Malware + Recommended + Security News
Unwanted cryptomining debuts (briefly) in Mac App Store
Posted on
by
Joshua Long
How much should you trust App Store apps? And how well does Apple screen apps to ensure they don’t contain any unwelcome behavior?
If you think of the App Store as a safe haven, you might be unpleasantly surprised about some recent events.
Calendar 2 App Oversteps Its Bounds
![]() Several users of Qbix, Inc.’s app Calendar 2, available in the Mac App Store, recently began having some unexpected and undesirable experiences after updating the app. According to App Store reviews, users may have experienced the following strange behaviors:
Several users of Qbix, Inc.’s app Calendar 2, available in the Mac App Store, recently began having some unexpected and undesirable experiences after updating the app. According to App Store reviews, users may have experienced the following strange behaviors:
- their Mac seemed to run more slowly
- their Mac’s fans would spin loudly for hours
- their Mac was noticeably hotter than usual
- their MacBook’s battery drained much faster than normal
- their Mac’s CPU (central processing unit) would constantly stay at its maximum utilization
- they would repeatedly see dialog boxes telling them that a process called xmr-stak had unexpectedly quit
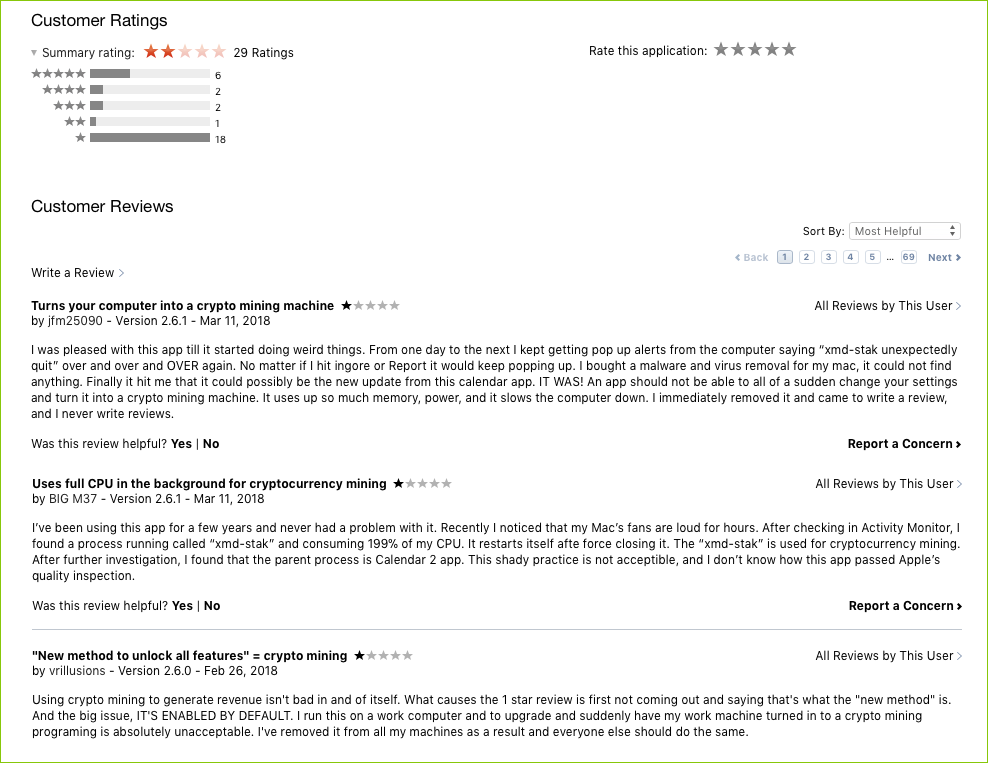 Calendar 2’s reviews have not been positive. Image: Patrick Wardle
Calendar 2’s reviews have not been positive. Image: Patrick Wardle
What could have caused all of these problems? It turns out that Calendar 2 versions 2.6.0 and 2.6.1 included a new “feature” that gave users an option to enable all of the app’s advanced features without having to pay the usual $17.99 for them.
 That “feature” was that the calendar app would use their Mac’s processing power to mine for the Monero cryptocurrency (similar to Bitcoin) on behalf of the developer.
That “feature” was that the calendar app would use their Mac’s processing power to mine for the Monero cryptocurrency (similar to Bitcoin) on behalf of the developer.
(To learn more about cryptocurrency mining, listen to episode 5 of the Intego Mac Podcast.)
The app’s description in the App Store said nothing about cryptocurrency. And according to some App Store reviews, the mining mode was allegedly enabled by default, meaning that users were taken by surprise and did not opt into allowing their Mac to exhibit the undesirable behaviors.
