Recommended + Security & Privacy
Rootkits Defined: What They Are and How They Can Be Used Maliciously
Posted on
by
Lysa Myers

If you’ve ever found yourself reading an article or watching a news segment on computer security, you’ve probably heard the word “rootkit” at some point. Those of you who read our first article on OSX/Crisis the other day certainly did. But you may be wondering what exactly is a rootkit? There is a lot of incorrect information floating around out there about what is and isn’t a rootkit. But that’s no surprise; when you have a new and highly technical subject like malware, information can really get mangled in translation.
So, what is a rootkit?
A rootkit is a piece of code that employs misdirection techniques involving software already on your machine to hide things, including itself. Rootkits are not backdoors, keyloggers or exploits, though these things may be associated with a rootkit. A rootkit may use an exploit (or for that matter social engineering or direct attacks) to get onto your machine. And once it’s there, it may hide a backdoor or a keylogger or any number of other things.
A rootkit is not inherently malicious, as a program could also be using rootkit techniques for protective measures in a beneficial way. Or it could be used in a way that’s questionable, especially when it’s not secured to keep other people from using it to hide (potentially bad) things. At this point, however, there is such stigma around saying something is using a rootkit that beneficial use is likely to remain rare. There are plenty of people who would argue that the redirection itself is malicious, as it’s kind of like reprogramming your computer to lie to you.
What’s the difference between a rootkit and malware?
The big difference between the ways a rootkit hides things and the way other malware hide is a little tricky. Regular malware will try to camouflage itself to look innocent, or to disable things (like AV software) that would help you identify the infection. Think of this as someone trying to break into a building by pretending to be a security guard, then tying up the real security guards and hiding them in a closet. Crude, but often effective.
Rootkits go one step further. They will add or replace code that would normally be trustworthy into hiding its presence. To stick with the break-in motif, it would be like the burglar had obtained an ID badge that allowed them in. They can do this on a few different levels, depending on how resistant they want to be against detection. These two different levels are called “Kernel Level” and “User Level.”
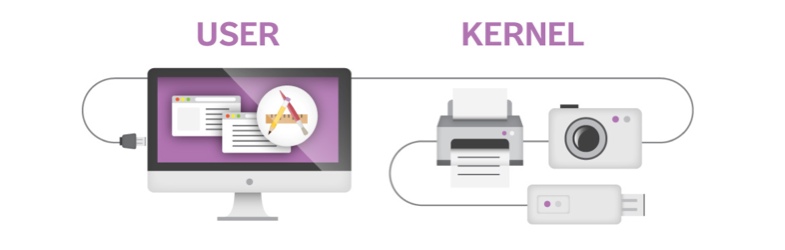
Obviously the User Level is the one you and I use. It’s the level at which most software works, and it’s the only level most users ever see; it’s the level of interaction between applications and the operating system. And it is a less-privileged level, which means the rootkit can only do a limited amount of hiding. But, frankly, this is all most rootkits need. It’s leaps and bounds more powerful than the vast majority of malware ever used, and most malware is unfortunately pretty darn successful at hiding without throwing the kitchen sink’s worth of tricks at the task.
The Kernel Level is the one at which the operating system interacts with hardware that plugs into your computer (like printers, video cards, digital cameras, etc). This is a very privileged level of access, and it’s very powerful. If you screw up something at this level, it can cause a lot of system instability and crashing. Even some anti-virus software has a hard time detecting rootkits once they’ve infected a system, because the rootkit is hiding itself at this lower level. (This is another one of those good reasons to make sure you’re using a complete security suite and updated virus definitions!)
To go back to our burglary analogy, the difference between levels is like having an ID badge that is only meant to pass visual inspection by a security guard versus having an ID badge that will fool a computerized card-reader too. Obviously the latter requires some serious time and skills that malware authors may not need or want to invest.
So, what should you take from this? Rootkits are a very powerful tool. They’re not used often, but when they are, they’re able to hide things from all but the most sophisticated tools and skilled users. Essentially, even the OS itself is fooled. Rootkits can hide files, network connections, user actions (like log entries or other data manipulation), among other things. They’re a very vivid example of the sort of sophistication security folks like to warn you about.
Further Reading: