Privacy Exodus: spam delivers Mac spyware
Posted on
by
Joshua Long

Earlier this month, malware researchers discovered an interesting attack: a scam e-mail with a cleverly disguised Mac malware attachment.
Let’s take a look at the e-mail in question, the signs that indicate it’s a scam, and what the malware does if someone falls victim.
Scam E-mail Disguised as Legit Developer Update
At first glance, the e-mail may appear to be a legitimate software update notification from the developer of Exodus. The real Exodus app is a digital wallet designed to hold more than 90 varieties of cryptocurrency (such as Bitcoin, Ethereum, Litecoin, and Zcash).
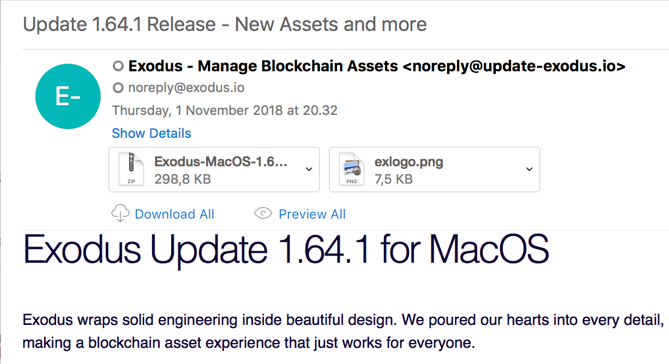
This fake Exodus e-mail has a harmful attachment. Screenshot: F. Vila
Unlike many scam and spam e-mails, this one has very few typos or glaring indicators that the e-mail may be fake. Even a close inspection will only reveal a few very minor textual issues: macOS is misspelled with a capital M, the From address has a different domain than the actual Exodus site, and the ad copy in the body of the e-mail promises “shorter release notes below” but doesn’t deliver. Frankly, all of those things are fairly passable and not necessarily indicative of a problem.
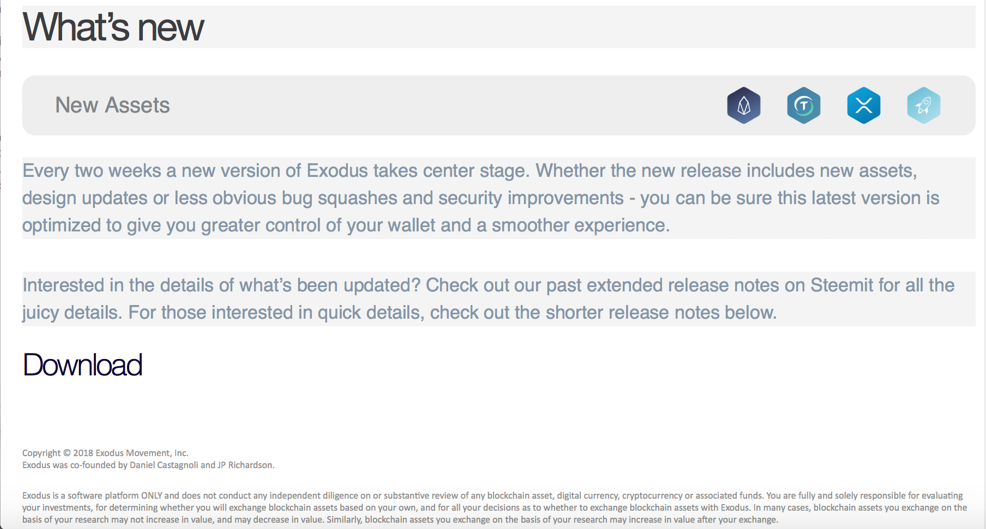
The scammer didn’t include “release notes below.” Screenshot: F. Vila
The biggest red flag is one of the e-mail attachments: a .zip file that supposedly contains an updater app (file name “Exodus-MacOS-1.64.1-update.zip”). I can’t recall ever seeing a developer distribute software updates to all of their users as a direct attachment to an e-mail, so this is sufficient cause for concern.
What’s Really In the Attachment?
