Poseidon macOS malware employs new tricks, targets Swiss Mac users
Posted on
by
Joshua Long

Poseidon macOS malware attempts to employ new stealer functionality. It has also been deployed in targeted attacks against Swiss citizens.
Regular readers of The Mac Security Blog know that stealer malware is all the rage these days. Stealers are a class of malware; they attempt to find and exfiltrate sensitive data from an infected computer.
The maker of a popular stealer malware family has recently rebranded as Poseidon. Under the hood, Poseidon looks and behaves much like existing AMOS malware. But what’s more interesting is that it is being used in malspam attacks against Swiss citizens.
Here’s what you need to know to avoid the latest macOS malware threat.
A brief history of Poseidon Mac malware
Atomic macOS Stealer (AMOS, or AtomicStealer) first surfaced in late April 2023, just over a year ago. At the time, a threat actor began selling it via Telegram as malware as a service, licensable for $1,000 per month.
Since then, we’ve seen lots of AMOS variants emerge. We wrote about later campaigns in September 2023 and February 2024, and we often discuss it on the Intego Mac Podcast.
In May, we wrote about a previously undocumented AMOS variant that Intego’s research team discovered. We also documented another variant, dubbed Cuckoo—one version of which our team unearthed as well.
Most often, AMOS malware is distributed through malicious Google Ads campaigns. These poisoned Google ads appear at the top of search results, where many people will see and click on them. In some cases, the ads are virtually indistinguishable from legitimate Google Ads run by the real software companies they mimic.
Poseidon is the latest variant or copycat of AMOS. A threat actor who goes by the name Rodrigo4 distributes it. (You can read more about Rodrigo4 in our later report about Banshee Stealer.)
From a technical standpoint, there’s one trait that distinguishes Poseidon from previous AMOS variants. That’s its alleged VPN configuration stealing functionality. Rodrigo4 claims that Poseidon can access and steal Fortinet and OpenVPN credentials from infected Macs. So far, we have not yet observed functional implementations of this capability in Poseidon samples.
What Poseidon variants have been observed so far?
Last month, Intego discovered the first macOS Trojan horse masquerading as the Arc browser. Malware researchers have observed Poseidon variants that also pose as Arc.
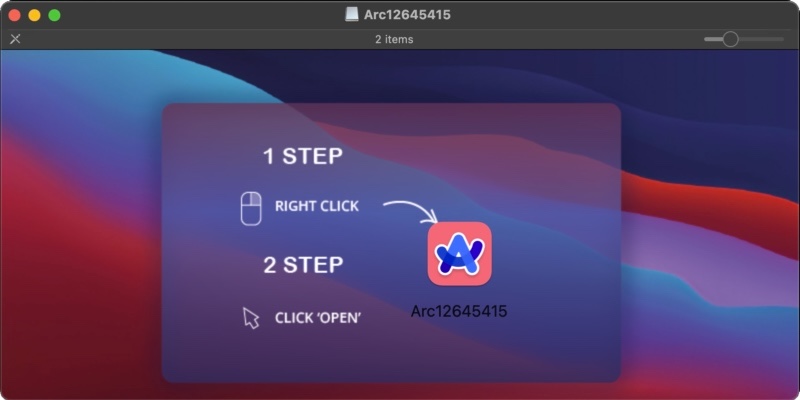
An in-the-wild Poseidon variant is disguised as Arc, an AI-infused Web browser.
Another Poseidon variant disguises itself as “AGOV Access.” It claims to be related to the Swiss government site agov.ch, which is a “public service login for Switzerland.”

Poseidon masquerades as a Swiss government app. Image credit: Archie
The real AGOV site currently displays a warning about this malware:
Beware of malware!
Cybercriminals are currently sending emails claiming to be from the Federal Administration and claiming, among other things, that the AGOV access app is available as a desktop application. If you click on the link in the mail, you are asked to install software. Please beware: this is malware that infects macOS systems. Delete the email immediately!
Interestingly, the Swiss National Cyber Security Centre (NCSC) even published its own write-up and technical details about this macOS malware and the associated malspam e-mail campaign.
Don’t “just Google it”
The Arc variant has been seen in the wild as part of a Google Ads poisoning campaign. Threat actors often pay Google for top placement, with sponsored ads disguised as real ads for legitimate software. These ads appear immediately above the actual search results; if you aren’t careful, you could inadvertently visit a malware distribution site instead of landing on the real software developer’s site.
