Malware + Recommended + Security News
Researcher Demonstrates How Malware Can Bypass OS X’s “Completely Broken” Gatekeeper
Posted on
by
Graham Cluley

Virus Bulletin 2015, Prague – Researcher Patrick Wardle says he “loves his Mac, but it’s so easy to hack.”
At the VB2015 conference in Prague earlier today, Wardle explained to members of the security community how he had uncovered a way to easily waltz past one of the key safeguards that Apple built into its OS X operating system to block unauthorised code, downloaded from the internet, from running.
Generally, Gatekeeper does a reasonable job.
If an app is developed by an unknown developer, or has been tampered with en route to your computer via a man-in-the-middle attack over an unencrypted HTTP connection, then Gatekeeper is supposed to spot it and block it.
In this way, fake anti-virus attacks launched from websites that you might visit should be blocked and users are prevented from downloading and running bogus HD video codecs claiming to offer access to hardcore porn.
In its default setting, Gatekeeper restricts you to only running apps downloaded from the Mac App Store or digitally-signed with an Apple-approved key. If you’re feeling the need to be particularly secure, you can even change the setting to insist that only apps downloaded from the official app store are allowed.
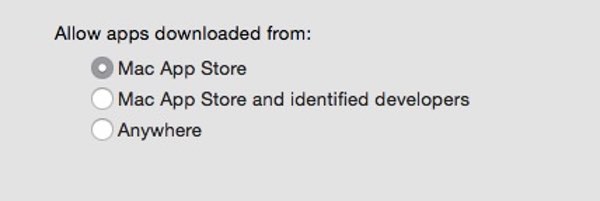
So far, so good.
But Wardle has uncovered a way to bypass Gatekeeper protection, even if you have configured your Mac computer’s security to choose the App Store-only setting.
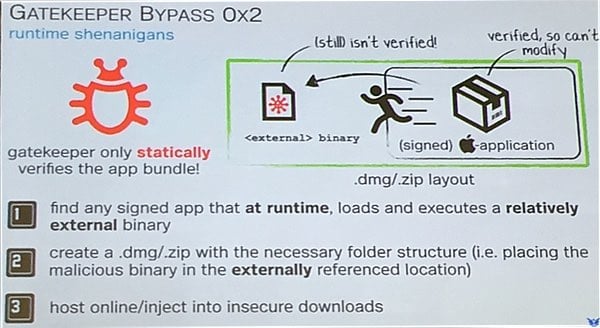
The trick is to use a legitimate app that already successful passes Apple’s Gatekeeper check, but that loads or runs code from the same folder, and bundling both into a disk image.
As the legitimate app has already been digitally-signed, Gatekeeper fails to check other content in the disk image that may have a malicious impact.
“If the application is valid – so it was signed by a developer ID or was (downloaded) from the Mac App Store – Gatekeeper basically says ‘OK, I’m going to let this run,’ and then Gatekeeper essentially exits,” Wardle told Ars Technica. “It doesn’t monitor what that application is doing. If that application turns around and either loads or executes other content from the same directory… Gatekeeper does not examine those files.”
Through this method, it’s easy to imagine how spyware could be implanted on a target’s computer or a remote backdoor trojan could be installed.
At the last-minute request of Apple, Wardle redacted the name of the legitimate app from his slides. Although, he pointed out, this was somewhat pointless as he could have performed the same attack with any number of other apps.
Wardle also described a theoretical attack where Photoshop could be bundled with poisoned plugins that automatically activated when the main app was run.
Wardle informed Apple about the vulnerabilities in Gatekeeper, and how they could be exploited, earlier this year — but, as more than 60 days had now passed, he felt that the time was right to make details of the flaws public.
In his presentation, Wardle suggested that Gatekeeper could be significantly improved if it attempted to validate all binary code at runtime (rather like how anti-virus software checks files each and every time they are run) rather than on one occasion after they are downloaded.
That would certainly be a step in the right direction for Gatekeeper, which Wardle describes as “trivial to bypass” and, in his opinion, “completely broken.”
So, if you’re worried about attacks like this happening on your Mac what can you do about it?
Firstly, you could choose to only download apps from the official Mac App Store. Depending on what apps you need on your Mac you may find that inconvenient, but it will offer a higher level of security, argues Wardle.
In addition, you could pressure your software vendor to provide app downloads via encrypted web connections (in other words, HTTPS rather than HTTP) as that will prevent an attacker from tampering with a download via a man-in-the-middle attack. Wardle said during his presentation that he was depressed by just how many software vendors, including security firms, still provided app downloads via HTTP.
Finally, I would recommend running an up-to-date anti-virus on your Mac. Although Wardle is not a fan of anti-virus software, per se (he is aware of their limitations and relies upon his technical skills and alternative tools to protect his Mac), he’s also not the typical user.
For most people, an anti-virus program run alongside Gatekeeper is a sensible step that can reduce the chances of your computer becoming infected — regardless of whether the malware was downloaded from the net or introduced to your Mac via a different route.