Mac malware masquerades as meeting apps: Realst Stealer is back!
Posted on
by
Joshua Long

The Mac malware family Realst Stealer is back in the news. Reports indicate that a recent malware campaign has been tricking victims into installing videoconferencing meeting software. But this software is actually a Trojan horse with password-stealing capabilities.
Let’s explore what we know about this active Mac malware campaign.
In this article:
- How is the malware currently spreading?
- What does the malware do?
- How can I keep my Mac safe from stealer malware?
- What can we glean from the malware distribution sites?
- Indicators of compromise (IOCs)
- Do security vendors detect this by any other names?
- How can I learn more?
How is the malware currently spreading?
In a recent campaign, threat actors have been targeting people looking for a job at a “Web3” company; i.e. working with technologies such as blockchains, NFTs, or cryptocurrencies similar to Bitcoin.
Victims may be invited to a call, and are given a link to a site that claims to offer meeting software for Mac or Windows. The site and software may go by any number of names; so far, they have reportedly included Meeten, Meetio, Meetone, Clusee, and Cuesee. As of when this article is being published, the Meetio[.]one and Meeten[.]org sites are currently online, and some browsers are not yet detecting these sites as malicious. A site delivering secondary payloads, deliverynetwork[.]observer, is still online as well.
It’s worth noting that the same fake meeting software could potentially be used in other scam campaigns as well. You may not work in Web3 technology, but a variation of the scam could be used against you regardless of your interests.
These Trojan horse applications are built using the Electron framework. Electron is a free, open-source software framework that makes it easy to build cross-platform apps—including malware.
What does the malware do?
The malware will attempt to steal sensitive data from the macOS Keychain (i.e. Passwords database), various Chromium-based browsers (namely Google Chrome, Microsoft Edge, Arc, Brave, Opera, Vivaldi, and the Vietnamese browser Cốc Cốc), the Telegram Messenger app, and popular cryptocurrency wallets.
Among the data stolen from browsers are cookies (which can often be reused on an attacker’s system to bypass passwords and two-factor authentication) and autofill data, potentially including usernames and passwords.
These Trojans may be variants of Realst Stealer. Realst came to light around mid-2023, when it was observed in sophisticated campaigns targeting gamers interested in NFT and Web3 video games. We also reported about Realst’s recruiting efforts shortly thereafter.
Mac stealer malware Realst disguises itself as video games, is macOS Sonoma-ready
How can I keep my Mac safe from stealer malware?
If you use Intego VirusBarrier, you’re already protected from this malware. Intego detects samples from this campaign as OSX/ChainBreaker.fs, OSX/Stealer.ext, Python/KeychainDump, and trojan/TR/PSW.Agent.lyel.
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s latest Mac operating system, macOS Sequoia.
One of VirusBarrier’s unique features is that it can scan for malicious files on an iPhone, iPad, or iPod touch in user-accessible areas of the device. Just attach your iOS or iPadOS device to your Mac via a USB cable and open VirusBarrier.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware, too.
What can we glean from the malware distribution sites?
As we saw with Realst’s elaborate video game Trojans last year, the distributors of these Trojan horses went to a lot of trouble to make these videoconferencing Trojans look legitimate. Each variant has had its own homepage, Telegram, Linktree, and X (aka Twitter) social network profiles.
