Lookalike domains are spreading malware; here’s how to stay safe
Posted on
by
Joshua Long
A recent report from Ars Technica indicated that, "with help from Google [Ads]," scammers were able to impersonate the Brave browser’s homepage to distribute malware to unsuspecting victims.
Part of the attack was enabled by various peculiarities of Google Ads (namely, the ability to display one domain in an ad, but actually go to another domain when clicked) and Google Search (which places ads that look very similar to search results above the actual results). But another part of the attack has to do with a feature in some browsers related to Internationalized Domain Names (IDN), which use Punycode encoding. In this case, the attackers used "bravė" in their lookalike domain instead of "brave"—which may be difficult to distinguish, in some cases. This type of attack is known as an IDN homograph attack.
What are Punycode and IDNs?
Domain names (for example, intego.com) can only contain standard English alphabet letters, numbers, and hyphens. But what if you want a domain to represent a language that uses characters not contained in the English alphabet? You may want a domain containing a character with a diacritical mark such as the ñ from Spanish, the ç from French, or the ü from German, or you may want a domain with Japanese, Chinese, or other characters. Punycode is a way of encoding such characters within the ASCII character set permitted for domain names, and an Internationalized Domain Name (IDN) contains Punycode strings prepended by the four characters "xn--".
If you don’t read or visit sites in multiple languages, you may want to ensure that your browser doesn’t hide the "real" domain name behind Punycode, to avoid potentially getting scammed by lookalike domains.
How does my favorite browser handle Punycode IDNs?
I tested a number of popular (and some less well-known) macOS browsers, downloaded from their English-language homepages and installed in an US English configuration of macOS. (I specify English, because it’s possible that some browsers may have different defaults if downloaded in other languages or if installed while macOS has a different default language.) Based on my testing, the following browsers displayed the "xn--" ("real") domain names, rather than domains with lookalike characters:
- Safari 14 on macOS 11
- Google Chrome version 92
- Microsoft Edge version 92
- Brave version 92
- Opera version 78
- Vivaldi version 4.1
- Waterfox Classic 56.5
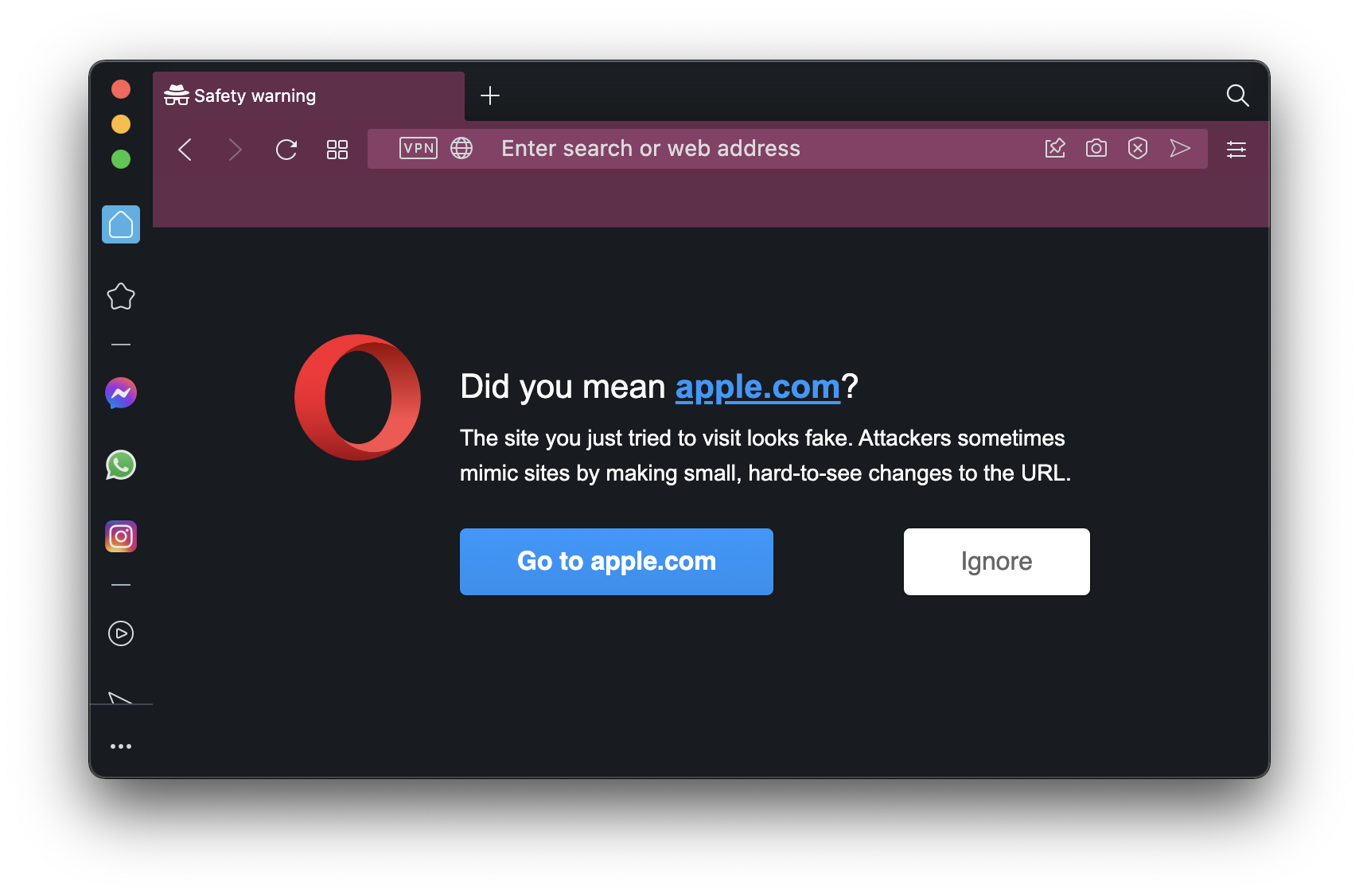
Two of those browsers get bonus points for going above and beyond just displaying the actual domain names. Opera displays a full-page warning message before loading the page:
"Did you mean [the English-alphabet variation of the domain]? The site you just tried to visit looks fake. Attackers sometimes mimic sites by making small, hard-to-see changes to the URL."
