SilverInstaller, Sneakier Than Previously Thought
Posted on
by
Jay Vrijenhoek

Last week, Intego reported on the discovery of a new fake Flash Player installer, called SilverInstaller. When SilverInstaller was found, a few things didn’t add up, so the Intego malware team kept poking at it over the weekend and have uncovered some new details. What we found is that SilverInstaller is a bit sneakier than previously thought — it detects whether it’s running in a virtual machine and behaves differently.
Here’s everything we now know about SilverInstaller.
Why keep poking at it?
Initially some of the payloads did not decompress. The PostInstall script (dropper) that is responsible for installing the payload downloads this as a compressed file “act.tgz.” This file, when examined, sometimes opened and sometimes didn’t. Why?
Also, why does the installer say it’s going to install MacKeeper, DavinciSearch and MegaBackup but install MPlayer instead?
Unanswered questions do not sit well with the team, so down the rabbit hole they went.
All right Alice, what did they find?
The biggest find is the difference in behavior when the installer runs in a virtual machine or a real Mac.
The installer mentions it will install several Potentially Unwanted Applications (PUA) but fails to do so. Intego’s malware team found out this is intentional.
The way malware is tested is by setting up a virtual machine (VM) that runs a copy of macOS. This VM can be infected without having to worry about compromising the host Mac it runs on, and when the testing is done, the VM can be stored or simply deleted. It is much safer and significantly faster than infecting an actual Mac and having to re-install it completely when done.
SilverInstaller is aware it will probably end up inside a VM to be picked apart by malware researchers, so it cleverly installs only MPlayer if it finds itself inside a VM. If it sees the Mac is an actual Mac and not a virtual one, it behaves differently. Even on an actual Mac it checks for signs of analysis and if any are found, like Packet Filtering, MPlayer is installed. However, if no analysis tools are found and the Mac is real, all of the goodies mentioned by the installer are downloaded and installed.
I previously mentioned: “The Dropper downloads the Payload, which is then responsible for opening a connection to “http://i.silvinst.com” on port 80 and a shell script is then executed.” This shell script, install_unit.sh, becomes much more interesting if it finds itself downloaded to a real Mac. Rather than installing just MPlayer, it installs the following:
MacKeeper (if not already present):
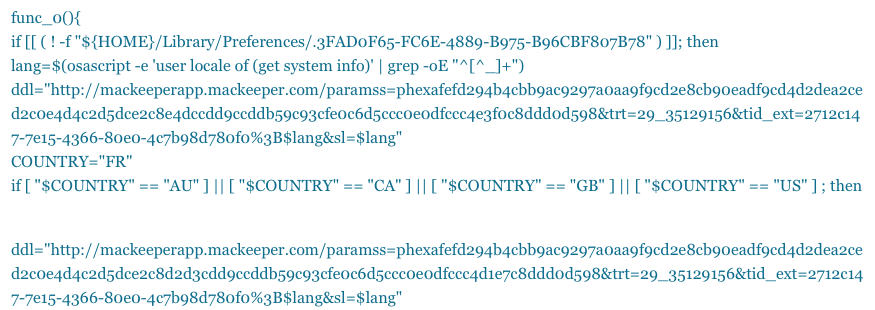
It’s even nice enough to make sure the user receives a localized version, though it currently installs the same version no matter what.
VSearch
“http://i.silvinst.com/static/c/c.tgz”
A Pirrit injector (VSearch family)
“http://i.silvinst.com/static/ij/ij_v2.tgz”
BrowserEnhancer, which Intego detects as VSearch
“http://i.silvinst.com/static/sr/sr_v2.tgz”
And finally MPlayer
“http://i.silvinst.com/static/mplayer/MPlayer.zip”
As observed previously, the payload files are deleted when the installations are finished and the installer itself can only be used once.
Other Findings
You may recall each downloaded package has a unique file name and hash. Intego quickly confirmed that the packages are dynamically generated (built) by the server. This not only causes every downloads installer package to have a unique name, like “FlashPlayer_01.10.pkg” or “FlashPlayer_01.18.pkg,” but also means the contents of each installer vary slightly. Part of this varying data is the dropper that downloads the payload onto a system, the “act.tgz” file mentioned earlier.