We recommend that everyone get out of the habit of “just Google it” to find legitimate sites. Such habits often include clicking on the first link without giving it much thought, under the assumption that Google won’t lead them astray, and will give them the correct result right at the top. Malware makers know this, of course, and that’s why they’re paying Google for the number-one position.
Until or unless Google does a much better job of vetting its ads, a better practice than “Google it” would be to bookmark trusted sites whenever possible, and to go back to those bookmarks in the future.
And of course, as always, avoid clicking on links in e-mails as well.
How can I keep my Mac safe from similar malware?
If you use Intego VirusBarrier, you’re already protected from this malware. Intego detects these samples as OSX/Amos, OSX/Amos.ext, OSX/Amos.scpt, OSX/Stealer.ext, and similar names.
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s current Mac operating system, macOS Sonoma.
One of VirusBarrier’s unique features is that it can scan for malicious files on an iPhone, iPad, or iPod touch in user-accessible areas of the device. To get started, just attach your iOS or iPadOS device to your Mac via a USB cable and open VirusBarrier.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware.
Indicators of compromise (IOCs)
Following are SHA-256 hashes of malware samples from the Arc-wannabe AMOS malware campaign (the DMG, Mach-O, and AppleScript), as well as the aforementioned later variant of the AppleScript:
9760043ad36a34d6548cafe1e89cb53f6af76a28d492da37517d7cb1912eb154 a4d4bbb201f59f89ba25b011f6b3b50abc63025505e6b25e9be588d4d9d3544d 02dff37f35bf78407d2ac3407e9ae0d363aa0fafc21e0d4fbf6521e589fc4749 f4e770a4ae2b6521d7cb1aa7cdef35dbc78e7a8b0441fa60b6699ee63349daf2 3b9a16f85d648ff7c4d21a666e1b79c4e70025ffcb64e5168143faf7bbce4844 152f7d2b4f428fbb3586b99995cc6ca27ed3e6c4066ec511e1e2ba072392e2e0 00b60bb5d692a0e3637b296c4db52dbee017caa0828bc302fc3a3e6963f4f513 8bd2b88eb6ca23122dce6e02d362d1a0ae886dcb97492907a5672c8dd0f56dd2 7276c6c6bff30cc9ddd97f4cd3e33102017281ffa7e164819dddc0beb83bafcf 85371dc259945e1b27f72cd7f1bcf23d4cacac2100e8990efbc80b7020fe7640 a95b406a64f3a270338ccd9f4096c023046bad09670da3add6ed9b7ea4198820 c1693ee747e31541919f84dfa89e36ca5b74074044b181656d95d7f40af34a05 46b65c4f8179a6bf8bd32a5647009170b7a1256c674c680b78640c7e4fddec13 748a7efffe738497c188b44c09335da7f93683a7bf0bc2dacc0f08783b03ce8b 15b0d9e4f1258f647a9178a697edcb4526be442a8af5eb24092f8baa6b741761 ebea4e566da67b8329b56cd5678113de17ffcaf9bb292d8684a8886ae44482f8 474ee78c6636ee478ea7f4521559679fbc468bb326357737bfc465e63ed153fa 6427baa1ce5ba37ff6cf3fff79b543018a0a8e8f088c3f66afb24561e4e9de43* 935bab8750187b584e23fb8a522200bcdf526db3c7ece0c6e909ee6e48f4321f* f48c210d57d291b3d5ef4eba81f8134a79a153996ab8d6d60a10e11b93e3285c* 82bda195fd4b7dffab8543433b5feff47d5ed1c04e3c53c89f9f58fd47123393* *added to this list on August 28, 2024
The following domains, IP addresses, and download URLs have been used in connection with Poseidon malware campaigns:
nextbugs[.]com zestyahhdog[.]com arc-download[.]com arcthost[.]org agov-access[.]com agov-access[.]net agov-ch[.]com agov-ch[.]net register-agov[.]com extraiptv.giize[.]com ip.tvguzel[.]com tv.surebettr[.]com 37.27.82[.]196 79.137.192[.]4 186.2.171[.]60 tinyurl[.]com/ysufhn7t nextbugs[.]com/static/Launcher.dmg nextbugs[.]com/static/Setup.dmg 37.27.82[.]196/Arc12645413.dmg static.196.82.27[.]37.clients.your-server[.]de/Arc12645413.dmg zestyahhdog[.]com/Arc12645413.dmg www.zestyahhdog[.]com/Arc12645413.dmg shop.aishabaker[.]com/about/ 186.2.171[.]60/AGOV-Access.dmg agov-access[.]com/AGOV-Access.dmg agov-access[.]net/AGOV-Access.dmg agov-ch[.]com/AGOV-Access.dmg www.agov-ch[.]com/AGOV-Access.dmg agov-ch[.]net/AGOV-Access.dmg extraiptv.giize[.]com/AGOV-Access.dmg ip.tvguzel[.]com/AGOV-Access.dmg register-agov[.]com/AGOV-Access.dmg tv.surebettr[.]com/AGOV-Access.dmg
Network administrators can check logs to try to identify whether any computers may have attempted to contact one of these domains or IPs in recent weeks, which could indicate a possible infection.
