New Imuler Variant Found–Steer Clear of “Your Dirty Pics”
Posted on
by
Lysa Myers
Update – September 23, 2012
This Trojan is being targeted at Tibetan activists. It has been reported as being received in a threatening email with the following text:
Subject:
“F*** you [recipient name]! I got your dirty naked photos.”
Body:
“F*** you A******! You are a stupid jerk! I got your dirty naked photos.
You’d better take care of yourself and get out of my way.
Understand??
F*** off!!!!!!!!!!!”
____
Intego has discovered a new version of the Imuler Trojan horse, which was first discovered in September 2011. Right now the risk is considered to be low – a sample of this malware was found on the VirusTotal website in a ZIP archive named “your dirty pics.zip.” Inside the ZIP file is an application with an icon making it look like an image. If the file is run, it installs a backdoor without the need for an admin password.
Below is a screenshot of the contents of the ZIP, which were housed in a file called “Your Dirt” (we took the liberty of covering the naughty bits):
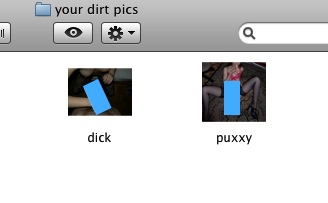
The malware quickly deletes itself, replacing the original application with a real JPEG image corresponding to the one that was an application. The image is then displayed in the user’s default image viewer. There is no visible trace of the application after this point, but it does remain active as a backdoor on the system.
The Trojan creates the following malicious files on an affected system:
- /tmp/.mdworker
- /tmp/updtdata
- /tmp/launch-IORF98
- ~/Library/LaunchAgents/ScheduledSync.plist
- ~/Library/LaunchAgents/ScheduledSync
Once active, the Imuler calls home to www.ouchmen.com to await further instructions. The Trojan survives reboot until the malicious files are removed.
The Imuler Trojan has two main methods of stealing information:
- It searches the system for user data
- It can also take screenshots.
Both are uploaded to the controller’s server. It creates a unique identifier for the specific Mac to be able to link the Mac and the data it collects. The backdoor also allows new files to be downloaded onto an affected system. That functionality is active at the time of writing.
Scaring or tantalizing users into viewing illicit pictures has always been a popular social-engineering tactic; many people cannot see past the possibility of viewing someone’s private pictures, and in cases like this they’ll pay the price. One of the oldest pieces of malware protection advice is not to view files that you were not expecting, and it still holds true in this instance. Whether it appears to come from your most trustworthy friend or a total stranger, if someone’s unexpectedly sending you dirty pictures, you should probably go ahead and delete it. Afterwards, ask that friend if they meant to send dirty pics. If the photos are something you really, urgently need to see (you naughty minx you), your friend can probably re-send them.
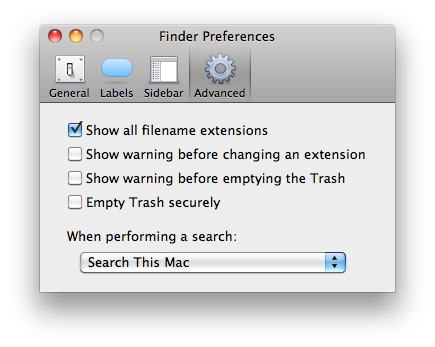
You can gain a small measure of additional protection against attacks like this if you configure Finder to show all file-extensions.
Intego VirusBarrier users with up-to-date virus definitions are protected from this threat, which is detected as Trojan:OSX/Imuler.D.