Security Bug in Safari Browsers Puts OS X and iOS Users at Risk
Posted on
by
Derek Erwin

Security researchers have discovered a serious Safari address-spoofing bug that can deceive users about the sites they’re visiting. The exploit works on fully patched versions of OS X and iOS, and could be used by cyber-criminals in phishing or malware attacks.
Deusen researchers have demonstrated a proof-of-concept exploit that tricks Safari users on iPhone, iPad and Mac into thinking they are visiting a known or trusted site, when in fact, Apple’s web browser is connected to an entirely different address, which could be used in phishing attacks to get login credentials or attempt to install malware.
The recently discovered bug can be seen in action on this site, where you will see your Safari address bar display “dailymail.co.uk,” even though the browser is displaying content from deusen.co.uk.
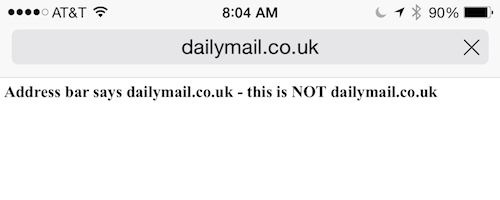 As you can see in the demo, attackers can set up a phishing page and then make the URL appear legitimate, but the address-spoof is not foolproof.
As you can see in the demo, attackers can set up a phishing page and then make the URL appear legitimate, but the address-spoof is not foolproof.
A quick test using Safari on the iPhone 6 Plus showed the page’s address bar repeatedly refreshed, which is unusual behavior for the web browser. Similar tests by Ars Technica, as reported by Dan Goodin, also showed the demo code is far from perfect: “On the iPad Mini Ars tested, the address bar periodically refreshed the address as the page appeared to reload. The behavior might tip off more savvy users that something is amiss.”
Most keen OS X and iOS users would likely notice something is off, however, as always the case, the oddity may go unnoticed by some users.
Furthermore, as referenced by Eduard Kovacs at Security Week, the JavaScript that the demo relies on shows that the PoC code is not very complex.
“The [PoC] code is very simple: webpage reloads every 10 milliseconds using the setInterval() function, just before the browser can get the real page and so the user sees the ‘real’ web address instead of the fake one,” explained Manuel Humberto Santander Peláez, handler at the SANS Internet Storm Center.
The script looks like this:
<script>
function f()
{
location="dailymail.co.uk/home/index.htm..."+Math.random();
}
setInterval("f()",10);
</script>
When you load a web page, it should load and stay as-is — easily verified by checking the URL and other details about the address by clicking on the address bar. If any web page causes your browser to crash or hang in spite of attempts to correct the issue, it’s best to not trust the page you are on and simply exit the tab or force-quit your browser.