application you have been using for a while starts asking to access all sorts of information that it doesn’t need—or even requesting for information it used to have access to, but now seemingly doesn’t (because the infected app is actually not the same one you’ve used for a while, it wants you to re-grant all previous permissions that the real app has)—it should signal red flags with you.
Prevention Step 5: If an app starts popping up a whole bunch of requests that you’ve either seen before or don’t understand why the app needs the information, stop. Ask yourself if something has changed recently (like a major iOS update). If not, go into your iPhone Settings > Privacy and check if the app that you think you’re running already has the access it’s asking for. If it does, something is wrong; queue the red flags. If it doesn’t, then, well, something may have changed and if you want the app to have access go ahead and allow it.
Again, at this point, the WireLurker malware is limited to access data in the app, and in your Address Book and Camera Roll. Plus, the application can also access your current location.
Step 6: If you’re still with us here, and none of the red flags have set off for you so far, you can use the new to iOS 8 extensions mechanism, or iCloud Drive, and from within the app, find and open a file other then the files inside the app itself. The malware now has access to that document as well (and only that document).
Prevention Step 6: If there are red flags going off in your head, don’t use an application to open documents that the app wouldn’t otherwise have access to.
For those who are engaging in risky online behavior, it is important to note that even though you have gotten this far—installing and running the malware on your iOS device, thus getting infected with WireLurker—the malware still only has access to data that the real app would have access to. Apple’s sandboxing that makes iOS so secure in the first place is still fully intact. The only reason you have malware running on your iOS device is because you’ve gone out of your way to help the malware get there.
Now, unfortunately once the malware is there, there is no way for any app (like VirusBarrier iOS) to scan and find the malware, because the same sandboxing that is preventing the malware from spreading or doing any real damage also prevents third parties from scanning the iOS device to look for malware.
So, if you’re infected, what can you do to undo the mess you’ve created?
How to mitigate the WireLurker threat
Metaphorically, you should just stop leaving your front door open and start using the deadbolts. In a more straightforward approach, there are four steps you can take to mitigate the WireLurker threat, and they are as follows:
- On your iPhone, go into Settings > General > Profiles. If you see something there that shouldn’t be there, remove it. Once the profile is removed, the malware can’t run on your iOS device anymore. Note that some enterprises actually install real signed profiles there, so just because you see a profile there, it isn’t necessarily a bad thing. But if you see a profile there with red text in it, beware.
- Any apps that no longer launch on your iOS device, delete. Then re-download them directly from the App Store on your device. This deletes the bad code.
- Scan your Mac for potential viruses and malware using robust Mac anti-virus software like Intego VirusBarrier. This will eradicate the malware from the Mac and prevent further re-infection of your iOS device.
- Don’t attach your iOS device via a USB cable to a computer that you perform risky behavior on. An infected computer (Mac OS X or Windows) that you attach an iOS device to via USB can get access to data on that device. Of course, the data has probably already been compromised as the malware on your computer has access to pretty much everything on your computer, but that’s another issue. Simply don’t practice unprotected syncing.
So there you have it. A step by step guide showing how to give yourself a nasty case of the WireLurker malware, and what to do if you were risky enough to get infected.
Intego VirusBarrier with up-to-date virus definitions detects this Mac and iOS malware as OSX/WireLurker and iOS/WireLurker.