Malware + Recommended + Security News
Ventir Trojan Intercepts Keystrokes from Mac OS X Computers
Posted on
by
Derek Erwin
Intego has seen an eyebrow-raising upward trend in the number of malicious files discovered targeting Mac OS X in the past few years, and it has many security experts concerned. Virus hunters have unveiled yet another modular malware for Mac OS X, called the Ventir Trojan.
Ventir uses a dropper program (e.g. Trojan horse) that can leave a backdoor, a keylogger and other malicious files behind on an infected Mac. These can be used for spying and stealing information from the victim’s Mac.
We currently do not know how the malware is distributed. Ventir is a Trojan horse, so it’s likely being picked up when downloading pirated software from peer-to-peer websites, such as BitTorrent.
The primary feature of Ventir is that it integrates a legitimate component for intercepting keystrokes that is freely available on code sharing websites.
Infection Vector
The keystroke logger makes use of an open source software package freely available from GitHub, called LogKext. Given the recent scares about hacked accounts, the thought of software that watches what you type and sends it to the bad guys is particularly unnerving.
LogKext has three files that function to intercept keystrokes (updated.kext), match the codes of the keys pressed by the victim to the characters associated with these codes (Keymap.plist), and log the keystrokes along with some system events (EventMonitor agent).
Fortunately, LogKext hooks on to the OS X kernel only if the dropper is successful in obtaining elevated privilges to the victims Mac.
It’s also worth noting that some of the keylogger components (Keymap.plist and updated.kext) are previously detected by Intego VirusBarrier as OSX/logKext.E and OSX/logKext.D.
How it installs on Mac OS X computers
The Ventir Tojan is delivered through a dropper that, when launched, checks whether it has root access to the machine—this is critical because that affects where the malware can install itself.
The result of the check for root access determines how much Ventir can run and the path where the Trojan’s files will be installed on the victims Mac.
Where Ventir installs files
It’s important to distinguish the two install directories: /Library/.local and ~/Library/.local (“~” stands for the path to the current user’s home directory). The malware will install to the home directory if the installer does not have root access.
With root access
If it has root access, the Trojan’s files will be installed in /Library/.local and /Library/LaunchDaemons. The Ventir malware downloads additional backdoor components if it has full privileges to the victims Mac.
Without root access
If it does not have root access, the files will be installed in ~/Library/.local and ~/Library/LaunchAgents. The EventMonitor spying component is downloaded to the affected machine only if elevated privileges are not obtained.
“All files of the Trojan to be downloaded to the victim machine are initially located in the ‘__data’ section of the dropper file,” wrote Mikhail Kuzin over at Securelist.
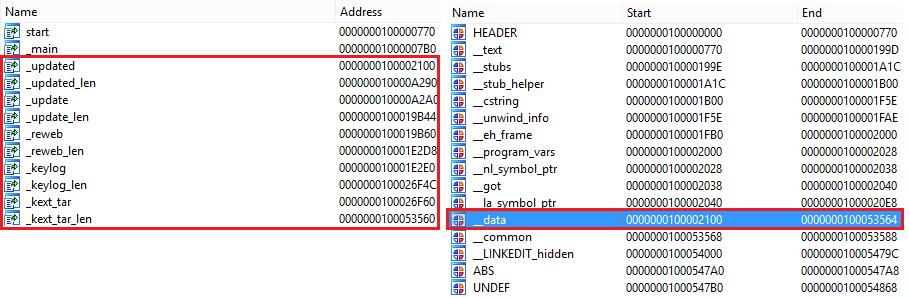
Image credit: Securelist
After the dropper determines where the Trojan’s files will be installed, it hides the following files on the infected machine:
- Library/.local/updated – re-launches files update and EventMonitor in the event of unexpected termination.
- Library/.local/reweb – used to re-launch the file updated.
- Library/.local/update – the backdoor module.
- Library/.local/libweb.db – the malicious program’s database file. Initially contains the Trojan’s global settings, such as the C&C address.
