OSX/Calisto Mac malware masquerades as Intego software
Posted on
by
Joshua Long
Every so often, a new piece of malware comes along that tries to deceive victims by disguising itself as legitimate anti-malware software from a reputable company. A recent example was Proton malware masquerading as Symantec software in November.
A variant of the Proton malware family was recently discovered—a predecessor, in fact, dubbed OSX/Calisto—and this time, the malware fraudulently disguises itself as an Intego software installer.
What Does OSX/Calisto Do?
 The malware attempts to do a number of things to a victim’s Mac, including:
The malware attempts to do a number of things to a victim’s Mac, including:
- steal a user’s local administrator username and password
- install backdoor malware and enable remote administration tool (RAT) capabilities
- steal passwords and other data from the Keychain
- extract history, bookmarks, and cookies from Google Chrome
- phone home to a (now defunct) command and control server
Like OSX/Coldroot, it also attempts to directly modify TCC.db, an Accessibility database that tracks special permissions that the user has granted to apps, which no third-party software should ever attempt to directly alter.
The malware’s code contains hints of capabilities that were under development but not yet completed, such as attempting to erase every file on the Mac’s boot drive.
How Was OSX/Calisto Discovered?
Interestingly, the malware was first uploaded to VirusTotal, a multi-engine malware scanning service, on August 2, 2016—nearly two years ago. Given that the malware disguises itself as the X9 version of Intego software, which was announced on June 20, 2016, the malware was likely developed within that six-week period.
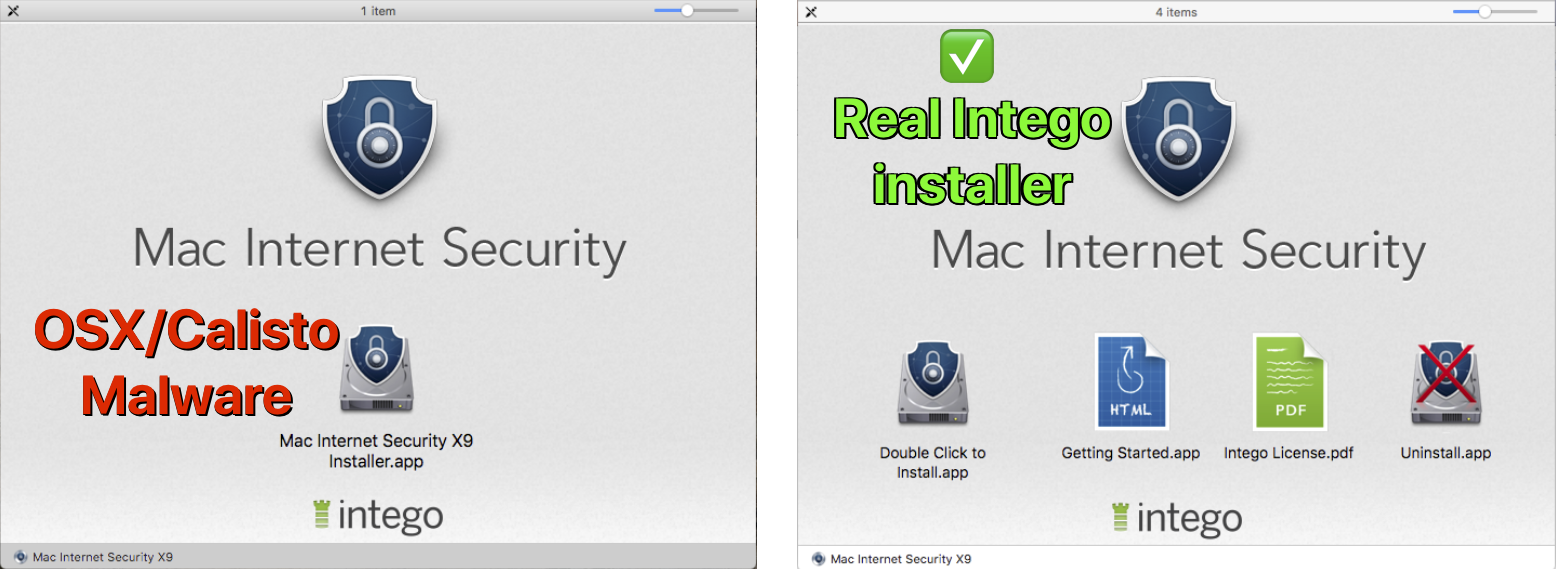
The OSX/Calisto malware disk image (left) falsely claims to be Intego software, but excludes files that come with the real Intego installer. Image: Securelist
For nearly two years after the samples were uploaded to VirusTotal, their harmful nature went undetected by every major antivirus engine, only recently being analyzed by malware researchers and identified as malicious.
