New Variant of Flashback Trojan Horse Gets Sneakier
Posted on
by
Peter James
We’ve seen several variants of the Flashback Trojan horse, since Intego first discovered this malware on September 26. The latest version, Flashback.D, has gotten a bit sneakier.
First, it checks to see if the user is running Mac OS X in VMware Fusion. If so, it does not execute. It does this because many malware researchers test malware in virtual machines, rather than infect full installations, as it is easier to delete them and start over with clean copies. This means that security researchers analyzing and looking for this malware need to be running regular Macs.
Next, the installer for the malware downloads the payload when running the postinstall script.
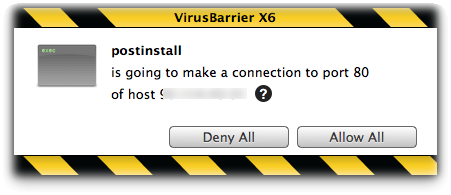
Finally, it no longer installs the easy-to-spot ~/Library/Preferences/Preferences.dylib. Instead, it installs the backdoor inside Safari, and does so in two ways. It adds information to Safari’s info.plist file, with the location of the backdoor, and it adds the actual backdoor module at /Applications/Safari.app/Contents/Resources/UnHackMeBuild.
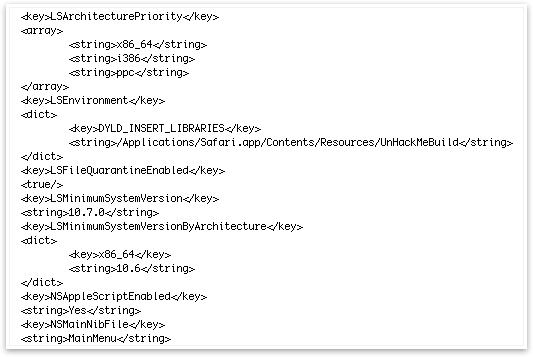
Even if a user removes the above file (UnHackMeBuild), they need to edit Safari’s info.plist file; if not, Safari will look for the backdoor on launch, and, if it is not found, Safari will quit.
These changes show that the malware authors are sophisticated, and that they’re altering their code to ensure that the malware is not detected. Naturally, Intego’s security researchers have spotted all these changes, and Intego VirusBarrier X6 continues to protect users from the Flashback Trojan horse.