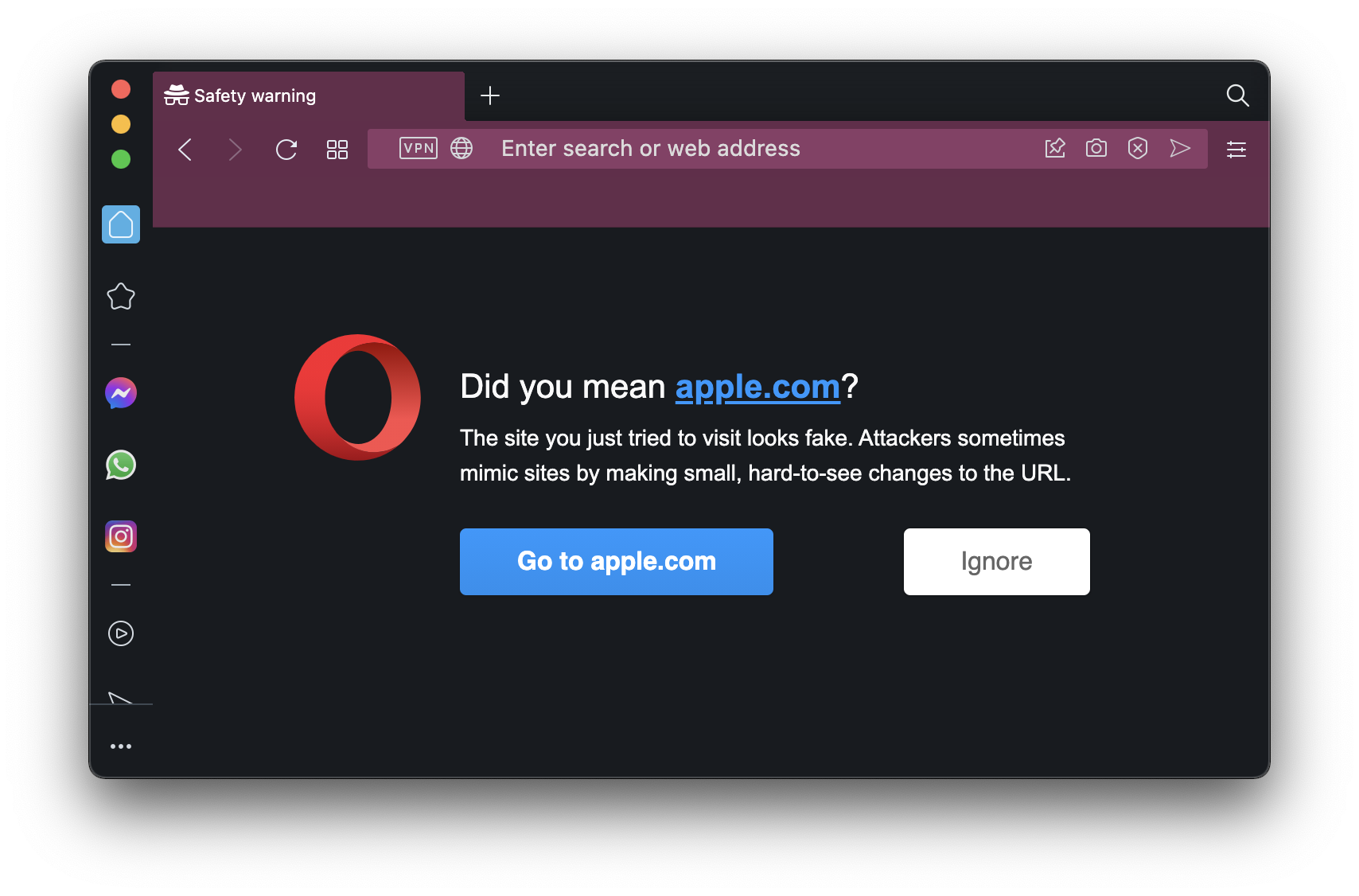
Opera’s warning message has two buttons: "Go to [the English-alphabet variation of the domain]" or "Ignore"—the latter loads the "xn--" domain and displays it as such.
