Malware + Recommended + Security News
OSX/Proton Malware is Back! Here’s What Mac Users Need to Know
Posted on
by
Jay Vrijenhoek

Last May, a download server of popular video encoding software, called Handbrake, was compromised by malware. Users downloading Handbrake at the time got not only the Handbrake application but also a nasty malware, called OSX/Proton.
Security researchers on welivesecurity published the discovery of yet another compromised download server distributing infected software with OSX/Proton malware. This time, Eltima, the makers of the Elmedia Player software were targeted. The trojan was found, reported and removed from the servers all on the same day, but it is currently unknown how long it was available or how many users may be affected.
Intego VirusBarrier identifies and eradicates the malware as OSX/Proton.C.
What is the infection vector?
Only those who downloaded Elmedia Player from their server (https://mac.eltima.com/elmedia-player-download.html) received the malicious application. It was not distributed on any other websites, as far as we know, and the App Store version was not affected. Malware researcher “noar” (@noarfromspace) pointed out that Eltima’s Folx application was also affected, which has since been confirmed.
Well done @marc_etienne_ @michalmalik There is also Flox 6257ccd437cdbc5a93a535ecb4bcae37e7a540dc5abd61ca3ceb23bafadb3fe1 https://t.co/UVDXa6432Z
— noar (@noarfromspace) October 20, 2017
How does Proton malware install?
The Elmedia Player application arrives in a .dmg file, as expected, and upon opening the file, nothing suspicious can be seen. The user will drag Elmedia Player to their Applications folder and launch it.
At this point OSX/Proton is extracted and launched in the background and a name/password window will pop up.
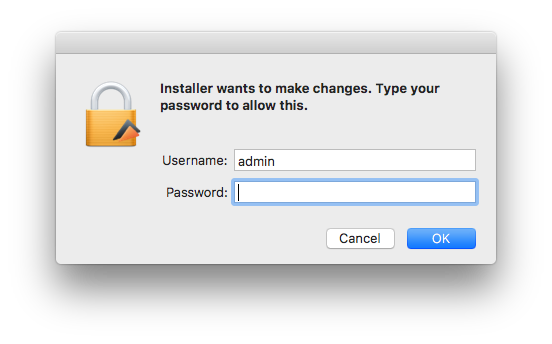
This is not Elmedia Player asking, it is OSX/Proton; as a result, entering the administrator name and password will give the malware all the access it needs. A backdoor will be installed on the system and is kept alive with the following files:
- /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist
- /Library/.rand/updateragent.app
What can OSX/Proton do?
Described as “a backdoor with extensive information stealing capabilities,” OSX/Proton can perform the following commands when received from the Command & Control (C&C) server:
| copy | copy file locally |
| create | create directory or file locally |
| delete | delete file locally |
| download | download file from a URL |
| file_search | Search for files (executes find / -iname \”%@\” 2> /dev/null) |
| force_update | Self-update with digital signature validation |
| phonehome | |
| remote_execute | Execute the binary file inside a .zip file or a given shell command |
| tunnel | Create SSH tunnel using port 22 or 5900 |
| upload | Upload file to C&C server |
Additionally, the following information can be collected/extracted:
- Operating system details: hardware serial number (IOPlatformSerialNumber), full name of the current user, hostname, System Integrity Protection status (csrutil status), gateway information (route -n get default | awk ‘/gateway/ { print $2 }’), current time & timezone
- Browser information from Chrome, Safari, Opera and Firefox: history, cookies, bookmarks, login data, etc.
- Cryptocurrency wallets:
- Electrum: ~/.electrum/wallets
- Bitcoin Core: ~/Library/Application Support/Bitcoin/wallet.dat
- Armory: ~/Library/Application Support/Armory
- SSH private data (entire .ssh content)
- macOS keychain data using a modified version of chainbreaker
- Tunnelblick VPN configuration (~/Library/Application Support/Tunnelblick/Configurations)
- GnuPG data (~/.gnupg)
- 1Password data (~/Library/Application Support/1Password 4 and ~/Library/Application Support/1Password 3.9)
- List of all installed applications.
It appears this instance of OSX/Proton can also run on OS X versions 10.7 Lion and newer.
Should Mac users be concerned about Proton?
If you have downloaded and installed Elmedia Player on or before October 19, before 3:15PM EDT, welivesecurity noted that you are likely compromised. Unfortunately, Eltima does not list hashes on their download page, so a user cannot compare the hash of the downloaded file — this leaves users unable to verify the download. More information about hash checksums and how to use them can be found in this article.
As mentioned the last time we covered OSX/Proton:
What is worrying, however, is the way the attackers went about this. As with Transmission, not once but twice, the download server was compromised and the application available for download was replaced with a malicious one. Going after servers, which are typically not updated or patched as often as they should be, will result in less users downloading your malware, but the fact that it comes from a trusted source will make those users not suspicious at all. If a user is not suspicious, they won’t go looking for malware, and malware that goes undetected longer is typically more successful.
If this becomes a trend, and even the servers of the trusted source can no longer be trusted, we may very well be in trouble.
I would not call this a trend just yet, but it certainly won’t be the last time this supply-chain attack method is used. If a website doesn’t list checksums for their files, contact the developer and request those checksums before downloading a file. Without it, there really is no way to know if you’ve downloaded the file you came for or if the file was modified to be malicious.
Apple has revoked the certificate that was used to sign these malicious applications.
Developer ID Application: Clifton Grimm (9H35WM5TA5)
How to tell if your Mac is infected (and removal instructions)
Open Activity Monitor and search for a process named “updateragent.” If this process is running, your Mac is infected.
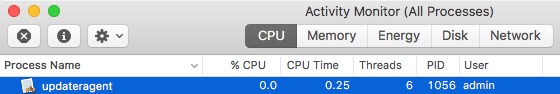
Click the process, and then close it with the X button in the menu bar.
To clear the infection off your Mac, browse to the following folders and trash the following files:
- Applications – Delete the Elmedia Player application.
- Library > LaunchAgents > com.Eltima.UpdaterAgent.plist – Delete this file.
To manually check for the invisible files OSX/Proton placed, you first need to make invisible files visible in the Finder. In macOS Sierra and High Sierra this can quickly be done with the following key combination:
Command-Shift-. (period)
For older OS X versions this can be done by typing the following commands in the Terminal app:
$ defaults write com.apple.Finder AppleShowAllFiles true
$ killall Finder
When done, enter the same commands but change “true” to “false”.
With the hidden files now visible, check both the root library and the user library for these files:
- tmp > Updater.app – Delete this file, if present (it may no longer be).
- Library > .rand – Delete this directory, or;
- Library > .rand > updateragent.app – Delete the application
With those files deleted, empty the trash and restart your Mac. Double-check the same locations again after the restart to ensure the infection is indeed cleared. If a warning shows that some items cannot be deleted, because they are in use, you’ll be able to empty the trash after the restart.
For Intego’s Mac anti-virus customers, protection comes in the form of updated malware definitions, which will detect and remove all of the Proton files. Proton components are detected by Intego VirusBarrier as OSX/Proton.C.
How to protect yourself from Proton
When the official server of the trusted source has been compromised, and the malware is coded to act much like the real application, there is very little to warn you something is amiss. Verifying your downloads will be the only way you can be sure the download was not compromised. Using the built-in updater, if an application provides one, is typically the best way to receive updates for an application.