OSX/Crisis Has Been Used as Part of a Targeted Attack
Posted on
by
Lysa Myers
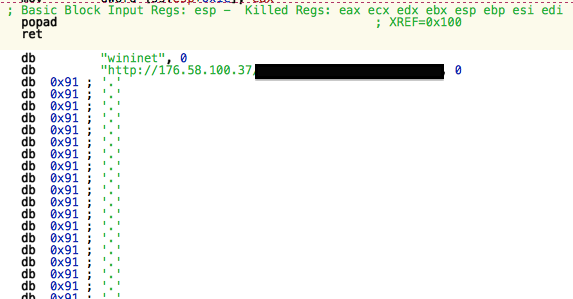
New information about the OSX/Crisis samples we spotted on VirusTotal is continuing to come to light. It turns out that the samples were submitted by a group of security researchers from DefensiveLab. They were submitting the files on behalf of a customer who was infected by the Trojan. The customer is a Moroccan journalist, and it appears that this infection is part of a larger attack that is being targeted against a group of independent Moroccan journalists who received an award from Google for their efforts during the Arab Spring revolution.
Ten days ago, the customer received an email from an unknown Yahoo email address informing the group about a new scandal with a link to a Word document called “scandale.doc”. At this same website, the previously identified Java applet attempted to install. The document contains a known Flash exploit and shellcode that it uses to connect to the same IP address as mentioned in our first Crisis article, in order to download what appears to be another DOC file. At the time of writing, this file was not accessible, so we cannot be sure what this is intended to contain. This exploit only works on Windows systems, so this attack would not be successful on OS X.
It’s interesting that this has come to light in such close proximity to discussion of the FinFisher Spy that has been used to target Bahraini activists. Such activities have been going on, on both OS X and Windows systems, for a while. One such example is the Tibet malware family. But it appears that such politically motivated attacks are either becoming more common, or being identified by their victims more often.