Roku leaks 576,000 accounts—its second data breach of 2024
Posted on
by
Joshua Long

Streaming giant Roku announced that it has suffered its second data breach so far this year.
In the first data breach, which Roku acknowledged on March 8, attackers compromised more than 15,000 user accounts. The company stated that the breach was the result of a credential stuffing attack, also known as a password reuse attack. In other words, hackers tried username-and-password combinations that had leaked in past data breaches.
Roku stated on April 12 that hackers had accessed roughly 576,000 additional accounts in a second incident. The company claims to have determined this by closely monitoring account activity.
Between the two incidents, there were fewer than 400 cases where “malicious actors… made unauthorized purchases of streaming service subscriptions and Roku hardware products using the payment method stored in these accounts.” Roku claims that the attackers “did not gain access to any sensitive information, including full credit card numbers or other full payment information.” The company said that it has refunded or reversed all fraudulent charges.
What Roku did—and didn’t do—right
The bad
It’s unclear why Roku’s supposedly “close” monitoring did not enable the company to stop the second attack much sooner. Additionally, it’s unfortunate that Roku evidently didn’t significantly reduce the feasibility of credential stuffing attacks after the first incident.
Instead, the company blamed its users for their bad password hygiene. Roku claimed that “it is likely that login credentials used in these attacks were taken from another source, like another online account, where the affected users may have used the same credentials.”
The good
On the bright side, Roku said after the second incident that it had proactively enabled two-factor authentication (2FA) for all of its 80 million user accounts.
The next time users attempt to log in, they’ll get a verification link via e-mail. We’ll walk you through this process below.
How to set up two-factor authentication for your Roku account
In addition to using a separate, unique password for each of your online accounts, you should also use two-factor authentication (2FA; also called MFA for multi-factor authentication, or 2SV for two-step verification).
Most services make 2FA optional, but Roku now requires it. You should ideally enable 2FA for all of your accounts to add an additional layer of protection in case your password is ever exposed in a data dump.
Now whenever you try to sign into your Roku account, you’ll see a “Verify it’s you to finish signing in” screen. This screen shows you your registered e-mail address, to which a verification link is sent.
Next, check your e-mail and look for a brand new message from [email protected] with the subject, “Roku | Signing in?” The e-mail will look similar to the following:
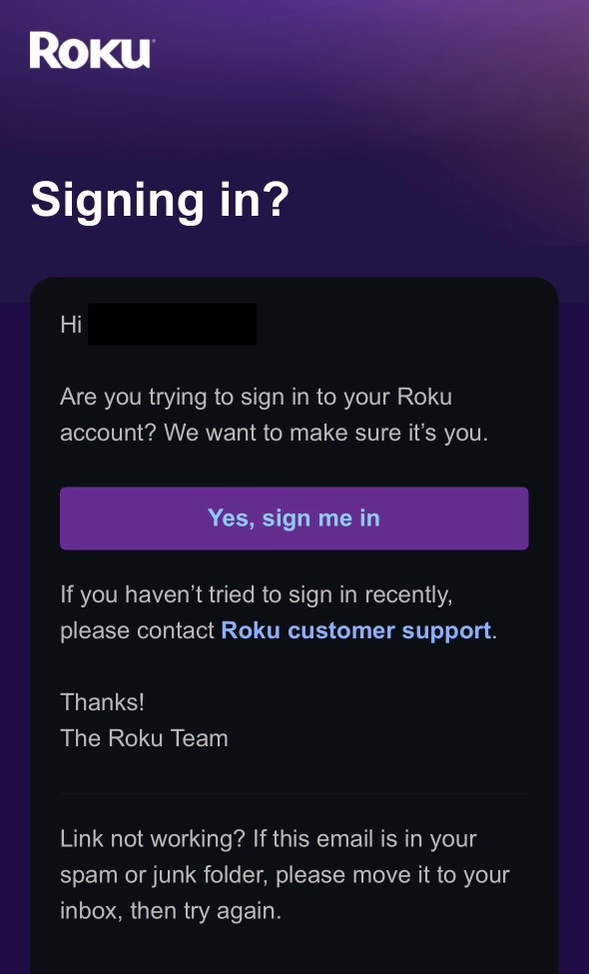
Roku’s “Signing in?” verification e-mail as of April 2024. Note that your first name will appear after “Hi” on the first line.
Note that you should only receive such an e-mail—and should only click or tap on the “Yes, sign me in” link—if you’re actively attempting to log in at that time. (Otherwise, it may be a phishing e-mail, or someone else may be trying to break into your account.)
The “Yes, sign me in” link begins with https://click.web.roku.com/. After clicking or tapping on the link, you’ll be redirected to a page hosted at https://my.roku.com/.
If the site asks you to change your password, verify that the domain in the address bar ends in “.roku.com” first. Otherwise, the page will automatically redirect to https://my.roku.com/dashboard.
Convenience is the enemy of security
Roku considers the ability to access your e-mail to be the “something you have” second-factor option. So unlike most sites, Roku doesn’t require you to configure an authenticator app or get a text message as your second factor.
This may seem convenient—but you’ll need to ensure you aren’t reusing the same password for both your e-mail account and your Roku account; if you are (and if you aren’t using 2FA for your e-mail account), then an attacker just needs to take an additional step to break into both accounts. As we’ve mentioned before, it’s crucial to never reuse any passwords and to always use 2FA.
How can I avoid falling victim to credential stuffing attacks?
Regardless of whether or not you have a Roku account, there are two important takeaways:
- Use unique passwords for each and every site. Never reuse a password.
- Use two-factor authentication wherever possible. Enable 2FA for every site that offers it.
These key points will help you avoid becoming a victim of future credential stuffing attacks. Be sure to check out the additional links below for more details.
How can I learn more?
We discussed the Roku data breaches on episode 340 of the Intego Mac Podcast.
We’ve previously covered: what 2FA is; why to avoid using SMS text messages for 2FA to prevent SIM swapping attacks; and how to use authenticator apps and physical security keys for 2FA.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()