Malware + Recommended + Security News
Mac Users Hit by Rare Ransomware Attack, Spread via Transmission BitTorrent App
Posted on
by
Graham Cluley

Mac owners who use the open source Transmission BitTorrent client are being warned that a version of the installer was distributed via the app’s official website, infected with a new family of ransomware.
It is believed that hackers managed to compromise the installer of Transmission version 2.90 on its download site on Friday, March 4, in order to spread ransomware that researchers at Palo Alto Research have dubbed “KeRanger.”
The outcome is that if you were unfortunate enough to install Transmission 2.90 onto your Mac, your computer may now be the digital equivalent of ticking time bomb. Because KeRanger waits three days before awaking, encrypting your documents and data files, contacting its command-and-control servers, and demanding a one bitcoin (approximately $400) ransom be paid for your data’s safe return.
According to the researchers, the KeRanger malware also attempts to encrypt Time Machine backup files, no doubt in an attempt to make it harder for victims to recover their precious data without paying the extortionists.
And don’t imagine that OS X’s built-in Gatekeeper protection would have saved you, as it appears that the poisoned KeRanger app was signed with a valid Mac app development certificate.
A message on the official Transmission website confirms the threat to users, and advises that they “immediately upgrade” to version 2.92:
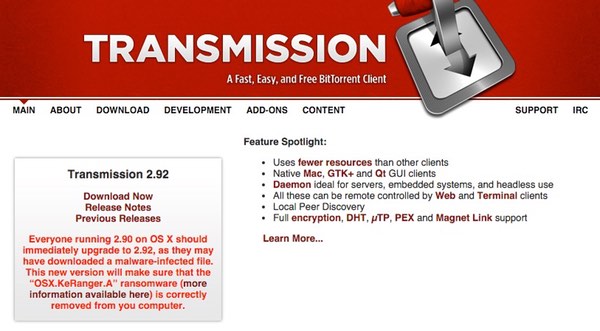
Everyone running 2.90 on OS X should immediately upgrade to 2.92, as they may have downloaded a malware-infected file. This new version will make sure that the “OSX.KeRanger.A” ransomware (more information available here) is correctly removed from you computer.
Palo Alto’s research team report that Apple has now revoked the digital certificates that the malware attack was abusing, and updated the rudimentary XProtect anti-virus protection built into the OS X operating system. Furthermore, the malicious downloads have now been removed from the Transmission website.
As MacRumors reports, the software is alerting users with a bright red warning when the app informs them that an update is available:
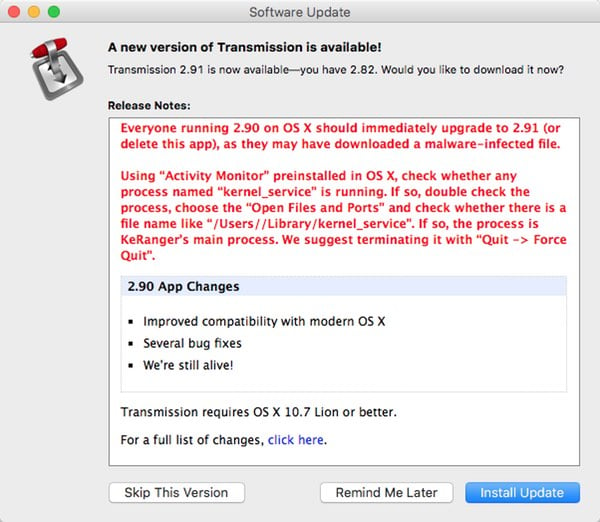
Everyone running 2.90 on OS X should immediately upgrade to 2.91 or delete their copy of 2.90, as they may have downloaded a malware-infected file. Using “Activity Monitor” preinstalled in OS X, check whether any process named “kernel_service” is running. If so, double check the process, choose the “Open Files and Ports” and check whether there is a file name like “/Users//Library/kernel_service”. If so, the process is KeRanger’s main process. We suggest terminating it with “Quit -> Force Quit
Apple has since revoked the abused certificate and updated XProtect anti-virus signature, and Transmission Project has removed the malicious installers from its website. Intego’s malware research team has also updated its VirusBarrier anti-virus definitions to detect the ransomware, identified as OSX/KeRanger.
Quite how the Transmission installer package managed to become infected is as yet a mystery. One natural theory is that the attackers may have been able to exploit a security vulnerability on the website to update the binary, having recompiled its open source code after incorporating the malware.
Reuters is reporting that this is the first time Mac users have been threatened by ransomware — which is a commonly encountered threat on Windows computers.
However, that’s not quite telling the whole story. Ransomware has admittedly rarely reared its ugly head on the OS X platform, but security researchers have been warning that there is no technical reason why extortionists might not target users of Apple’s operating system just as they have on Windows.