![]() As you’ve probably guessed, the attachment doesn’t actually contain a software update from the developer of Exodus.
As you’ve probably guessed, the attachment doesn’t actually contain a software update from the developer of Exodus.
Rather than updating Exodus, the Trojan horse actually installs a copy of Realtime-Spy, a utility that allows someone to remotely monitor and spy on another computer. Realtime-Spy’s homepage claims that the software is “designed for parents and employers to legitimately monitor” computers they own.
According to Spytech, the developer of Realtime-Spy, the software supports Mac OS X 10.6 all the way through current versions of macOS.
What Can the Spyware Do?
According to Spytech, Realtime-Spy can log what applications you use, what sites you visit and for how long (including in private browsing sessions), and the approximate location of the computer. It can also record keystrokes and take continuous screenshots of the victim’s computer.
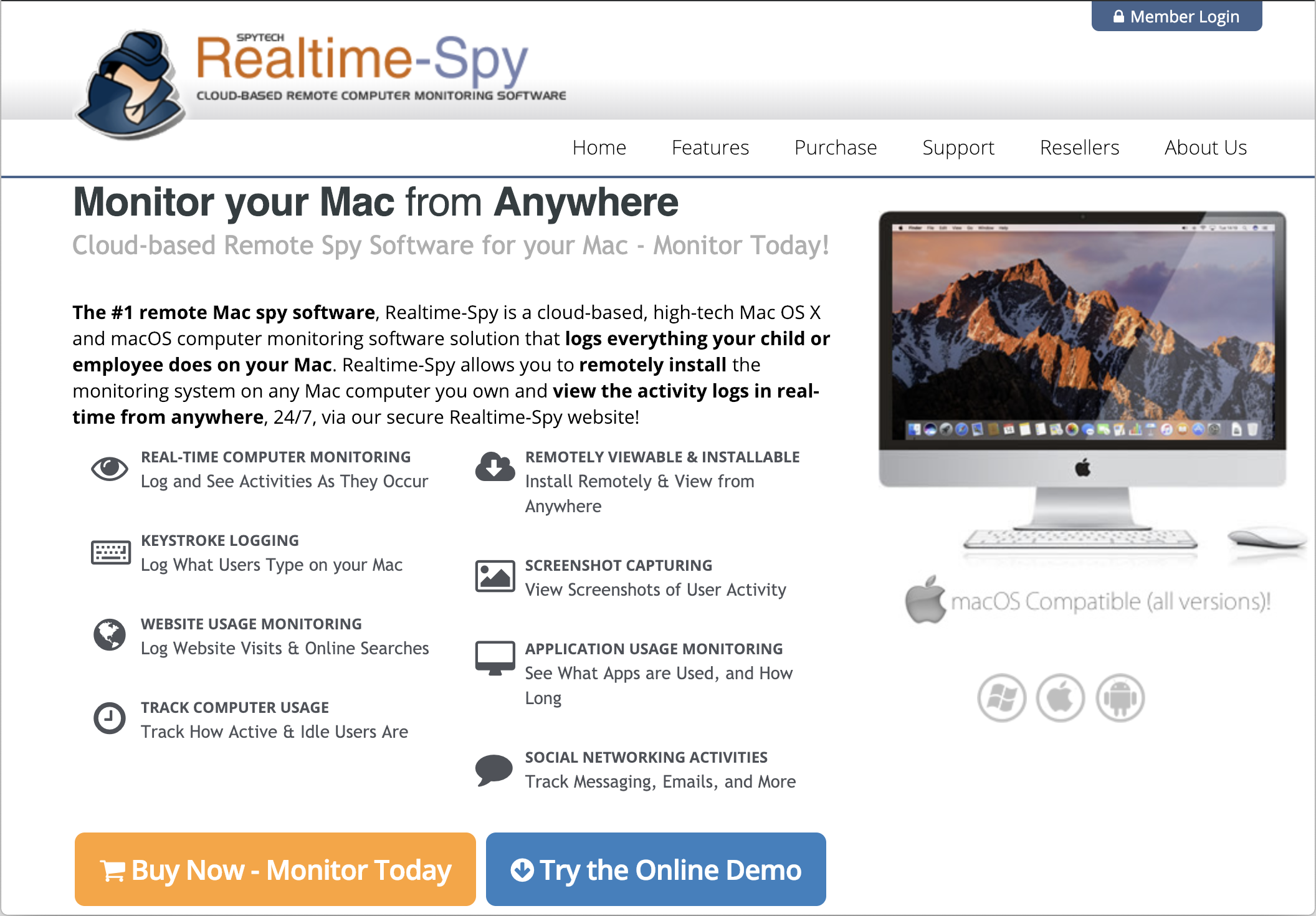
Realtime-Spy’s list of creepy features
For the person who deployed Realtime-Spy, all of these logs are supposedly available via an online interface with handy reports for each individual computer to which the user has deployed the spyware.
