Porn blackmail “sextortion” emails: Have you been hacked? A new scam
Posted on
by
Kirk McElhearn and Joshua Long

Malicious spam emails claiming that your computer has been hacked—and demanding you pay a ransom to stop them from distributing your browsing history and videos of you engaging in activities that you would like to keep private—are not new.
It’s a type of scam that can earn money for the scammers, if victims are convinced that they were hacked. But, in reality, it’s unlikely that any such hack has taken place.
Let’s discuss a novel attack that we’ve seen in the wild recently, so you’ll know what to look for.
A new porn blackmail email referencing Pegasus spyware
A new porn blackmail email has been going around; it has only been spotted in the past several weeks. To understand why these emails are fake, we’re going to examine the text of this email and explain why its claims are false.
Subject: You have been hacked
That’s a cleverly deceptive subject line; most people will open and read the email.
Hello pervert, I’ve sent this message from your iCloud mail.
This strong first sentence grabs the reader’s attention. The “From:” address is spoofed (falsified), so has the appearance of having been sent from the recipient’s account.
I want to inform you about a very bad situation for you. However, you can benefit from it, if you will act wisеly.
I’m not sure how the recipient can benefit, but I’ll read on.
Have you heard of Pegasus? This is a spyware program that installs on computers and smartphones and allows hackers to monitor the activity of device owners. It provides access to your webcam, messengers, emails, call records, etc. It works well on Android, iOS, and Windows. I guess, you already figured out where I’m getting at.
What is Pegasus spyware? Can hackers use it against me?
Pegasus spyware is, indeed, quite powerful. It is used by nation-state level threat actors to target specific individuals, and it usually spreads through highly targeted attacks. (Read this article where we explain how Pegasus is used. And here’s another email scam claiming to use Pegasus from 2021.) However, this is not a tool that random hackers can access.
In addition, Pegasus, one other similar types of spyware, exploit “zero-day” vulnerabilities in operating systems; these are newly discovered vulnerabilities that the developer, such as Apple, hasn’t yet patched. Apple regularly issues security updates, specifically for the types of vulnerabilities used to infect devices with this type of spyware.
It’s been a few months since I installed it on all your devices because you were not quite choosy about what links to click on the intеrnеt. During this period, I’ve learned about all aspects of your private life, but one is of special significance to me.
I’ve recorded many videos of you j**king off to highly controversial рorn videos. Given that the “questionable” genre is almost always the same, I can conclude that you have sick реrvеrsiоn.
It’s extremely unlikely that some hacker or malware has activated your camera without your knowledge if you’re using a Mac or iPhone; if that had happened, you would have seen a circle of green light next to the front-facing camera. And on both platforms, you have to give apps permission to use your camera in the first place.
Threats of exposing the user’s activity to friends, family, and coworkers
Now we get to the heart of the email: an accusation of activities that the recipient might want to hide:
I doubt you’d want your friends, family and co-workers to know about it. However, I can do it in a few clicks.
That’s the threat. Some people may have engaged in the type of activities the email discusses and may feel that they are at risk. But can the hacker do what they claim?
Pegasus primarily targets and infects smartphones running iOS or Android. The hacker says it works on Windows, but there aren’t any known variants that infect Windows PCs or Macs. There are other types of spyware, but if you are careful in your Internet use, and you use antivirus software such as Intego’s VirusBarrier X9 for Mac or Intego Antivirus for Windows, you’re protected from this type of malware.
Can a hacker get all your contacts on WhatsApp, Telegram, Instagram, and Facebook?
Next, the email makes claims about being able to contact everyone you know:
Every number in your contact list will suddenly receive these vidеоs– on WhatsApp, on Telegram, on Instagram, on Facebook, on email – everywhere. It is going to be a tsunami that will sweep away everything in its path, and first of all, your fоrmеr life.
While this creative writing may be convincing, the threat isn’t very plausible. It could hypothetically be possible, if someone had actually installed spyware that can record your keystrokes, or stealer malware to exfiltrate your app data. But even then, it’s hard to sort out all those keystrokes to find your credentials for each of the services they named. And while stealer malware is rampant on Macs and Windows PCs, it’s less common on Android, and least common on iPhone. Again, the average cybercriminal doesn’t have access to really powerful mobile phone spyware like Pegasus.
It’s worth noting that the threat could be a little more plausible if you follow the bad practice of reusing the same password across multiple sites; this is why it’s so important to use a trusted password manager and unique passwords instead.
Don’t think of yourself as an innocent victim. No one knows where your реrvеrsiоn might lead in the future, so consider this a kind of deserved рunishmеnt to stop you.
I’m some kind of God who sees everything. However, don’t panic. As we know, God is merciful and forgiving, and so do I. But my mercy is not free.
Delusions of grandeur, but with the carrot of offering forgiveness. For a price…
Transfer 700 USD to my Litecoin (LTC) wallet: REDACTED
The “sextortion” blackmail scam
This is the definition of “sextortion”: a form of blackmail in which sexual information, images, or videos are used to extort money from the victim. Sextortion can be a real problem for someone who has ever shared nude images with someone who later abused them. However, this sort of email is a scam; it’s not claiming to have images that you shared while sexting; it’s claiming to have monitored your activities.