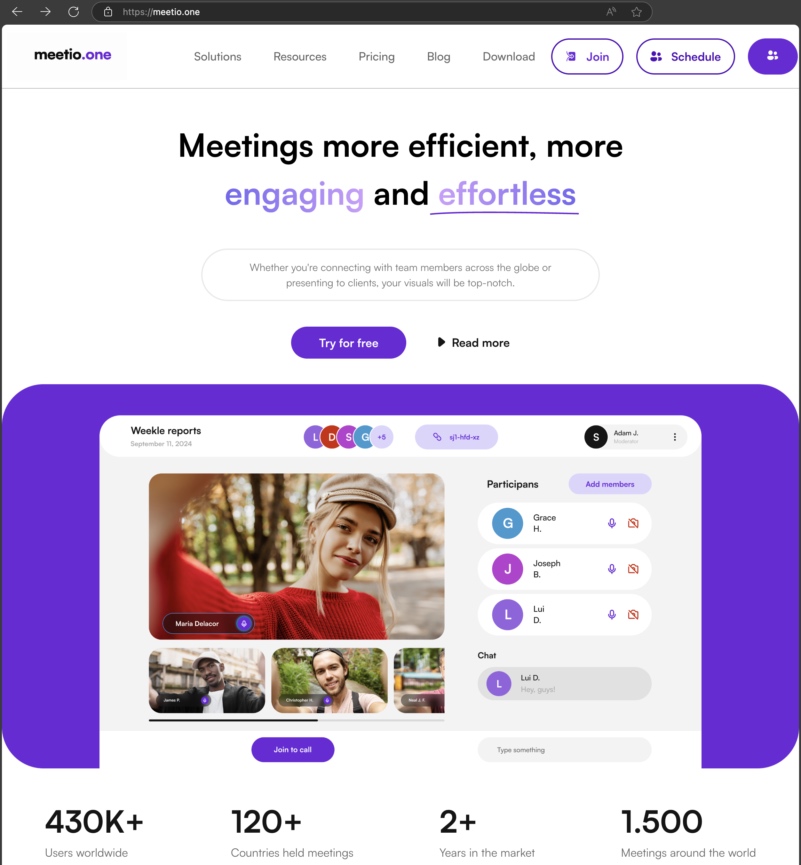
“Meetio” and “Meeten” sites are nearly identical. While they may look harmless, they have distributed Trojan malware.
The @MeetioHQ handle on X is still active as of the time of this publication. It has been a “verified” account with a blue-check badge since last month. “Meetio” currently has more than 8,500 followers—but only two are verified accounts; this suggests that most of the rest are likely bots.
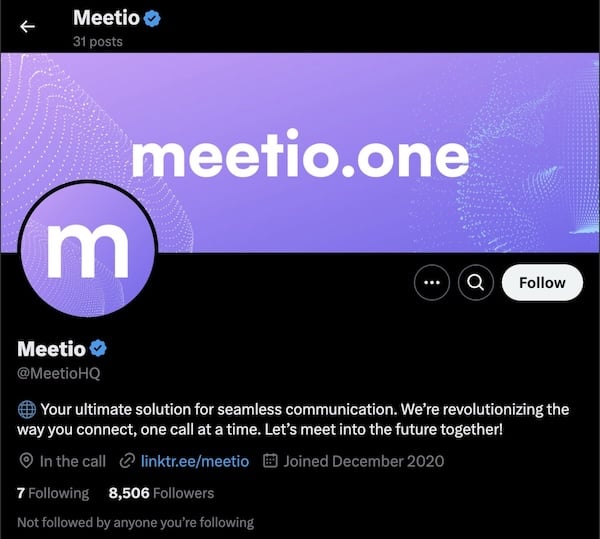
@MeetioHQ, a malware distributor with a “verified” X account
Interestingly, the account was created in December 2020, though “Meetio” posts only date back to November 20, 2024; this may indicate that a dormant account was reactivated by the malware distributors, or that a years-old account may have been hacked.
