Microsoft Tackles Critical Flaws in Office for Mac Updates
Posted on
by
Derek Erwin
Microsoft has issued Office 2016 version 15.17.0 updates to patch security vulnerabilities in its latest software, as well as Office 2011 14.6.0 to patch the earlier suite. Microsoft tackled “critical” vulnerabilities in the company’s flagship application software that can allow remote code execution.
Multiple remote code execution vulnerabilities exist in now outdated versions of Microsoft Office for Mac when the Office software fails to properly handle objects in memory. The most critical vulnerability, identified as CVE-2016-001, is present in all versions of Office from 2007 to 2016, for both Mac and Windows, according to Wolfgang Kandek writing for Qualys blog.
According to Microsoft’s security bulletin (MS16-004), the Office for Mac software affected includes: Microsoft Excel for Mac 2011, PowerPoint for Mac 2011, Word for Mac 2011, Excel 2016 for Mac, PowerPoint 2016 for Mac, and Word 2016 for Mac.
The vulnerabilities patched in these updates are described as follows:
- CVE-2016-0010 : Microsoft Office 2007 SP3, Office 2010 SP2, Office 2013 SP1, Office 2013 RT SP1, Office 2016, Excel for Mac 2011, PowerPoint for Mac 2011, Word for Mac 2011, Excel 2016 for Mac, PowerPoint 2016 for Mac, Word 2016 for Mac, and Word Viewer allow remote attackers to execute arbitrary code via a crafted Office document, aka “Microsoft Office Memory Corruption Vulnerability.”
- CVE-2016-0035 : Microsoft Excel 2007 SP3, Excel 2010 SP2, Excel 2013 SP1, Excel 2013 RT SP1, Excel 2016, Excel for Mac 2011, Excel 2016 for Mac, Office Compatibility Pack SP3, and Excel Viewer allow remote attackers to execute arbitrary code via a crafted Office document, aka “Microsoft Office Memory Corruption Vulnerability.”
The Microsoft security team further detailed the vulnerability attack scenarios, saying:
An attacker who successfully exploited these vulnerabilities could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
To exploit the vulnerabilities, a user must open a specially crafted file with an affected version of Microsoft Office software. In an email attack scenario an attacker could exploit the vulnerabilities by sending the specially crafted file to the user and convincing the user to open the file. In a web-based attack scenario an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerabilities. An attacker would have no way to force users to visit the website. Instead, an attacker would have to convince users to click a link, typically by way of an enticement in an email or Instant Messenger message, and then convince them to open the specially crafted file.
Microsoft’s Office for Mac updates address these vulnerabilities by correcting how Office handles objects in memory.
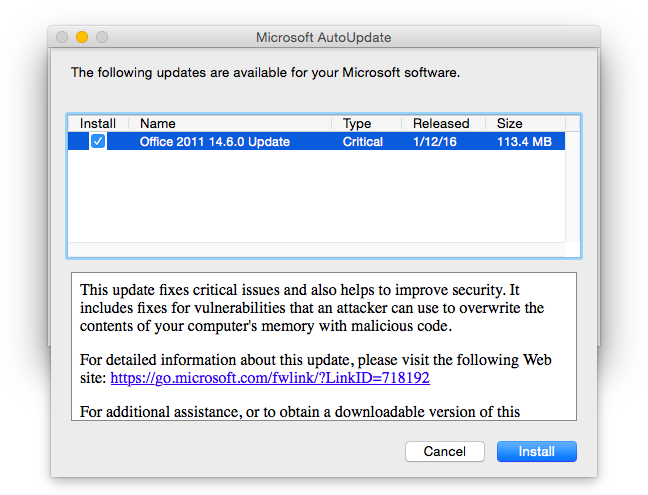
All Microsoft Office for Mac users should install these updates immediately. Mac users can update your software by using Microsoft’s AutoUpdate application, or by visiting the Microsoft Download Center:
Microsoft Office for Mac 2011 14.6.0 Update (113.4 MB)
Microsoft Office 2016 for Mac 15.17.0 Update (MS15-131)