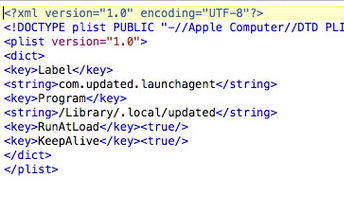
- Library/LaunchAgents (or LaunchDaemons)/com.updated.launchagent.plist – the properties file used to set the file Library/.local/updated to autorun using the launchd daemon.
- Depending on whether root access is available:
- A) If it is – /Library/.local/kext.tar. The following files are extracted from the archive:
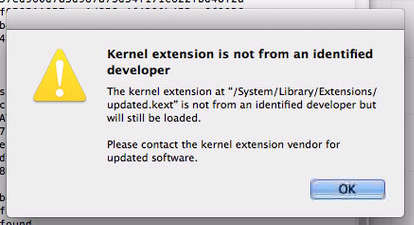
- updated.kext – the driver that intercepts user keystrokes. This is installed at /System/Library/Extensions/updated.kext. There is a good chance the user will see a popup for this when it’s installed.
- A) If it is – /Library/.local/kext.tar. The following files are extracted from the archive:
- Keymap.plist – the map which matches the codes of the keys pressed by the user to the characters associated with these codes. This is installed to /Library/.local, and users may see a popup when it’s installed.
- EventMonitor – the agent which logs keystrokes as well as certain system events to the following file: Library/.local/.logfile. This is installed to /Library/.local, and users may see a popup when it’s installed.
- B) If it isn’t – ~/Library/.local/EventMonitor. This is the agent that logs the current active window name and the keystrokes to the following file: Library/.local/.logfile
How to check if you are infected
Checking for and finding the existence of a /Library/.local or ~/Library/.local directory on your Mac is the most obvious indicator of infection. But first you will need to ensure you have Finder set to show hidden files.
By default, Mac OS X’s Finder keeps system files—which generally start with a dot, like .bash_profile—out of sight. To set Finder to show all hidden files, open Terminal and type the following:
defaults write com.apple.finder AppleShowAllFiles TRUE
killall Finder
To set it back, simply execute those same commands, but switch TRUE to FALSE.
If the /Library/.local directory exists, there may also be a keylogger extension located at /System/Library/Extensions/updated.kext.
Also check for the Agent/Daemon: com.updated.launchagent.plist in /Library/LaunchDaemon/ or ~/Library/LaunchAgents/. Its contents will reference a program in /Library/.local:
Is the Ventir Trojan related to OSX/Crisis?
It appears that OSX/Ventir is similar to OSX/Crisis, as researchers have found it has approximately the same number of modules with similar functionality. Unfortunately, using open source software makes it easier for criminals to create new Mac malware, and it’s likely that such attacks will grow more prevalent as it becomes simpler and simpler to use off the shelf components to build malicious software.
How to eradicate Ventir malware
The Ventir Trojan is a great example why a layered defense strategy is so handy. We’ve already covered the need to back up your data in multiple places and establish a good backup routine. But what else can you do?
- Create a non-admin account for everyday activities
- Use unique, strong passwords
- Uninstall Java from your machine
- Do not install pirated software from peer-to-peer sites
- Pay attention to system warnings when it asks you whether you want to install something
- Turn on FileVault full-disk encryption on your Mac
- Run “Software Update” and patch your Mac promptly when Apple security updates are available
- Ensure all third-party software is up-to-date (i.e. Flash Player, web browsers)
- Use a web browser that contains a sandbox and has a solid track record of fixing security issues promptly
- Install a good Mac security solution (this includes anti-virus and firewall)
Mac anti-virus is meant to detect known-bad things, and as Ventir was previously unknown, odds are it would not have caught this. Firewalls, however, are meant to detect unknown network traffic and would likely have alerted on this. By having layered security on your machine, you increase the chances of being able to prevent incidents like these.
Intego VirusBarrier with up-to-date virus definitions detects and eradicates this malware, which it identifies as OSX/Ventir. Additionally, some of the keylogger components (Keymap.plist and updated.kext) were already detected by Intego VirusBarrier as OSX/logKext.E and OSX/logKext.D.