Do security vendors detect this by any other names?
Other antivirus vendors’ names for this malware may include variations of the following:
A Variant Of OSX/PSW.Agent.BN, A Variant Of OSX/PSW.Agent.CD, DMG/ABTrojan.CVEI-, DMG/ABTrojan.GJVR-, Gen:Variant.Trojan.MAC.Stealer.35 (B), HEUR:Trojan-PSW.OSX.Amos.gen, HEUR:Trojan-PSW.OSX.Amos.v, HEUR:Trojan-PSW.OSX.Amos.x, IOS/ABTrojan.JMRU-, IOS/ABTrojan.MNGB-, IOS/ABTrojan.UVLX-, Mac.Stealer.43, MAC/Agent.BN!tr, MacOS:Agent-ANG [Trj], MacOS:AMOS-I [Trj], MacOS:AMOS-O [Trj], MacOS/ABTrojan.EHNK-, MacOS/ABTrojan.GIJU-, MacOS/ABTrojan.MKHZ-, MacOS/ABTrojan.VDPM-, MacOS/ABTrojan.XBFH-, Malware.OSX/Agent.xlntn, Malware.OSX/AVA.Agent.kweyc, Malware.OSX/AVF.Agent.zxgsr, Malware.OSX/AVF.Agent.zxgss, Malware.OSX/AVI.Agent.eakmx, Malware.OSX/GM.Agent.UC, Malware.OSX/GM.Amos.QS, NetWorm ( 0040f4ed1 ), OSX.RodStealer, Osx.Trojan-QQPass.QQRob.Dkjl, OSX.Trojan.Gen, OSX.Trojan.Gen.2, OSX/Agent.BN!tr.pws, OSX/Agent.BO!tr.pws, OSX/Agent.CD!tr.pws, OSX/Agent.xlntn, OSX/GM.Agent.UC, OSX/GM.Amos.QS, OSX/InfoStl-DH, OSX/PSW.Agent.BN, OSX/PSW.Agent.BO, PoseidonStealer, Trojan ( 0040f4e71 ), Trojan-Dropper.OSX.Agent, Trojan-Spy.OSX.Agent, Trojan-Spy.OSX.Amos, Trojan:MacOS/Multiverze, Trojan.Generic.36478898 (B), Trojan.Generic.36478899 (B), Trojan.Generic.D22C9FB2, Trojan.Generic.D22C9FB3, Trojan.Generic.D45EA4C5, Trojan.Generic.D45EAE22, Trojan.GenericKD.73311429 (B), Trojan.GenericKD.73313826 (B), Trojan.MAC.Generic.119357 (B), Trojan.MAC.Generic.119358 (B), Trojan.MAC.Generic.119365 (B), Trojan.MAC.Generic.119919 (B), Trojan.MAC.Generic.119920, Trojan.MAC.Generic.D1D23D, Trojan.MAC.Generic.D1D23E, Trojan.MAC.Generic.D1D245, Trojan.MAC.Generic.D1D46F, Trojan.OSX.Amos.i!c, Trojan.OSX.Psw, Trojan.OSX.Stealer.i!c, Trojan.Trojan.MAC.Stealer.35, Trojan[PSW]/MacOS.Amos, Trojan[stealer]:MacOS/Amos.v, Trojan[stealer]:MacOS/Amos.x, UDS:Trojan-PSW.OSX.Amos.gen, UDS:Trojan-PSW.OSX.Amos.v, Win32.Troj.Undef.a
How can I learn more?
Be sure to check out Intego’s previous Mac malware articles from 2024 and earlier.
For more information about Poseidon, you can read Moonlock Lab’s X thread about Poseidon, Jérôme Segura’s write-up about the Arc variant, Archie’s X post about the AGOV variant, and the Swiss NCSC’s write-up about the AGOV variant and their IOCs list.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()