Month in Review: Apple Security in July 2017
Posted on
by
Joshua Long

July 2017 was another gripping month for Apple security, with new Mac malware surfacing yet again, and Black Hat and DEF CON presentations relevant to the security of Apple devices. Read on for more details.
New Mac Malware: “FruitFly” Spy Trojan Returns
Patrick Wardle spoke at the Black Hat USA and DEF CON security conferences last week about a variant of the “FruitFly” malware (also called, ClientCapture and Quimitchin).
Wardle noted that Apple had not yet updated its XProtect or Malware Removal Tool signatures to detect the newer FruitFly variant.
By registering command and control (C&C) domains previously used by the malware, Wardle was able to receive communication from infected machines and analyze the malware’s traffic.
You can read our write-up about OSX/FruitFly.B in New FruitFly Malware Variant Dragged from the Shadows. For further reading, see Wardle’s slide deck from his talks.
New Mac Malware: OSX/Leverage Resurfaces as OSX/FlashyComposer
Backdoor malware from 2013 (originally known as OSX/Leverage.A) has resurfaced in the form of a fake Flash Player update (dubbed OSX/FlashyComposer.A).
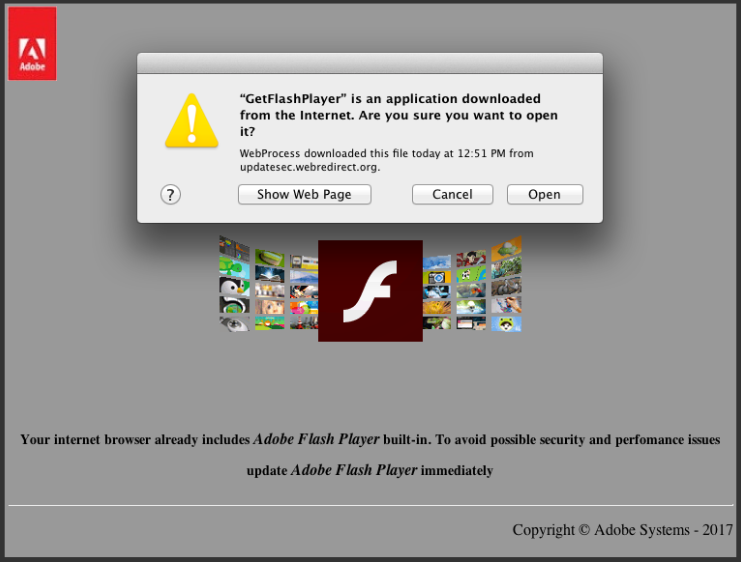
The malicious code attempts to download and install a fake Flash update. Image credit: Volexity.
Although Apple has updated its XProtect bad-download blocker, XProtect won’t clean up an existing infection. Make sure you’re running antivirus software on your Mac such as Intego VirusBarrier to more proactively prevent and defend against new malware and new variants of existing malware.
For more details, see Apple Updates XProtect to Block New Leverage Malware Variant.
Apple Security Updates; Broadpwn Mitigated

On July 19, Apple released security updates for its operating systems, including macOS 10.12.6 and iOS 10.3.3, along with several other apps.
The most notable fix — available for macOS Sierra, iOS, watchOS, and tvOS, as well as a special Wi-Fi Update for Boot Camp — resolves a memory corruption issue that could allow a nearby attacker to exploit a flaw in Broadcom wireless hardware to execute arbitrary code on the wireless chip.
That vulnerability, known as Broadpwn, was demonstrated last week by Nitay Artenstein at the Black Hat conference. Artenstein gives a very detailed technical overview of Broadpwn here on his company’s blog.
Notably, some vulnerabilities including Broadpwn were mitigated for macOS Sierra, but not for El Capitan or Yosemite, even though the older versions of macOS would presumably be affected as well. Intego recommends that users keep their Macs upgraded to the latest version of macOS to get the greatest benefit from Apple’s latest security features and patches.

Some macOS vulnerabilities are only patched for the most recent version of macOS, in this case Sierra.
Several other vulnerabilities, mostly related to the WebKit page-rendering engine, were fixed as well. Safari was updated for macOS Sierra, El Capitan, and Yosemite, and Apple’s Windows apps (iTunes and iCloud for Windows) also received updates.
For more details on Apple’s recent security updates, see Apple Releases macOS Sierra 10.12.6 and More with Security Fixes.
Other Apple Security News
July also brought some other interesting (although not necessarily Apple-related) security news:
- According to BleepingComputer, the DevilRobber malware (first discovered by Intego in 2011) made a comeback in June as the second most detected Mac malware by a rival anti-virus firm. Read more, here.
- Black Hat has posted briefings with descriptions of sessions and copies of the slideshow presentations from their USA 2017 event.
- DEF CON has highlights of their DC25 event.
- Wired also has coverage of its favorite hacks from both security conferences, including hacks involving guns, safe cracking, carwashes, and “evil bubbles.”
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Have something to say about this story? Share your comments below!