Spyware Gang Ports XSLCmd Malware to Mac OS X from Windows
Posted on
by
Graham Cluley

Stop kidding yourself that cybercriminals aren’t interested in infecting Mac computers with malware. Although there is much, much more malware for Windows than there is for Mac OS X, that’s not going to be any consolation if your Apple desktop computer or laptop is one of the unfortunate ones to find itself infected.
And it’s clear that, just like the rest of the world, the computer underground has noticed the increasing popularity of—and buzz around—Apple products, and realises that if it wants to effectively target those particular organisations or individuals who use shiny devices designed in Cupertino that they can’t afford to ignore OS X.
After all, let’s face it, Apple Macs and MacBooks are awesome computers, and there are plenty of company execs with access to sensitive corporate information who swear by them.
If you wanted any evidence of the unwanted criminal interest in infecting Mac OS X users, then consider a newly discovered threat detected by Intego VirusBarrier as OSX/XSLCmd.
What’s interesting about OSX/XSLCmd is that it shares a “significant portion” of code with the Windows version of the XLSCmd backdoor, which was first seen at least five years ago.
Researchers at FireEye have written extensively about the new version of the threat, designed to infect Mac computers:
“The backdoor code was ported to OS X from a Windows backdoor that has been used extensively in targeted attacks over the past several years, having been updated many times in the process.”
A hacking gang named GREF by the security community has been identified as the criminals behind the malware. In the past, the GREF gang has used malware to target defence contractors, engineering companies and non-government organisations.
A typical scenario for how GREF manages to target victims is by hacking websites popular with particular industries, and injecting malicious JavaScript disguised as Google Analytics code into their webpages.
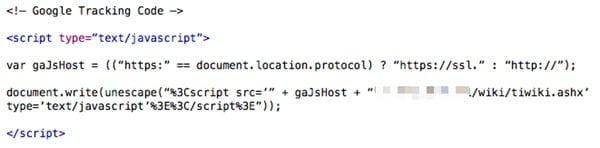
In the original Windows variant (circa 2009), anyone who visited a poisoned webpage on an unsecured computer could find that XSLCmd had been silently installed onto their PC, which opened a backdoor through which hackers could exfiltrate sensitive information.
But this isn’t a simple port to OS X and the delivery method is not yet clear, if there indeed is one. At this point, the malware looks weak and has not yet been found in the wild. (The ‘art’ of creating malware is not difficult. Finding a way to actually get it on a target computer is the hard part.)
However, new features have been added to the OS X variant that could help hackers hell bent on spying and stealing information if it were ever installed:
“The OS X version of XSLCmd includes two additional features not found in the Windows variants we have studied in depth: key logging and screen capturing.”
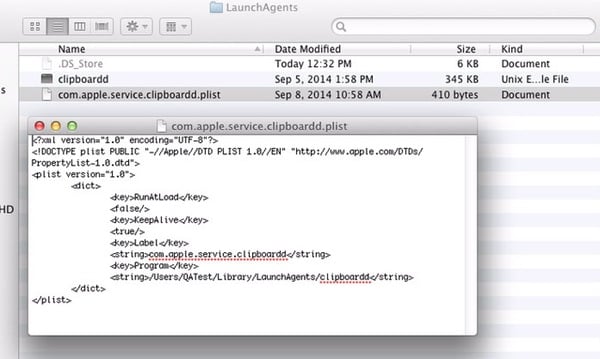
Intego researchers have analysed the malware, which is detected as OSX/XSLCmd. When run, the malware copies itself to the ~/Library/LaunchAgents folder and renames itself clipboardd (yes, with two ‘d’s), and is deleted from its original location.
By creating a plist file, the malware ensures that it is always running.
Your best defence? Well, prevention is always better than cure. Ensure that your Mac’s anti-virus software is always running and kept up-to-date with the latest definitions.
And if you know someone who loves their Mac but isn’t running any anti-virus software, do them a favour and clue them up. There may not be as much malware for Mac as there is for Windows, but the last thing anyone wants to happen to their computer is to be silently hit by a hack attack.
Editor’s update: We have updated this article to clarify some possibly misleading information about how the malware infects Macs. For the OS X platform, Intego has not found a valid delivery mechanism for OSX/XSLCmd. The delivery system previously noted was how the original malware for Windows attempted to deliver itself on Windows machines a number of years ago. Intego is continuing to research how this malware could ever actually end up installed on a Mac. Of course, Intego VirusBarrier has been updated to detect and disable this malware should it be found.