New Flashback Trojan Horse Variant Uses Novel Delivery Method to Infect Macs
Posted on
by
Peter James
Intego first discovered the Flashback Trojan horse in September 2011, and since then has seen a number of variants of this malware. A variant discovered in October 2011 notably damaged some system files.
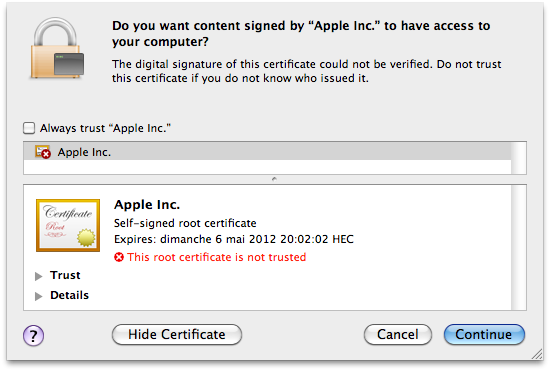
In the past few months, Intego has found new variants of the Flashback Trojan horse every few days, but the company’s latest discovery is a bit surprising. The people behind the Flashback Trojan horse have begun using a novel delivery method to infect Macs. Taking advantage of two Java vulnerabilities, this latest variant is able to install itself on a Mac with much more limited user intervention. There is no more installer, no request for a password. The malware first tries to install itself using one of two Java vulnerabilities. If this is successful, users will be infected with no intervention. If these vulnerabilities are not available – if the Macs have Java up to date – then it attempts a third method of installation, trying to fool users through a social engineering trick. The applet displays a a self-signed certificate, claiming to be issued by Apple. Most users won’t understand what this means, and click on Continue to allow the installation to continue.
Found in the wild, this new variant installs an executable file in the /tmp directory, applies executable permissions with the chmod command, then launches the executable with the nohup command. The Flashback backdoor is then active with no indication to users that anything untoward has happened.
A few points need to be made regarding Java and Mac OS X. Since Mac OS X 10.7 Lion, Java is no longer included with the operating system. However, the first time a user attempts to launch a Java applet, they see a dialog asking if they want to download Java. While most users may not use any Java applets, it is fairly common for online meeting and collaboration services to use Java, as it is cross-platform. Because of this, many Mac users may not realize that they have Java installed, as they may not remember having downloaded it when presented with such a request.
Also, the current version of Java for Mac OS X has patched the vulnerabilities that are being exploited. However, many Mac users who haven’t applied all the necessary security updates are at risk of having this malware installed with no intervention on their part.
Intego’s VirusBarrier X6 detects all current Flashback Trojan horse variants, so this new delivery method changes nothing for those users who are protected by VirusBarrier X6; the attempt to install this malware will be blocked, and users will be alerted.