Security & Privacy + Security News
Update Your iOS Devices – Your Cookies May Be at Risk!
Posted on
by
Graham Cluley

If you own an iPhone or iPad chances are that you already know that there is an update to iOS available. With a few presses your device should be downloading iOS 9.2.1 which, according to Apple, includes a number of under-the-hood performance improvements and bug fixes.
If you bothered to read the update dialog on your iDevice, you will have seen that iOS 9.2.1 addresses a bug that was causing headaches for businesses using Mobile Device Management.

But, of course, that wasn’t the only issue that the new version of iOS aims to resolve. As researchers at Skycure explain, iOS 9.2.1 tackles a vulnerability that has potentially left iPhones and iPads open to abuse for at least the last 2.5 years.
The flaw, known as CVE-2016-1730, is described at the bottom of Apple’s advisory about the security content in the new version of iOS:
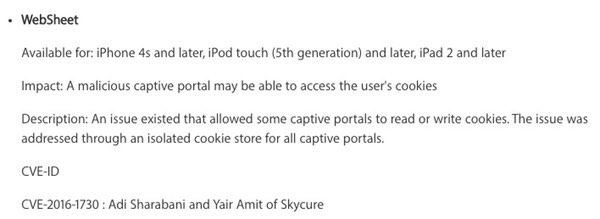
WebSheet
Available for: iPhone 4s and later, iPod touch (5th generation) and later, iPad 2 and later
Impact: A malicious captive portal may be able to access the user’s cookies
Description: An issue existed that allowed some captive portals to read or write cookies. The issue was addressed through an isolated cookie store for all captive portals.
CVE-ID
CVE-2016-1730 : Adi Sharabani and Yair Amit of Skycure
From that brief description it may be difficult to determine precisely what the problem was, so I’ll do my best to explain.
When you connect to the Wi-Fi at your local coffee shop or in the airport departure lounge, you usually find that your iPhone or iPad is redirected to a special login page. This is known as a “captive portal,” and is triggered by your device making a request to the url http://www.apple.com/library/test/success.html
If the request is redirected to a third-party page then Apple knows that the providers of the wireless connectivity have put a portal in place, and a dialog box is displayed via an embedded browser giving you the opportunity to login.

So far, so good.
But, back in June 2013, Skycure discovered that the embedded browser used to display captive portals had a vulnerability, which saw private cookies already stored in the user’s mobile Safari browser shared with the captive portal, and vice versa.
As Skycure’s Yair Amit explains, the vulnerability opens opportunities for attackers to do a number of things:
- Steal users’ (HTTP) cookies associated with a site of the attacker’s choice. By doing so, the attacker can then impersonate the victim’s identity on the chosen site.
- Perform a session fixation attack, logging the user into an account controlled by the attacker–because of the shared Cookie Store, when the victims browse to the affected website via Mobile Safari, they will be logged into the attacker’s account instead of their own.
- Perform a cache-poisoning attack on a website of the attacker’s choice (by returning an HTTP response with caching headers). This way, the attacker’s malicious JavaScript would be executed every time the victim connects to that website in the future via Mobile Safari.
If abused, the consequences clearly could have been serious.
Apple has apparently taken 2.5 years to roll out a fix for this problem, as Skycure first informed them in June 2013. According to the researchers “this is the longest it has taken Apple to fix a security issue reported by us,” but they do acknowledge that the fix was “more complicated than one would imagine” and that Apple was receptive and responsive to the issue.
I guess we all have to be grateful that Skycure was patient, and wasn’t tempted to go public about the flaw before Apple had rolled out a fix — even though it must have been frustrating quite so long.
Because, if Skycure had acted like some other vulnerability researchers have in the past, there is no doubt in my mind that this flaw might have been more widely exploited by malicious hackers.