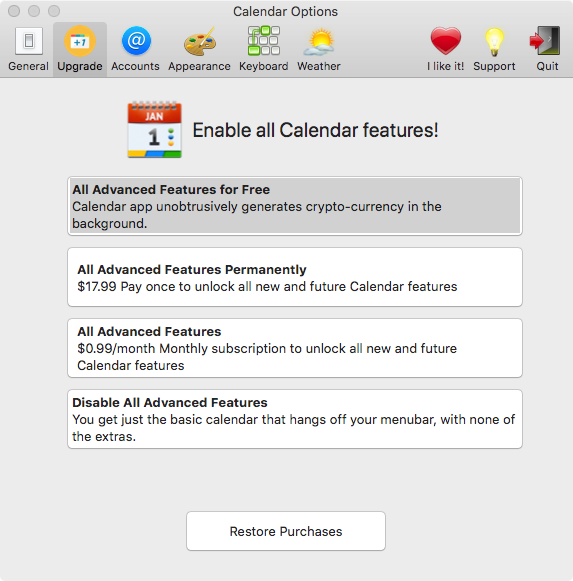 Calendar 2 was not very clear about what it was doing. Image: Wardle
Calendar 2 was not very clear about what it was doing. Image: Wardle
Even if users had explicitly chosen to enable cryptocurrency mining, the app itself wasn’t particularly clear about what behavior users could expect. The option within the app claimed that “Calendar app unobtrusively generates crypto-currency in the background,” without further explanation about what that means or how it could potentially impact their user experience.
In any case, the app’s behavior was evidently not “unobtrusive,” and users were very displeased.
After a few popular news sites had written about what was happening, and in the midst of much discussion in public forums such as Twitter, Apple evidently removed the offending app from the Mac App Store on March 12. On March 13, Qbix released an updated version of Calendar 2 that appears to have removed the mining capabilities.
If you have an affected version of Calendar 2 installed on your Mac, Intego VirusBarrier will warn you by flagging the software as OSX/Miner. Although not necessarily malicious, affected versions of Calendar 2 could best be described as “potentially unwanted apps” (PUAs, also known as a “potentially unwanted programs” or PUPs); they exhibit undesirable and potentially harmful behavior inconsistent with users’ wishes.
If you’d like to read a highly technical analysis of an affected version of the Calendar 2 app, see Patrick Wardle’s write-up.
For further discussion of this news story, be sure to listen to episode 23 of the Intego Mac Podcast, in which Kirk McElhearn and I discuss this and other topics.
Did Calendar 2 Violate App Store Policies?
![]() There was some debate about whether or not Calendar 2 technically violated Apple’s App Store Review Guidelines. As of when this article is being published, Apple does not explicitly forbid App Store apps from mining cryptocurrency.
There was some debate about whether or not Calendar 2 technically violated Apple’s App Store Review Guidelines. As of when this article is being published, Apple does not explicitly forbid App Store apps from mining cryptocurrency.
However, there are a number of grounds on which Apple could potentially ban apps that exhibit similar behaviors, including:
From section 3.2.2, on “Unacceptable” business models:
“Monetizing built-in capabilities provided by the hardware or operating system, such as Push Notifications, the camera, or the gyroscope…”
Leveraging CPU or GPU (graphics processing unit) processing power to make money for the developer could be interpreted as a violation of this policy.
From section 3.1.4:
“Apps may not use their own mechanisms to unlock content or functionality, such as license keys, augmented reality markers, QR codes, etc.”
Calendar 2’s option to get “all advanced features for free” by enabling cryptocurrency mining could be viewed as a violation of this policy.
From section 2.5.3:
“Apps that transmit viruses, files, computer code, or programs that may harm or disrupt the normal operation of the operating system and/or hardware features… will be rejected.”
In this case, the cryptocurrency mining clearly disrupted Macs’ normal operation.
From section 2.1:
“We will reject incomplete app bundles and binaries that crash or exhibit obvious technical problems.”
At least one review that many people rated as helpful said that the mining process that ran in the background (xmr-stak) was repeatedly crashing. To the average user, maximum CPU utilization slowing down their whole computer is a technical problem!
From section 1.4.5:
“Apps should not urge customers to use their devices in a way that contradicts safety documentation for Apple hardware, risking damage to the device or physical harm to people.”
Although running cryptocurrency mining software may not be mentioned in Apple’s safety documentation, the behavior exhibited by Calendar 2 could risk damage to a Mac (e.g. caused by overheating for an extended period of time) and could potentially cause physical harm to people (e.g. skin burns caused by an overly hot laptop).
Regardless of whether cryptocurrency mining is technically in violation of the App Store Review Guidelines or not, it’s certainly in Apple’s best interest to prevent apps from behaving as Calendar 2 did.
Can you imagine if it were a regular occurrence for App Store developers to include mining features in their apps? What if you had more than one cryptocurrency miner running on your system at the same time, fighting for control of your Mac’s processing power?
If Apple were to permit App Store apps to behave this way, Macs would develop a reputation of being slow, unstable, and unusable—and that’s certainly not in the best interests of Apple or Mac users.
Can We Still Trust the App Store?
Even if you’ve never used Calendar 2, this story serves as a reminder that Apple’s app review processes—and the humans who review apps—are not infallible.
Although such occurrences may not happen very often, users should always exercise caution when installing any third-party app.
Read reviews first, and make sure the software seems reputable before you choose to download it. For further tips on how to avoid unwanted cryptocurrency mining on a Mac, see Intego’s latest YouTube video for a brief tutorial.