The average computer user has no idea what Litecoin is. They might have heard of Bitcoin, and there are hundreds of alternative cryptocurrencies.
Interestingly, while cryptocurrency transactions are anonymous, blockchain records are public; so by looking up the address in the email, one can see how much this scammer has earned so far:
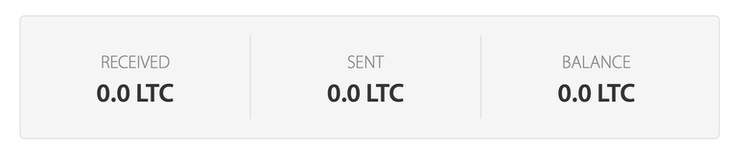
Once I receive confirmation of the transaction, I will permanently delete all videos compromising you, uninstаll Pegasus from all of your devices, and disappear from your life. You can be sure – my benefit is only money. Otherwise, I wouldn’t be writing to you, but destroy your life without a word in a second.
It goes without saying, but it would be unwise to believe that an unethical blackmailer would be completely honest and true to their word.
I’ll be notified when you open my email, and from that moment you have exactly 48 hours to send the money. If cryptocurrencies are unchartered waters for you, don’t worry, it’s very simple. Just google “crypto exchange” or “buy Litecoin” and then it will be no harder than buying some useless stuff on Amazon.
It would be possible in a standard HTML email to include a remotely loaded image, even a hidden one (an invisible pixel); unfortunately, Gmail and most mail apps default to automatically loading all remote images in emails. But in this case, the scam email we observed was sent as plain text, so there would have been no way for a supposed hacker to know when it was opened.
Don’t buy cryptocurrency for cybercriminals
It is relatively easy to buy cryptocurrencies; you can use a credit card. But there’s the risk of ending up on a scam site that records your credit card number, and, well, you can see where that is going…
I strongly warn you against the following:
Do not reply to this email. I’ve sent it from your iCloud mail.
Do not contact the police. I have access to all your devices, and as soon as I find out you ran to the cops, videos will be published.
Don’t try to reset or destroy your devices. As I mentioned above: I’m monitoring all your activity, so you either agree to my terms or the vidеоs are published.
Also, don’t forget that cryptocurrencies are anonymous, so it’s impossible to identify me using the provided address.
Those are the usual threats of blackmailers and kidnappers: don’t go to the police, or else.
If you did have Pegasus or other spyware on a device, it would be deleted by resetting the device to factory settings, or erasing a Mac’s drive.
Can hackers monitor everything you do online?
The bit about “monitoring all your activity” is overkill; because while it may be possible to install Pegasus on one device, getting it on multiple devices is difficult. And, again, Pegasus in particular is designed to infect phones, not computers.
It would take an extraordinary amount of effort and hacking skills to somehow infect multiple devices, with a separate kind of malware on each. And it’s very difficult to actually install malware on an iPhone, so such claims are pretty sketchy and implausible.
Good luck, my perverted friend. I hope this is the last time we hear from each other.
And some friendly advice: from now on, don’t be so careless about your online security.
This is the only true statement in the email; you need to take your online security seriously. Even though this is a scam, don’t click on random links in emails, don’t visit dodgy websites, and don’t reuse passwords, which could allow hackers who acquire databases of credentials leaked from websites to access your important accounts.
Beware of scams, and protect your devices and accounts
This sort of webcam blackmail is not new, and suggesting that Pegasus was used can scare people who may have read about that spyware in the news. You need to know that they are scams, and that they use social engineering to try to convince you that you have been hacked.
Malware that infects smartphones, especially iPhone, is rare. It’s more realistic that your computer (e.g. a Mac or Windows laptop or desktop) may have been hacked or infected by some malware. It’s true that some malware can activate a computer’s camera and microphone. You can scan your Mac or Windows computer with Intego antivirus software to check whether or not it’s infected.
4 key tips for protecting your online privacy and security
Here are four crucial things you should do to ensure that you’re keeping yourself safe from hackers and spyware.
1. Keep your operating system and apps updated
The most important thing you can do to protect your online security is to keep all your devices updated with the latest operating system.
Don’t use iPhones, Macs, or iPads that are so old that Apple no longer issues security updates for their operating systems. Using an outdated OS means your device is missing critical security patches; these often include fixes for vulnerabilities that hackers are already exploiting in the wild.
2. Use unique passwords everywhere
Use a unique password for every site, and keep track of them using a trusted password manager. This helps ensure that you can’t be hacked through credential stuffing attacks, where cybercriminals use leaked passwords from data breaches to break into accounts.
3. Use antivirus software from a company you can trust
Be sure to install anti-malware protection software, such as VirusBarrier X9 for Mac, or Intego Antivirus for Windows, in case you really do end up with a malware infection (spyware, data stealers, or otherwise). Reputable antivirus software can clean existing malware infections, and it can prevent future infections as well.
4. Stay informed via e-mail and social media
Last but not least, stay informed by subscribing to our free e-mail newsletter. You’ll also want to follow Intego on social media and enabling notifications. Staying up to date about the latest scams and threats will help you be prepared when facing dangerous situations online.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()