How Can Mac Users Stay Protected?
Intego VirusBarrier X9 and Flextivity detect and eliminate this malware, components of which are identified as Hacker Tool: OSX/RealtimeSpy and Keylogger: OSX/KeySpy.A.
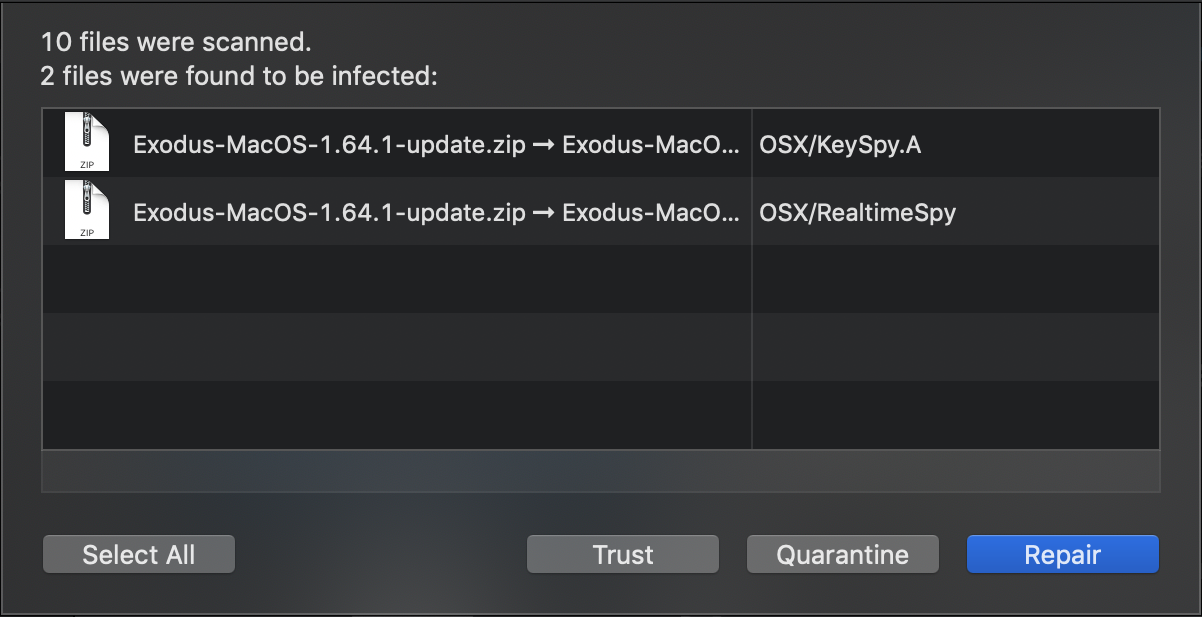
The e-mail attachment is blocked by Intego VirusBarrier X9.
Network administrators can monitor for traffic to realtime-spy-mac[.]com and search for inbound e-mails from update-exodus[.]io to find potentially infected computers.
How Can I Learn More?
 Each week we talk about the latest Apple security news on the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
Each week we talk about the latest Apple security news on the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
For a few additional technical details on this malware, you can refer to Frederic Vila’s write-up.