New Flashback Variant Takes Advantage of Unpatched Java Vulnerability
Posted on
by
Peter James
A new variant of the Flashback malware, Flashback, has been found in the wild. This variant uses a Java vulnerability, as a previous variant did. This variant takes advantage of two Java vulnerabilities, on of which has not yet been patched by Apple in the version of Java that they supply.
Intego has had samples of this variant of the Flashback malware since March 23, and have been finding new samples and variants of this malware almost daily since then. Intego has a number of samples, and other security companies have reported about samples that they have, which are not all the same as the ones Intego has. Our latest variant is Flashback.R.
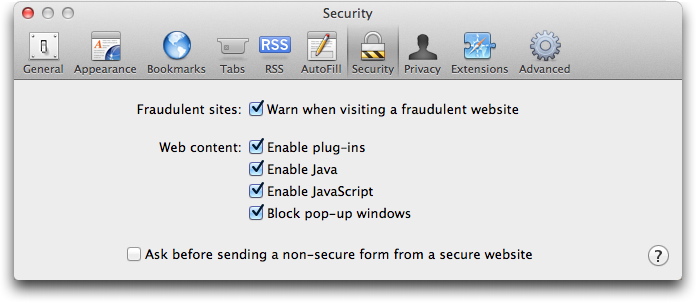
In any case, the safest thing that users can do is turn off Java in their web browser. If you use Safari, choose Safari > Preferences, then click on Security. Uncheck Enable Java, to ensure that no Java applet can run. For other browsers, check in their security preferences as well.
It’s worth noting that given the reactivity of the creators of this malware, it can be risky to follow instructions presented on some websites about removing it. As the most recent versions of the Flashback malware use random four-character names for files they place in the /tmp folder, you cannot know, simply by looking at these file names, if a file is valid or if it is malware. Deleting files manually, because you think they are malicious, may lead to system problems or instability.
Intego VirusBarrier X6 protects against this variant of Flashback, with malware definitions dated March 23, 2012 or later.