Shrootless: A Mac Vulnerability Found By Microsoft
Posted on
by
Jay Vrijenhoek
In late October, Apple released macOS Monterey, this year’s major upgrade to the Mac operating system. We wrote about some of the security vulnerabilities that Monterey resolved, one of which was nicknamed “Shrootless.”
Let’s take a closer look at this intriguing vulnerability, which was surprisingly discovered by a Microsoft security team member.
But even before we get to that, it’s worth reviewing the macOS protection technology that Shrootless bypasses: SIP.
A brief explanation of SIP: System Integrity Protection
System Integrity Protection, or SIP, was introduced in 2015 with the release of OS X 10.11 El Capitan. It’s a security feature built into the Mac OS that’s designed to protect most system folders, apps and processes, and kernel extensions from being written to, modified, or replaced.
SIP allowed the operating system to run “rootless”—that is, without a root or superuser account, ostensibly. The system does not actually function without a root account; it still exists, but the introduction of SIP restricted its potential for abuse.
The folders managed by SIP include:
- /System
- /usr
- /bin
- /sbin
- All apps pre-installed by Apple
A number of things in everyday computing require access to those locations, though. For this reason, certain privileged processes and apps—including Apple software updates and installers—are allowed to access them without user approval. The process or app has to be signed by Apple and have a special entitlement to be allowed a SIP bypass.
SIP has undergone some changes over the years but is mostly still the same as what was introduced in 2015. Since macOS 10.14 Mojave, SIP now also protects third-party apps so they cannot be tampered with. If a kernel extension needs to be installed, the only way to get it past SIP is if it’s signed with an Apple Developer ID that specifically allows for signed kext (kernel extension) certificates.
Overall, SIP was a welcome addition to the operating system and has helped to protect the Mac operating system from being modified by malware and other threats.
How certain processes can bypass SIP
As mentioned, certain processes and apps are allowed to bypass SIP. One of these processes is system_installd, which has been entitled by Apple, and is thus able to do what it wants, when it wants, at least up to a point. That’s because system_installd is an Apple software installation daemon that’s called up when a software update or other installer needs to perform its functions, and it can in turn start child processes to handle specific tasks. These child processes are endowed with the same privileges as their parent—which in this case includes the entitlement to bypass SIP.
Many installers include post-install scripts that handle cleanup, setup, transfer of settings in case the install was an update, etc. When a post-install script wants to run, system_installd calls a shell named zsh (“Z shell”), which in turn looks for the file /etc/zshenv. This zshenv file (Z shell environment variables, or in other words, zsh settings) includes the post-install commands as instructed by the script.
Researchers found that planting a malicious /etc/zshenv file (which is in a folder that is not protected by SIP), could be a very effective way to infect a system with malware. Simply wait for an Apple installer to run, run commands from the malicious zshenv file, which could then run with the SIP bypass entitlement, and voilà! SIP bypassed.
