Top 10 online scams to beware of: from malvertising to deepfake kidnappings
Posted on
by
Kirk McElhearn and Joshua Long

The online world is full of scams. Given the ease of creating fake websites, bogus ads, and deceptive emails, the Internet is full of risks. Everyone needs to be on their guard and understand that just about anything can be faked and used to try to trick you.
This article looks at the top ten most common and dangerous online scams, so you know what to look out for.
- 1. Phishing
- 2. Fake invoice scams
- 3. Porn blackmail emails
- 4. Scareware
- 5. Malicious Google Ads
- 6. Tech support scams
- 7. Fake celebrity scams
- 8. eBay scams
- 9. Online dating and romance scams
- 10. Fake emergency/impersonation scams
1. Phishing
Phishing uses deceptive communications to steal sensitive information like login credentials and financial data. It is most commonly used in emails, but also exists with text messages (SMShing or smishing), phone calls (vishing or voice phishing), and sometimes targets specific individuals (spear phishing). It’s one of the most common attacks because it works so often.
Phishing emails generally try to get you to click a link to log into a website, where you enter your username and password. A victim might think it’s a legitimate site, but their credentials are collected by cybercriminals who can then access their account.
Examples include emails or other communications that try to get you to update bank information, log into your email account, or log into services like PayPal or iCloud. Some of these can also be fake security alerts, purporting to come from companies like Apple, Google, or Microsoft.
Make sure you check links before clicking on them so you don’t get caught; on a Mac or Windows PC, you can often hover your mouse cursor over a link or button in an e-mail to find out where it will take you. And after clicking a link, you should also check the address bar of your browser to ensure you are at the site you expect to be.
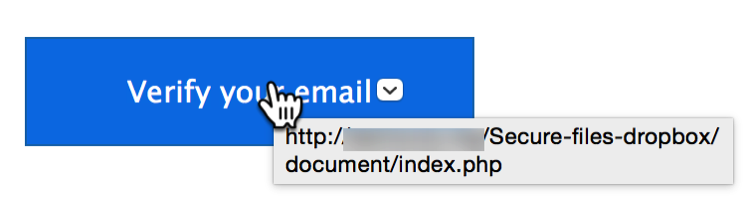
2. Fake invoice scams
A recent online scam involves sending someone a fake invoice for a product or service, which can claim you owe hundreds of dollars, and which includes a phone number for “customer service.” Many of these scam messages are sent via legitimate platforms, such as PayPal or QuickBooks.
If you call these scammers to contest the charges, they may attempt to get more personal information from you, such as bank account or credit card details. They’ll lead you to believe it’s for the purpose of refunding you, but in fact they just want to make charges against your accounts. They might even try to infect your computer, if you give them remote access to it.
3. Porn blackmail emails
A common email scam is the porn blackmail or sextortion email. It claims to have hacked your computer, your email account, and sometimes all your devices. The emails claim to have hacked your cameras, and recorded you performing activities that you might not want your family, friends, or co-workers to see.
In reality, such messages are bogus. Most likely, the supposed “hacker” has not hacked you at all. Rather, it’s just a scammer, and they’ll ask you to pay a ransom via cryptocurrency.
See our recent article on porn blackmail e-mails for a detailed look at one of these recent scams.
Porn blackmail “sextortion” emails: Have you been hacked? A new scam
4. Scareware
Scareware is a malicious site or app that tricks users into downloading or buying fake security software, often through alarming pop-ups or messages. You may encounter these pop-ups on dodgy websites, or even through poisoned Google searches. They may say that your computer has a virus, and some pretend to be alerts from companies like Apple, Microsoft, or Google. They might even mimic your own operating system’s interface to try to seem more plausible or to trick you into clicking on something to initiate a malicious download.
No website can tell whether your computer is infected with malware, so you can ignore these alerts. To close the browser tab or window without clicking on a fake button, use a keyboard shortcut instead: Command-W (⌘W) on a Mac, or Alt+F4 on a PC.
5. Malicious Google Ads
“Malvertising” is when cybercriminals create Google ads that appear legitimate, and that promote popular software or services. These ads often appear at the top of search results, making them highly visible to users. When you click on a malicious ad, you are often redirected through a series of benign websites before landing on a malicious site. This redirection helps the attackers bypass Google’s safe browsing checks.