Indicators of compromise (IOCs)
Following are SHA-256 or MD5 hashes of malware samples from this campaign:
0f38a620cb3641ffb2d7472472d65700634199e54e451087c316aecba3613ae0* be012ac8a3f046e56e1c6a293ae567462c01216d024032c4225f656d8002691e b5c1260e6f4acc44470c3fb18c665832d15f478005eb291e2caeff94fc5b7d6f* 5e6cc2ed3876197561ba60a8d8aa7042d025e997cc1046ea351b5b2bc48f9dd7 693731b1ff6e49f698e0aee2a97ae5d7ddbbd104ddec86e0d27bbd0e52e4b0a3* 7c1f28ac0a115bfe6f272acb86e3c0f2c9aa5b52d2cfad087a1abcc0dd7ac771* 8d731b0bd8c0cda9f923ed0980ea76d57ba036c3a73acb9f4ac8ffe4e4734b83 98cb1ab05047e6ff2b614ce9f6f0cf6ece6592522c90898ce1f43d646e7edfea* aea0bfbba8dd4f3cb99b33792e044af653c2ea07af960f9587d389160497d647 f3381109a90f1c2be9e005dcf6d4095766123978d786a2531c5631df4b7d883e* 9b2d4837572fb53663fffece9415ec5a [unavailable on VirusTotal] *first reported by Intego
File names for the malicious payloads have included the following:
MeetioSetup.pkg* MeetenAppSetup.pkg* CluseeApp.pkg CallCSSetup.pkg Meeten.exe MeetenApp.exe MicrosoftRuntimeComponentsX64.exe UpdateMC.exe *first reported by Intego
This malware campaign leverages the following domains and IP addresses:
meetio[.]one meeten[.]us deliverynetwork[.]observer clusee[.]com meetone[.]gg 81.28.12[.]12* 139.162.179[.]170 172.104.133[.]212 199.247.4[.]86 *first reported by Intego
Network administrators can check logs to try to identify whether any computers may have attempted to contact the domains or IPs above in recent weeks, which could indicate a possible infection.
The malware campaign also currently uses the following social media accounts:
linktr[.]ee/meetio t[.]me/meetiohq x[.]com/MeetioHQ meetioapp.medium[.]com linktr[.]ee/meeten t[.]me/meetenhq
Do security vendors detect this by any other names?
Other antivirus vendors’ names for this malware may include variations similar to the following:
A Variant Of Win64/PSW.Agent.FC, Exe.trojan.stealer, Generic.MAC.Stealer.J.3BEE0F67 (B), Generic.MAC.Stealer.J.46AF4C95 (B), Generic.ml, HEUR:Trojan-PSW.OSX.HashBreaker.e, Infostealer.Win64.Agent.V73i, JS/TrojanDownloader.Agent.ABSC, MacOS:Stealer-AR [Trj], MacOS/ABPWS.ZWLX-9, MacOS/ABTrojan.ZWLX-, Mal/Generic-S, Malicious_Behavior.SB, Malware.OSX/GM.Stealer.XS, Malware.Win32.Antis, Malware.Win32.Gencirc.11cacd7d, Malware/Win.Generic.C5695177, Osx.Trojan-QQPass.QQRob.Dplw, Osx.Trojan-QQPass.QQRob.Edhl, Osx.Trojan-QQPass.QQRob.Rsmw, OSX.Trojan.Gen, OSX/Agent-BKOX, OSX/Agent.BX!tr.pws, OSX/GM.Stealer.XS, OSX/PWS-COF, Password-Stealer ( 005ad7011 ), PUP/Generic, RiskWare:Win/Stealerc.npb, Spyware.Stealer!8.3090 (CLOUD), Suspicious.low.ml.score, Tar.trojan.stealer, Ti!AEA0BFBBA8DD, TR/PSW.Agent.lyely, Trojan-PSW.Discord, Trojan-PSW.Win32.Stealerc.nfa, Trojan:MacOS/Multiverze, Trojan.Agent.Win64.63740, Trojan.Gen.MBT, Trojan.MAC.Agent.ZW, Trojan.MAC.Generic.118582, Trojan.OSX.Psw, Trojan.OSX.Stealer.i!c, Trojan.TR/PSW.Agent.lyely, Trojan.UKP.Stealer.i!c, Trojan.Win32.Stealer.12!c, Trojan[stealer]:MacOS/HashBreaker.C9OKG, Trojan[stealer]:MacOS/HashBreaker.e, Trojan[stealer]:MacOS/Multiverze.Gen, TrojanPSW:Win32/Stealerc.c44afb60, TrojanSpy/Stealer.na, W32.Malware.gen, W64/ABPWS.AKFA-6874, Win64:MalwareX-gen [Trj], Xar.trojan.stealer
How can I learn more?
This malware was first written about by Tara Gould; see Gould’s report for additional technical details.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()