What is BlueBorne? An Apple Device FAQ
Posted on
by
Joshua Long

From the number of inquiries Intego has received throughout the past week, it’s evident that “BlueBorne” is something of concern for a lot of users of Apple products.
Let’s start with briefly explaining what BlueBorne is, and then delve into how it might affect you and your Apple devices.
What is BlueBorne?
Armis, a company focused on Internet of Things (IoT) security, recently published a site and a white paper detailing eight Bluetooth-related vulnerabilities that they collectively call “BlueBorne.”
The name BlueBorne is a portmanteau of the words Bluetooth and airborne, because BlueBorne attacks are wireless by nature.
 Armis claims in their press release that “nearly all devices with Bluetooth capabilities, including smartphones, … laptops, watches, smart TVs, and even some automobile audio systems, are vulnerable to this attack.”
Armis claims in their press release that “nearly all devices with Bluetooth capabilities, including smartphones, … laptops, watches, smart TVs, and even some automobile audio systems, are vulnerable to this attack.”
Bluetooth pairing and discoverability mode are not required by the attack.
The company claims that, if exploited, BlueBorne vulnerabilities could make it possible for an attacker to do such nefarious things as take complete control of affected devices, steal data in transit, and spread malware.
And here’s the kicker: all of this can be done without requiring any user interaction.
Because such an attack can be carried out surreptitiously, affected users may have no idea that their Bluetooth-enabled systems have been compromised by an attacker.
Which Apple devices are affected?
The following Apple products are specifically called out by Armis as being vulnerable to BlueBorne attacks:
- All iPhone, iPad, and iPod touch devices with iOS 9.3.5 or earlier
- All Apple TV devices with version 7.2.2 or earlier
![]()
All devices still running the outdated iOS 9 are affected.
Note that not all versions of Apple hardware can run a more current version of their respective operating systems.
In particular, the following Apple products (and older versions) cannot be upgraded to an operating system version that protects against BlueBorne attacks:
- iPhone 4S and older
- iPad (3rd generation) and older
- iPad mini (1st generation) and older
- iPod touch (5th generation) and older
- Apple TV (3rd generation) and older
According to the Armis report, iOS 10 and later are not susceptible to the BlueBorne vulnerabilities. Therefore if you have a newer device than the ones listed above, you’ll need to make sure you’ve updated to the highest version of the operating system that your device supports.
You can go to the Settings app on your device to check whether an operating system update is available. On iOS devices, tap on Settings, then General, then Software Update. (To see what version of iOS you currently have, you can tap on About instead of Software Update.)
(Keep in mind that many devices from other manufacturers, including devices running Android, Windows, or Linux operating systems—including Samsung devices such as their Gear S3 smart watch and their Family Hub smart refrigerator—are also affected. For non-Apple devices that may be affected, check with the manufacturer to see if an update is available.)
Are Macs affected? What about Apple Watch?
We noted that Armis made no public mention of Mac or macOS, or Apple Watch or watchOS, in their reports, so we reached out to them for comment. They responded:
“At this time, Armis has not identified any macOS that are vulnerable to BlueBorne.”
They also commented that “watchOS is not vulnerable at this time,” with the caveat that they needed to confirm with their researchers whether previous versions of watchOS were exposed.
 ✅ Apple Watch and Mac are not known to be vulnerable to BlueBorne. Image: AlexBor
✅ Apple Watch and Mac are not known to be vulnerable to BlueBorne. Image: AlexBor
My Apple product is on your list of vulnerable devices! ? What can I do?
If you don’t use Bluetooth, you can mitigate the BlueBorne vulnerabilities by turning off the Bluetooth radio on your affected Apple device. This can be done via the Settings app. Once your device indicates that Bluetooth is off, you’re protected from BlueBorne.
However, if your hardware is so old that you can’t upgrade to iOS 11 or tvOS 11, that means your device is susceptible to quite a few more unpatched vulnerabilities than BlueBorne alone; merely turning off Bluetooth won’t protect you from many other dangerous vulnerabilities.
You should strongly consider upgrading to newer hardware that is capable of running iOS 11 or tvOS 11, of which the bare minimum includes:
- iPhone 5S or later (including iPhone SE; note that iPhone 5C is not compatible)
- iPad Air (1st generation) or later
- iPad mini 2 or later
- iPod touch (6th generation)
- Apple TV (4th generation) or later
![]()
If you have a compatible device, upgrade to iOS 11.
So if I’m running iOS 10 or later, is it okay to leave Bluetooth enabled even when I’m not using it?
Sure, you can… if you trust Bluetooth.
Armis, however, warns that although iOS 10 and iOS 11 are not vulnerable to the BlueBorne attack, they believe “many more vulnerabilities await discovery in the various platforms using Bluetooth.”
Other security professionals including Steve Gibson have long cautioned to turn off any wireless radios that you don’t actively use. Gibson has noted that Apple has a habit of reenabling Bluetooth after every major and minor iOS upgrade, even if the user has explicitly turned it off.
Our advice?
If you don’t use Bluetooth at all, you might as well leave it off, and after each iOS update make sure to turn it off again.
If you do use Bluetooth on a regular basis, consider turning it off whenever you’re not using it; it’s fairly easy to turn it off and back on.
Well, at least it used to be.
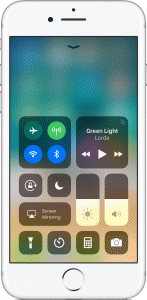 As of iOS 11, you can’t truly turn off Bluetooth by swiping up anymore. Image: Apple
As of iOS 11, you can’t truly turn off Bluetooth by swiping up anymore. Image: Apple
Take caution if you’ve upgraded to iOS 11, because when you attempt to disable Bluetooth or Wi-Fi from the new Control Center by swiping up from the bottom of the screen, it doesn’t actually turn the radios off.
Apparently, according to Vice’s Motherboard blog, Apple sees this as a feature, not a bug.
If you really want the radios off, you now have to disable Bluetooth or Wi-Fi from the Settings app.