To avoid this, either avoid clicking on Google ads, or be very careful when you do so. Real ads will likely redirect once to the website after Google records the click, but if you see multiple redirections (i.e. if your address bar changes several times), or if you end up at a domain that looks different from what you expected, the ad is likely to be poisoned.
Of course, it’s not just Google where you might encounter malicious advertisements. Malvertisers may buy ads on Bing or other search engines, and of course you can potentially encounter malicious ads elsewhere on the Internet.
Use protection tools: ad blocker and antivirus
Given how common poisoned ads are, it’s wise to take additional precautions. You may wish to use an ad blocker, for example uBlock Origin, which is available for most desktop browsers except Safari. Or you may prefer to use a browser with a built-in ad blocker, like Brave with its Shields set to Aggressive mode.
But even with the best ad blockers, there are also poisoned search results to contend with; these are hacked or high-ranked malicious sites that appear in search results. So even if you’re blocking ads, you may still inadvertently land on a lookalike page and end up downloading malware from a very realistic-looking site. You’ll need to use antivirus software such as Intego’s VirusBarrier X9 for Mac or Intego Antivirus for Windows to stay protected from this type of malware; built-in protections on macOS or Windows may be insufficient.
6. Tech support scams
A scam similar to scareware occurs by telephone, when scammers call saying that they are from a major company (e.g. Microsoft or Apple), and that they have detected that your computer is infected.
In such cases, you are led to install software to supposedly allow the caller to help you get rid of the malware. This software lets the scammer view your screen and install other apps, and may allow them to exfiltrate personal data and remain logged into your computer after the call ends; this can enable scammers to record your keystrokes to get your passwords, and then get access to your accounts, among other things.
7. Fake celebrity scams
An increasingly common scam occurs when scammers post fake profiles of celebrities on Facebook and Instagram, and then contact users saying that they would like to chat with them. This can lead to a long con where the victim believes they are getting into a relationship with the celebrity. After a while, the celebrity asks for money, as one woman found out recently: I thought Bob Dylan had fallen in love with me – then he asked me for $5,000.
Many celebrities post warnings on their Facebook pages and Instagram accounts, but not enough people see these warnings. It’s highly unlikely that any celebrity would chat directly with random individual fans like this. You can safely ignore such friend requests or accounts that slide into your DMs claiming to be celebrities.
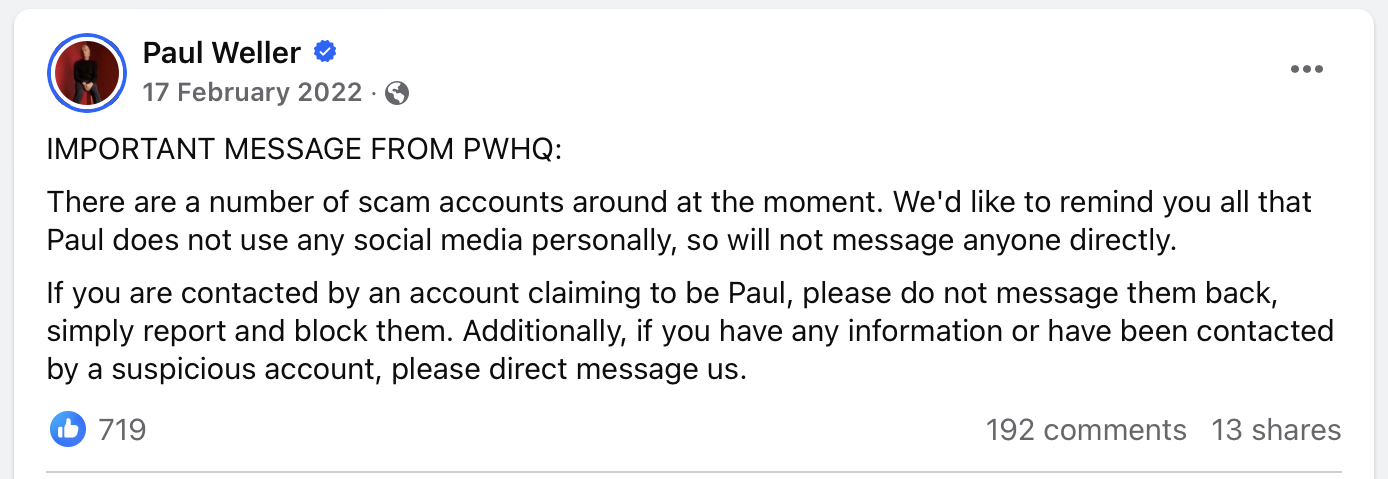
A warning on Facebook from an actual celebrity about fake accounts pretending to be him.