The first time the installer runs it shows an installer that doesn’t actually do anything, runs the PostInstall script, downloads the “act.tgz” payload, decompresses it, and then downloads and installs MPlayer. When done, the payload file is deleted.
The second time the installer is opened, it behaves the same but the result is different. This time when the payload “act.tgz” file is downloaded, it’s a fake. It does not decompress and is deleted right away. The installer knows if it has been run before by comparing keys with the server. Each package is assigned a key as it’s built by the server, and it is likely that the installer checks with the server to see if a key has been used more than once. This basically guarantees the installer package can only be used once, even if copied to another machine on a different IP address. Here is an example of a key:
“http://t.silvinst.com/is/cact?i=”fd4ee38b-d713-47ba-82c7-3df8790288c7“&ve=10.12”
This key is the UUID, which is taken from the IOKit framework (IOPlatformUUID) by the Payload. The UUID is a unique identifier for your Mac and helps SilverInstaller keep track of which machine the installer has been run on.
In the last few days, the people or person behind SilverInstaller has already changed a few things:
- The subdomain previously used by the dropper and payload to download their contents from “http://i.silvinst.com” has been changed in some cases to “http://t.silvinst.com.”
- The “act” payload in some cases is now signed with an adhoc identifier and not a Developer ID certificate.
Websites that these installers have been found on are extratorrent.cc and k2s.cc. Clicking on those pages will result in pop-ups and redirects that feed the fake Flash Player installers.
Apart from the observations mentioned in the previous article, we note that the dropper does not collect User ID’s (UID’s).
$ ls -la FlashPlayer_XX.X/base.pkg/Scripts/total 48drwxr-xr-x 8 user admin 272 Oct 18 15:27 .drwxr-xr-x 6 user staff 204 Oct 18 15:27 ..-rw-r–r– 1 user admin 36 Oct 17 23:35 27b86b7f-e4c5-4a4c-a56f-b54b3a423617-rw-r–r– 1 user admin 36 Oct 17 23:35 51ef332f-6ed2-4574-aea5-6f8788661b68-rw-r–r– 1 user admin 36 Oct 17 23:35 b45bfc63-465d-426c-8bad-f1d0dea3d202-rw-r–r– 1 user admin 36 Oct 17 23:35 eaf2e7d6-f6c3-4f91-9428-cb10eb4e3cea-rw-r–r– 1 user admin 36 Oct 17 23:35 f7a5b00e-fd20-45f9-9c90-7ac8a128f31f-rwxr-xr-x 1 user admin 595 Oct 17 23:35 postinstall
We now know that those are Generated User ID’s (GUID’s). The GUID hashes are collected, but at this time the research team is unable to link these to existing users on an infected system. This goes for both physical users and hidden system process users.
What can Mac users do to protect their computers?
The steps Mac users can take to protect their Macs remains unchanged; only download software from a reliable source.
Manually removing SilverInstaller
The below list was adjusted to reflect infection of a real Mac. If infected, Mac users can manually remove the SilverInstaller files to clean up the infection. From the Finder menu “Go,” select “Go to Folder” and copy/paste the following path:
- /var/tmp/
In this folder you may find several files, delete the following:
• act (folder)
• MPlayer OS X Extended (application)
• MPlayer.zip (archive)
• re.txt (text file)
• c (folder)
• c.tgz (archive)
• ij (folder)
• ij.tgz (archive)
• mk.pkg (package)
• sr.tgz (archive) - Delete the following applications from the Applications folder:
• MPLayer OS X Extended
• MacKeeper - Also delete the installer “FlashPlayer_XX.X.pkg” from it’s download location.
Intego VirusBarrier identifies the SilverInstaller files as OSX/SilverInstaller, and if detected, VirusBarrier will eradicate it from your system. The installers that use the t.silvinst.com subdomain are recognized as variant B.
All this seems like a lot of trouble to go through just to get some PUA’s loaded onto a system, so Intego is keeping a close eye on SilverInstaller to see if it will evolve into something more.