Month in review: Apple security in January 2018
Posted on
by
Joshua Long

Well, 2018 has sure started off with a bang! January brought to light major vulnerabilities affecting modern processor architectures, newly discovered Mac malware, and more. Read on for the details.
Meltdown and Spectre Vulnerabilities
 Months ago, multiple groups of researchers independently discovered serious vulnerabilities related to a feature of modern microprocessors known as speculative execution.
Months ago, multiple groups of researchers independently discovered serious vulnerabilities related to a feature of modern microprocessors known as speculative execution.
In early January, details about the two classes of vulnerabilities—namely, Meltdown and Spectre—were released to the public. Multiple hardware platforms were affected, including personal computers, mobile phones, and more.
Apple was among the companies that had received early notification about the vulnerabilities before they were publicly disclosed, so Meltdown mitigations were already present in December for macOS High Sierra 10.3.2, iOS 11.2, and tvOS 11.2 (Apple said that watchOS was unaffected).
In January, Apple also released Spectre-mitigating patches for Safari, as well as Meltdown mitigation for the two previous versions of macOS: Sierra and El Capitan.
For lots more details, be sure to listen to our podcast discussion and read our featured article on Meltdown and Spectre:
OSX/MaMi: First Mac Malware of 2018
 The first Mac malware discovered in 2018 was OSX/MaMi, DNS-hijacking malware found by a forum user on his coworker’s computer.
The first Mac malware discovered in 2018 was OSX/MaMi, DNS-hijacking malware found by a forum user on his coworker’s computer.
DNS is the technology that translates a domain (for example, apple.com) into the IP address of a server on the Internet. If malware forces a Mac to use rogue DNS servers, it’s possible for bad guys to monitor, intercept, redirect, or inject malicious code into your Internet traffic.
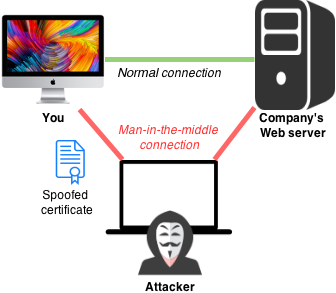
Diagram of a man-in-the-middle attack. Image: Nasanbuyn, Apple
OSX/MaMi also installs a root certificate authority, allowing man-in-the-middle interception of even TLS/SSL-encrypted communications, in particular HTTPS connections to Web sites that are normally considered secure.
Intego VirusBarrier detects this threat as OSX/MaMi.A.
For lots more details, including how to know whether your Mac is infected, be sure to check out our featured article on OSX/MaMi:
CrossRAT Malware Used for Global Cyber-Espionage
 Researchers from the Electronic Frontier Foundation and Lookout published a new report called “Dark Caracal: Cyber-espionage at a Global Scale,” with details about a “nation-state level advanced persistent threat (APT).”
Researchers from the Electronic Frontier Foundation and Lookout published a new report called “Dark Caracal: Cyber-espionage at a Global Scale,” with details about a “nation-state level advanced persistent threat (APT).”
The report includes information about a Java-based, cross-platform remote access Trojan (RAT) that’s capable of running on Macs and other platforms.
CrossRAT is capable of manipulating files, taking screenshots, and gaining persistence (enabling itself to run again automatically after a reboot). Intego VirusBarrier detects this threat as Java/LaunchAgent.
For additional details, including how to know whether your Mac is infected, be sure to check out our featured article about CrossRAT:
New CrossRAT Malware Used in Global Cyber-Espionage Campaign
Apple Security Updates
 Apple issued two batches of security updates in January. The first round was on January 8, which notably featured mitigations for the aforementioned Spectre vulnerabilities.
Apple issued two batches of security updates in January. The first round was on January 8, which notably featured mitigations for the aforementioned Spectre vulnerabilities.
The second round of updates came on January 23. Among other things, Apple mitigated the Meltdown vulnerability for macOS Sierra and El Capitan, as well a vulnerability that could allow a specially crafted link to crash an iOS device or a Mac (as discussed in the January 24 episode of the Intego Mac Podcast). Apple also released security updates for both iTunes and iCloud for Windows.
For more details on Apple’s January 23 updates, see our featured article:
Other Security News, in Brief
There were other notable goings-on in the security world in January. Some highlights:
- Five episodes of the Intego Mac Podcast were published in January. Be sure to subscribe to make sure you don’t miss any future episodes! This month’s topics included:
- In the United States, tax season began on January 30; U.S. citizens should file their tax returns as soon as practical to help prevent scammers from fraudulently filing for you

- The U.S. Department of Justice indicted the alleged author of the Fruitfly Mac malware, reports ZDNet; the alleged hacker is 28 years old but was 14 at the time Fruitfly was originally developed
 Western Digital My Cloud drives have a built-in backdoor (with a hard-coded password) that hasn’t been patched for more than six months, and the discoverer has released the full details to the public, reports Tech Spot
Western Digital My Cloud drives have a built-in backdoor (with a hard-coded password) that hasn’t been patched for more than six months, and the discoverer has released the full details to the public, reports Tech Spot Strangers can spy on your Tinder swipes, reports Wired
Strangers can spy on your Tinder swipes, reports Wired- Personal information of half of Norway’s population may have been breached due to an intrusion at a healthcare provider, reports Infosecurity Magazine
 Personal information of 240,000 U.S. Department of Homeland Security employees has been breached, reports The Register
Personal information of 240,000 U.S. Department of Homeland Security employees has been breached, reports The Register- Malware was found at dozens of gas stations in Russia; reportedly the malware skimmed money whenever customers used their credit cards at the infected pumps

Also, check out our article featuring the top Apple security stories of 2017—there’s a good chance you’ve missed or forgotten about something!
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
Also, each week we discuss Mac and iOS security news and other topics of interest on the Intego Mac Podcast. You’ll want to subscribe in iTunes/Podcasts to make sure you don’t miss any shows! Show notes are available at podcast.intego.com.
Last but not least, be sure to subscribe to the Intego YouTube channel to get monthly updates in video form, and click on YouTube’s bell icon (?) so you’ll get notified when each new episode is available.
“Evil mommy”/MaMi image credit: Max Pixel. Fruit fly photo: Arian Suresh.