8. eBay scams
How to not get scammed as an eBay seller
If you sell valuable items on eBay, you’ve probably already encountered this scam. You may want to sell a used iPhone, iPad, or Mac, and you list it on eBay. You quickly get contacted by people who want to buy the item immediately—even if the listing is set up as an auction—but they don’t want to pay you through eBay and PayPal. They give you an email address to contact them directly.
Of course, if you were to sell the item directly to the buyer, they’ll either avoid paying altogether, or they’ll dispute the transaction claiming the item was broken or that you defrauded them. You should never sell anything “on eBay” outside of the normal eBay listing process, because you’ll lose access to eBay’s seller protection.
And for anything truly valuable, you should arrange to hand the item over directly to the buyer in person if possible, and take pictures when you do so. This way, they can’t claim that the item was damaged or broken when they received it.
eBay buyers, beware, too!
Naturally, sellers aren’t the only scam victims on eBay. Buyers should beware as well! If a listing seems too good to be true, it probably is. Here are some tips for eBay buyers:
- A “Buy It Now” listing for an item in new or like-new condition that’s far below the normal asking price is suspicious. (Auctions, however, sometimes do this legitimately to appear in more search results, to get more people to watch the listing.)
- If the seller has negative feedback, a low number of positive feedback, or a lack of feedback for having sold items previously, these can all be potential red flags.
- Watch out for listings that use stock product images rather than actual photographs. And if the listing uses real photos, but you have other reasons to be suspicious, use the “Search by Image” button at Google Images to try to determine whether that photo has appeared elsewhere online.
- Read the entire listing carefully, and examine each picture. For example, sometimes items sold as “new” don’t actually meet eBay’s criteria for such a designation. Some sellers may also try to hide defects by using low-quality photos, or may use other tricks to try to make more money on the sale than the item is actually worth.
9. Online dating and romance scams
Criminals create fake profiles to deceive victims into believing they are in a genuine relationship, and scammers manipulate victims over time to gain their trust and ultimately ask them for money (similar to fake celebrity scams; see above). These scams are so common that the US Federal Trade Commission (FTC) has a page with advice about romance scams.
Dating sites generally have detailed information about how to spot scam profiles, and you need to be very careful. If someone asks for money, especially if you haven’t met in person, it’s a scam.
10. Fake emergency/impersonation scams
Messages that demand wiring money
In what is sometimes called “grandparent scams,” fraudsters may pose as a child, or friend in distress. These messages may come as emails, texts, or DMs (e.g. via Facebook Messenger). The sender asks for money to be sent immediately to help with an emergency situation. They might claim that they’re stuck in jail or in an airport overseas, and can’t access their financial accounts. Such scams often ask you to send money via a wire transfer service, but they might ask you to send cryptocurrency instead.
You may be more likely to receive such a scam message if you’ve recently accepted a friend request from someone you thought you were friends with already; this is a common tactic used by scammers. It can also happen if your loved one’s real account gets hacked.
Virtual kidnapping scams
In extreme but increasingly common cases, you may get what’s called a virtual or hoax kidnapping phone call or text. The phone call variation can be extremely frightening, and effective at catching you off guard. The voice on the other end may sound like the purported loved one (for example, your child or grandchild); they may sound like they’re crying, saying they’re being held by a kidnapper or the police and can’t talk. After this brief and startling exchange, someone else takes the phone and takes over the negotiation.
With AI-enhanced deepfake tools, criminals can mimic voices, so the voice may sound authentic. Don’t immediately assume that any such calls or texts are authentic. Stay calm, have someone else call the police while you stay on the phone; in the meantime, attempt to contact your loved one directly, and look up their real location in the Find My app (if they have an iPhone, MacBook, or an AirTag they keep with them) to verify that they’re somewhere safe.
The U.S. FTC, Customs and Border Protection (CBP), and even the National Institutes of Health (NIH) all have warning pages about similar scams, and offer additional advice.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
Header graphic credits: Main image “Bitcoin (BTC) Scam” by Richard Patterson (CC BY 2.0); fishing hook by daniel jaeger (CC BY 2.5); phone receiver via PxHere (CC0); CCTV camera via rawpixel (CC0); eBay logo © eBay Inc.; email and lipstick-kiss emojis © Apple Inc.; compilation by Joshua Long for Intego.