Shrootless exploit demonstrated in a proof-of-concept
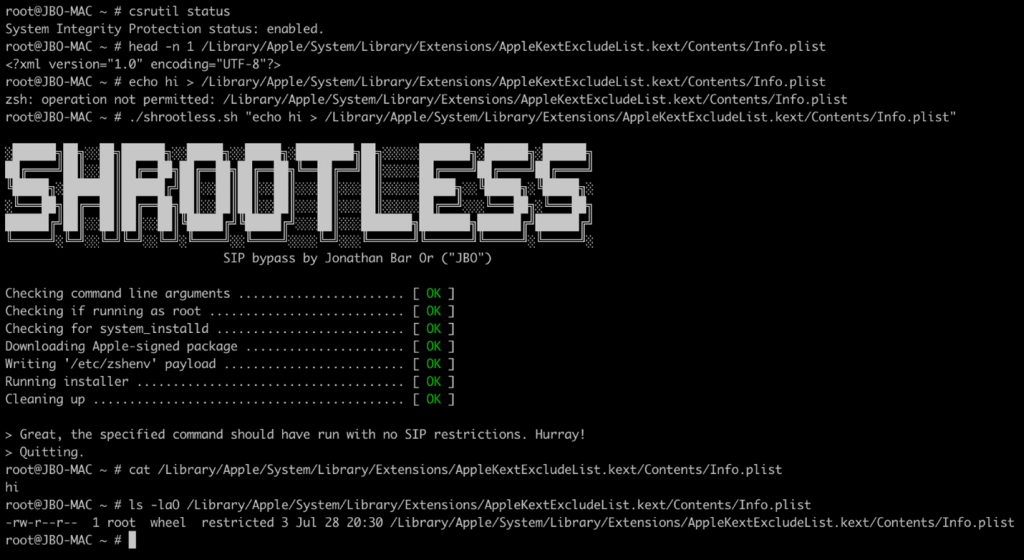
Microsoft’s Jonathan Bar Or, who discovered and wrote about the Shrootless vulnerability, set out to create a proof-of-concept (PoC) exploit. The process involved:
- Download an Apple-signed package (using
wget) that is known to have a post-install script - Plant a malicious
/etc/zshenvthat would check for its parent process; if it’ssystem_installd, then it would write to restricted locations - Invoke the
installerutility to install the package
The following image shows that Shrootless was able to override the kernel extension exclusion list (click to enlarge):
Jonathan goes on to note:
“During our research, we also found out that zshenv could also be used as a general attack technique besides being used for a SIP bypass. We discovered that /etc/zshenv has an equivalent for each user profile under ~/.zshenv, which has the same function and behavior but doesn’t require root permissions to write to.”
The zshenv file could be used either as a persistence mechanism (i.e. a way for malware to run again after a reboot) or an elevation of privilege mechanism.
Planting a malicious zshenv file could be very easily done by an installer, as the PoC shows. For any fake Flash Player installer or other piece of malware, if it asked for your user password, then it had enough privileges to replace the legitimate file with a malicious one.
Apple started using the zsh (Z shell) as a default, replacing the bash shell, in macOS 10.15 Catalina, so this vulnerability does not appear to be a problem for versions of macOS older than that. (However, macOS 10.14 Mojave and older are no longer receiving security updates and are no longer safe to use.)
Crisis averted; the good guys win this round
Upon discovery, Microsoft reported the Shrootless vulnerability to Apple. In turn, Apple fixed the vulnerability in macOS Monterey, Big Sur, and Catalina. Make sure you’ve installed the latest updates to ensure your Mac is protected.
A typical operating system is made up of thousands and thousands of files, all working together to bring you the end-user experience. The continued search for, discovery and investigation of potential vulnerabilities is what those with malicious intent—and those who seek to protect us—are constantly working on. Luckily in this case, the good guys got to it first!
 Because security is so complex, it’s important to take a layered approach, and use all the tools at your disposal. Intego VirusBarrier—part of the Mac Premium Bundle X9 security and utility suite—can protect your Mac from malware before it has a chance to try exploiting any vulnerabilities. Learn more and download a free trial today. And from November 19 until December 2, 2021, you can save up to 65% off during our Black Friday sale!
Because security is so complex, it’s important to take a layered approach, and use all the tools at your disposal. Intego VirusBarrier—part of the Mac Premium Bundle X9 security and utility suite—can protect your Mac from malware before it has a chance to try exploiting any vulnerabilities. Learn more and download a free trial today. And from November 19 until December 2, 2021, you can save up to 65% off during our Black Friday sale!
How can I learn more?
Although Apple did the right thing by patching all three currently supported macOS versions (Monterey, Big Sur, and Catalina), it’s important to note that Apple does not necessarily always patch all affected operating systems. For more on that subject, see Intego Chief Security Analyst Josh Long’s recent article about Apple’s patching policies:
Apple’s Poor Patching Policies Potentially Make Users’ Security and Privacy Precarious
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()