In spite of the recent incident, the App Store nevertheless remains one of the safest places to obtain Mac software.
 The Mac App Store is certainly safer than download aggregation sites, as we were reminded in February when MacUpdate mistakenly distributed malware-infected copies of Firefox and two utility apps, OnyX and Deeper.
The Mac App Store is certainly safer than download aggregation sites, as we were reminded in February when MacUpdate mistakenly distributed malware-infected copies of Firefox and two utility apps, OnyX and Deeper.
Download aggregation sites are also notorious for displaying confusing advertisements with fake download buttons, so there’s an increased risk of accidentally downloading adware or other potentially unwanted software.
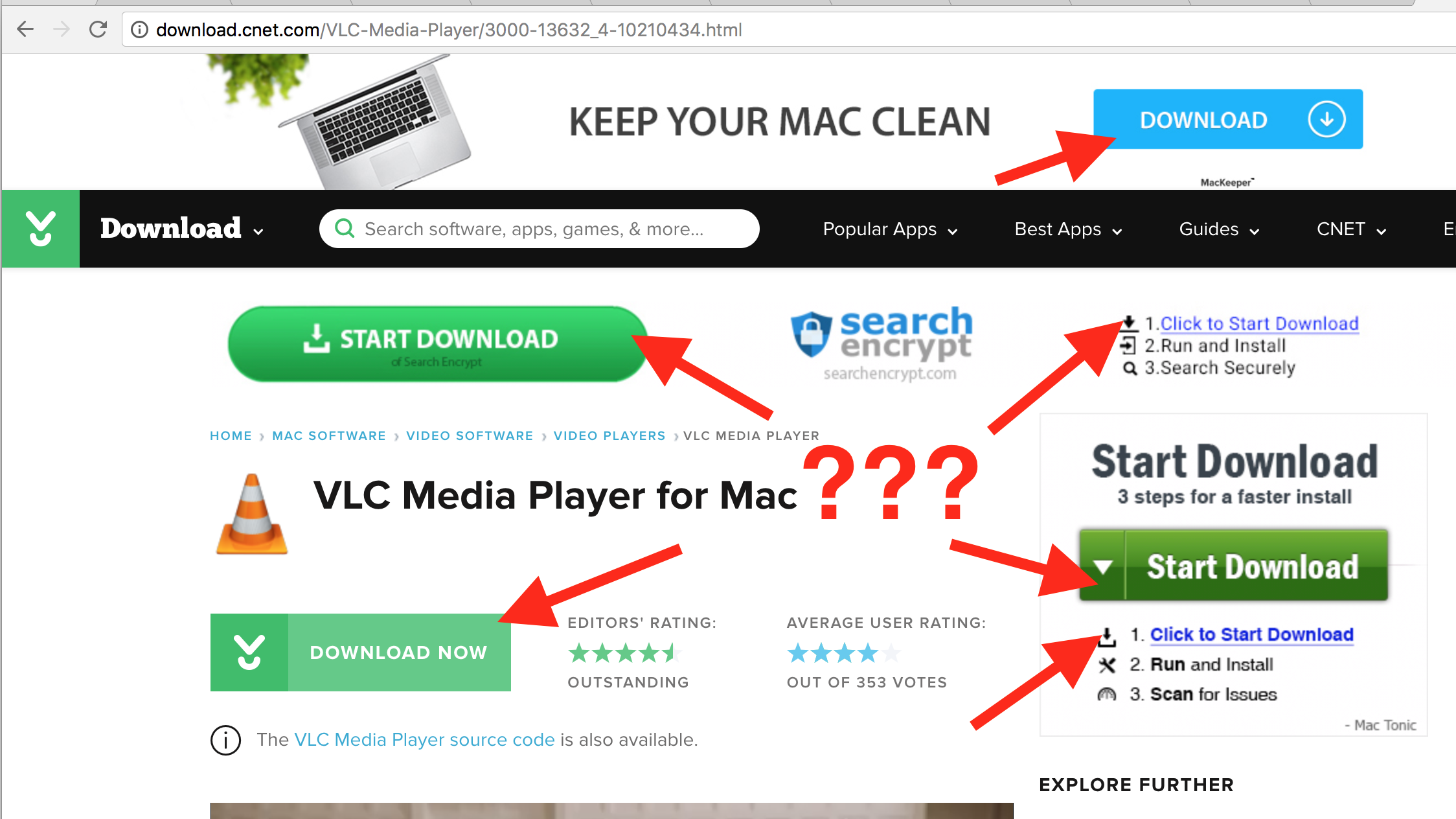
CNET’s ad-laden Download site can be a digital minefield.
The rule of thumb discussed in our January video interview with Amit Serper is still good advice:
- Obtain apps through the Mac App Store when possible.
- When you need an app that isn’t in the Mac App Store, the safest place to obtain the app is the developer’s official site.
Be sure to subscribe to the Intego Mac Podcast for weekly audio discussions of topics like this, and subscribe to the Intego YouTube channel to get informative video updates—click on YouTube’s bell icon (?) to get notified when each new video is available.
Have something to say about this story? Share your comments below!