New Version of Imuler Trojan Horse Masquerades as Image Files
Posted on
by
Peter James
Intego has discovered a new version of the Imuler Trojan horse, which the company first discovered in September, 2011. At the time, the sample discovered masqueraded as a PDF file containing Chinese text. This was not found in the wild, and the risk was considered to be low.
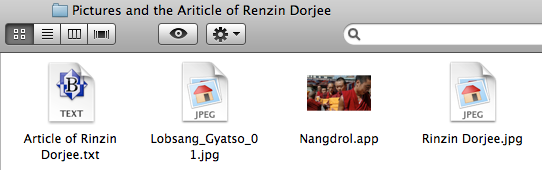
The latest version, Imuler.C, has been found to be disguised as image files. Intego found two samples of this malware on the VirusTotal website, a site used by security companies to share malware samples. Two samples were found, both in zip archives: “Pictures and the Ariticle of Renzin Dorjee.zip” and “FHM Feb Cover Girl Irina Shayk H-Res Pics.zip.” In both cases, an application was included among the various files, with an icon making it look like an image:

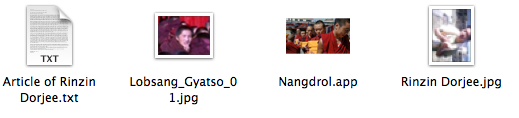
This technique is not new, and takes advantage of a default setting in the Mac OS X Finder, whereby file extensions are not displayed. Users double-clicking on the application launch the malware, which quickly deletes itself, replacing the original application with a real JPEG image corresponding to the one that was an application, and displays this image in the user’s default image viewer. There is no visible trace of the application after this point.
The malware installs a backdoor at /tmp/.mdworker, along with other files in this directory. A process called .mdworker then launches; the mdworker process (not the absence of the . before the name) is a processed used by Spotlight to index files.
A launchagent file is also installed at ~/library/LaunchAgents/checkvir.plist, along with an executable in the same folder, ensuring that the malware launches when the user logs into his or her Mac, or starts it up. After a restart, the .mdworker process is deleted, and the checkvir executable launches.
This malware searches for user data, and attempts to upload it to a server. It also takes screenshots and sends them to the server. It creates a unique identifier for the specific Mac to be able to link the Mac and the data it collects. We have seen that this malware is active, as it connects to a remote server and downloads new executables.
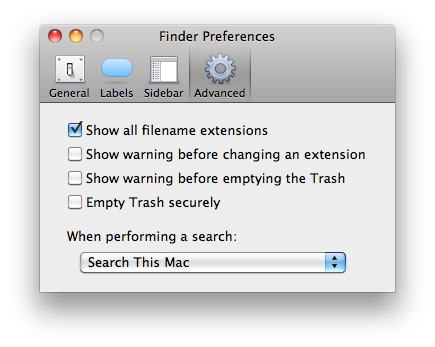
For now, Intego has not found this malware in the wild, and considers the risk to be low for now. However, we recommend that Mac users display file extensions in the Finder’s Advanced preferences:
Intego VirusBarrier X6 with malware definitions dated March 15, 2012, or later protect against the Imuler.C malware.