For instance, in 2014 researchers warned of Mac ransomware called “FileCoder,” which they described as “unfinished.” More recently, last November, researcher Rafael Salema Marques produced a functional proof of concept of ransomware that he called Mabouia.
And two months earlier OS X security researcher Pedro Vilaça published the code of his own Mac ransomware as a warning of what was possible.
Could this be the beginning of more ransomware attacks for Mac users? It would be a brave man who would bet against it.
The fact is that ransomware has proven to be a successful way to extort money out of Windows users, and there is little doubt that online criminals will not be tempted to switch the threat to Mac users too — especially as there continue to be many Mac users who have fooled themselves into believing that they do not need to take basic security precautions, such as running Mac anti-virus software.
It doesn’t matter if you are running Windows or OS X on your computer, the way to reduce the threat of ransomware blackmailing you for the safe return of your data is the same:
- Make regular backups of your important data, and keep them separate from your computer (to prevent the malware from trying to meddle with your backups too)
- Run up-to-date anti-virus software and keep your computer’s operating system and applications patched against the latest vulnerabilities.
- Always be suspicious of unsolicited links and attachments you are sent, and source your applications from reputable sources to reduce the chances that they have been tampered with.
Of course, the final piece of advice is to stay on your guard.
We know that criminals attempted to spread their OS X ransomware via a poisoned version of the Transmission app. What we don’t know is whether any other apps have been similarly meddled with, and it would be foolhardy to assume that whoever is behind this particular attack won’t try again, or won’t continue to develop their malware.
Sadly it seems clear that ransomware has well and truly arrived for OS X.
Editor’s Update, March 7: This post was originally published March 6, but we have updated it for clarity and conciseness.
How to tell if infected and remove the ransomware
Intego VirusBarrier with up-to-date malware definitions detects and eradicates the ransomware as OSX/KeRanger. Of course, you may also choose to manually remove KeRanger if your machine is infected.
To do so, check for this existing process within Activity Monitor: kernel_service. (The infected process kernel_service starts when the Transmission app v2.90 is opened.)
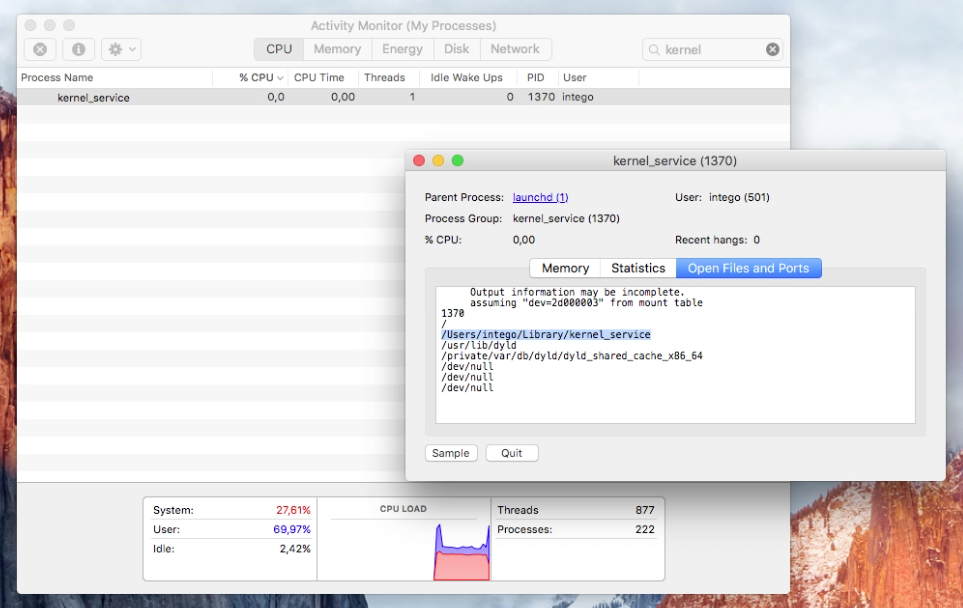
If this service is running, you must manually remove the ransomware as it will reload even if you force quit the service. If kerne_service is running, double-click it in order to see more information about the process, and then select the “Open Files and Ports” pane.
In Open Files and Ports, check for the file name:
/Users/<username>/Library/kernel_service.
If that file exists, then you have found OSX/KeRanger’s main process. Terminate the process using Quit > Force Quit.
Once you have force quit the process, use Spotlight to find out if any of the following files exist in the ~/Library directory:
- .kernel_pid
- .kernel_time
- .kernel_complete
- .kernel_service
If you see any of these files, delete them from your system.
We also recommend Mac users check for any infected Transmission apps. To do so, open Terminal and enter the following commands
ls /Applications/Transmission.app/Contents/Resources/General.rtf ls /Volumes/Transmission/Transmission.app/Contents/Resources/General.rtf
If the Terminal returns file permission details for one of these files, you should delete the application immediately.
Intego will continue to update this story as new information becomes available. Check back later for more details!