OceanLotus OS X Malware Disguises Itself as Adobe Flash Update
Posted on
by
Graham Cluley

Intego VirusBarrier users are protected against the OS X version of OceanLotus, a sophisticated Trojan horse that has been used to spy against businesses and government agencies.
In May last year, Chinese security firm Qihoo360 published a technical paper examining a malware campaign that was said to be targeting critical areas of Chinese infrastructure — including government offices, research institutes, maritime agencies, construction and shipping enterprises.
Sadly, Qihoo360’s paper is in Chinese (a language I don’t read!) and Google’s online translation is not perfect, but it is clear that the security firm had also seen a version of OceanLotus made specifically for the OS X platform.
A recent report by AlienVault has brought this OS X version of OceanLotus back into the spotlight.
 There’s nothing particularly novel about the social engineering that OceanLotus uses to dupe users into infection, posing as an update to Adobe Flash.
There’s nothing particularly novel about the social engineering that OceanLotus uses to dupe users into infection, posing as an update to Adobe Flash.
But then, an attack’s social engineering doesn’t need to be sophisticated if it is effective. Malicious hackers know that their targets are used to being prompted to install updates to widely-used applications — such as Adobe Flash — and many will not be surprised to see a pop-up appear on their screen and will click to run code without thinking carefully about the potential dangers.
And, you may be asking, how did the criminals get the fake version of Flash to users in the first place in order to hit them with the OceanLotus malware? It appears that OceanLotus has been spread via two different methods.
Firstly, the malware was distributed via watering hole attacks. This is where a particular legitimate website is compromised by online criminals, who inject malicious code into its pages. Innocent visitors to the poisoned webpages have their computers infected via a drive-by download attack, or are socially engineered into installing software that then compromises their systems.
Examples of possible watering hole sites include websites that might cover news about a particular topic, or forums that deal with a particular industry. Online criminals target particular sites, knowing that their targets are likely to regularly visit it. Examples would include the OSX/Tibet malware that was distributed in the form of a poisoned Java applet on compromised websites, or OSX/Pintsized that successfully infected computer systems at Facebook, Twitter, Apple, and Microsoft, amongst others.
The other way that OceanLotus has been distributed is through spear-phishing attacks, where emails carrying malicious attachments or links are targeted at workers at specific organisations with the intention of tricking them into infection.
Files used by the malware include:
- FlashUpdate.app/Contents/MacOS/EmptyApplication
- FlashUpdate.app/Contents/Resources/en.lproj/.DS_Stores
- FlashUpdate.app/Contents/Resources/en.lproj/.en_icon
The malware’s loader is encoded and it decodes itself to be able to decode other files, which are used to deploy the threat locally. This makes analysis (and the creation of protection routines) harder. When the Trojan is installed, a persistent daemon runs and performs several tasks from a command & control (C&C) server. During Intego’s laboratory tests, the C&C servers appear to be currently offline.
In the below image you can see Intego NetBarrier alerting on an attempt by the malware to receive commands from the command & control servers, in order to download additional payload code. If you see such a message you should obviously block the connection.
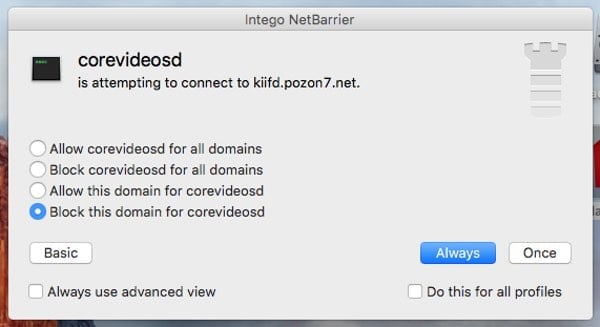
Intego VirusBarrier with up-to-date virus definitions will detect and eradicate the OSX/OceanLotus malware.
Users are reminded that the only safe place to download security updates for Adobe Flash is directly from the Adobe website itself.