Was Intego Hacked?
No. Intego servers were not hacked, and no source code was stolen from Intego. Anyone who downloaded an installer from Intego’s site is safe.
Unfortunately, it’s fairly easy for any attacker to create fraudulent software that looks nearly identical to the legitimate version, or to hijack someone else’s software and embed malware into it—and that appears to be exactly what the creators of OSX/Calisto did.
For this reason, it’s best to avoid obtaining software from third parties such as BitTorrent.
Whenever possible, obtain your software directly from Apple’s App Store or a trusted software developer’s official site. And never install pirated, cracked, or other illegally or questionably obtained software, which is significantly more likely to contain malware.
Developers’ official sites and even the App Store aren’t impervious to attacks, but they’re generally much safer than other software download sources.
Is My Mac Infected?
It’s fairly unlikely that you’ll find this malware in the wild today given how long ago it was first uploaded to VirusTotal. It’s possible that the malware was never very widespread, if it ever made it into the wild at all.
![]() Malware developers sometimes upload their software to VirusTotal simply to check whether or not their latest sample is identified by any major antivirus vendor as malicious. While it’s unclear whether or not that’s the case for OSX/Calisto, it’s possible that it may have simply been a prototype of OSX/Proton that may never have been distributed publicly.
Malware developers sometimes upload their software to VirusTotal simply to check whether or not their latest sample is identified by any major antivirus vendor as malicious. While it’s unclear whether or not that’s the case for OSX/Calisto, it’s possible that it may have simply been a prototype of OSX/Proton that may never have been distributed publicly.
 Regardless of how pervasive the malware was, if you’re a user of Intego VirusBarrier X9—assuming you downloaded a legitimate copy from Intego—your Mac is already protected from this threat, and any existing infection will automatically be identified as OSX/Calisto and exterminated.
Regardless of how pervasive the malware was, if you’re a user of Intego VirusBarrier X9—assuming you downloaded a legitimate copy from Intego—your Mac is already protected from this threat, and any existing infection will automatically be identified as OSX/Calisto and exterminated.
If you aren’t currently running anti-virus software on your Mac, you can scan your computer with VirusBarrier Scanner, available for free in the Mac App Store. (Later, you may want to read about the benefits of using an anti-malware suite with real-time scanning.)
If your Mac has ever been infected with OSX/Calisto or an OSX/Proton variant, you’ll want to clean up any data folders and files that may have been left behind, as they may contain your passwords and other sensitive information in plain text. As noted by researcher Thomas Reed, a future attack against your computer could leverage the information contained in those files if they’ve been left behind by a malware removal tool.
You can copy and paste the following command into Terminal to remove those fragments from your system if they exist (note that it can be dangerous to run Terminal commands unless you really know what you’re doing—if you’re not an expert, you should always consult one first):
sudo rm -rf ~/.calisto ~/Library/VideoFrameworks /Library/.cachedir
Where Can I Learn More?
 We’ll talk about OSX/Calisto on this week’s episode of the Intego Mac Podcast. Subscribe now to make sure you don’t miss an episode!
We’ll talk about OSX/Calisto on this week’s episode of the Intego Mac Podcast. Subscribe now to make sure you don’t miss an episode!
If you’d like additional technical details about OSX/Calisto, you can read the write-ups by Mikhail Kuzin and Sergey Zelensky and Thomas Reed.