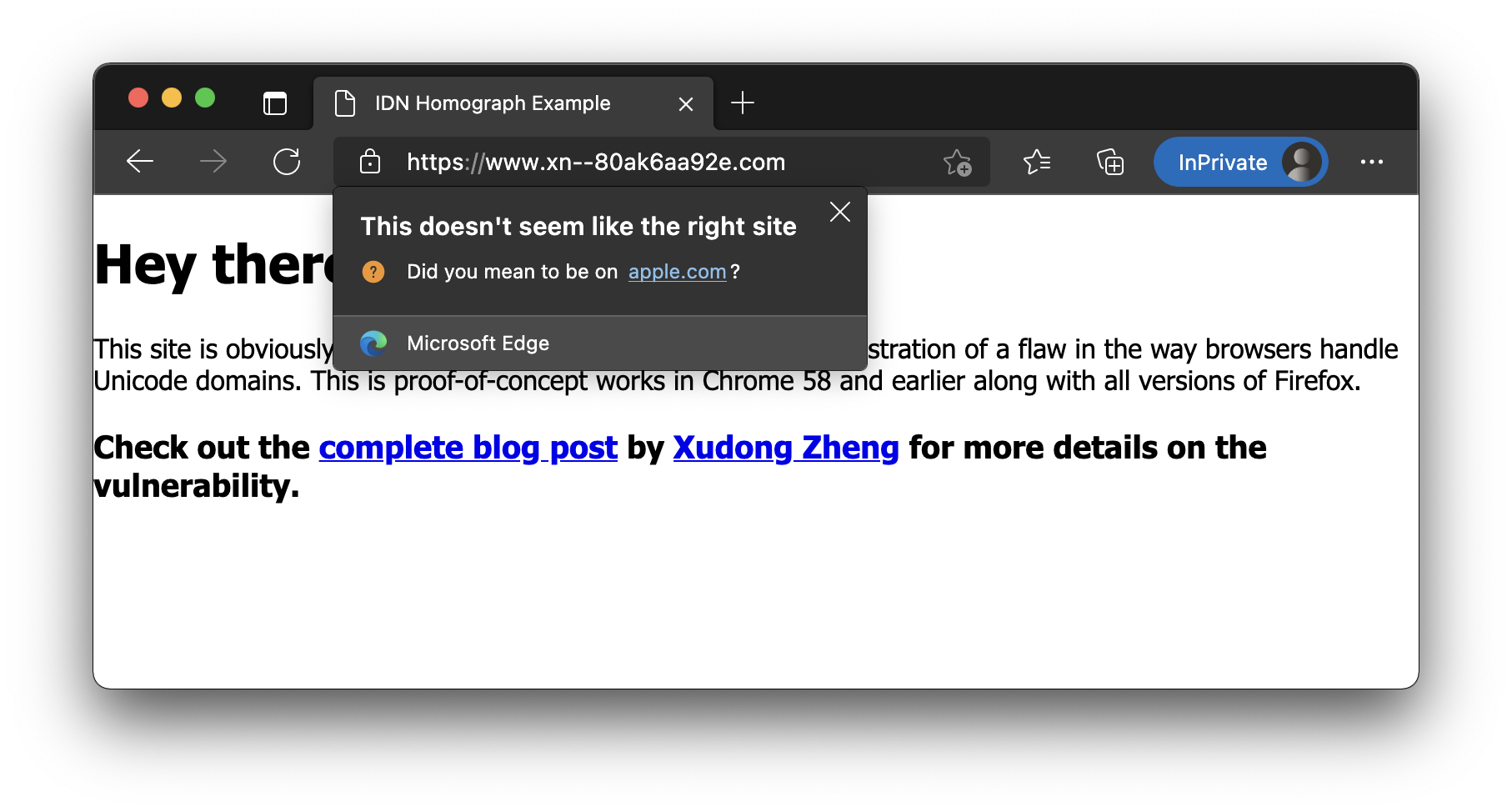
Microsoft Edge is a little less protective than Opera, but behaves better than the other browsers listed above. Edge dutifully loads the "xn--" site and displays the domain as such, but it pops up a little warning stating, "This doesn’t seem like the right site," and it asks, "Did you mean to be on [the English-alphabet variation of the domain]?"
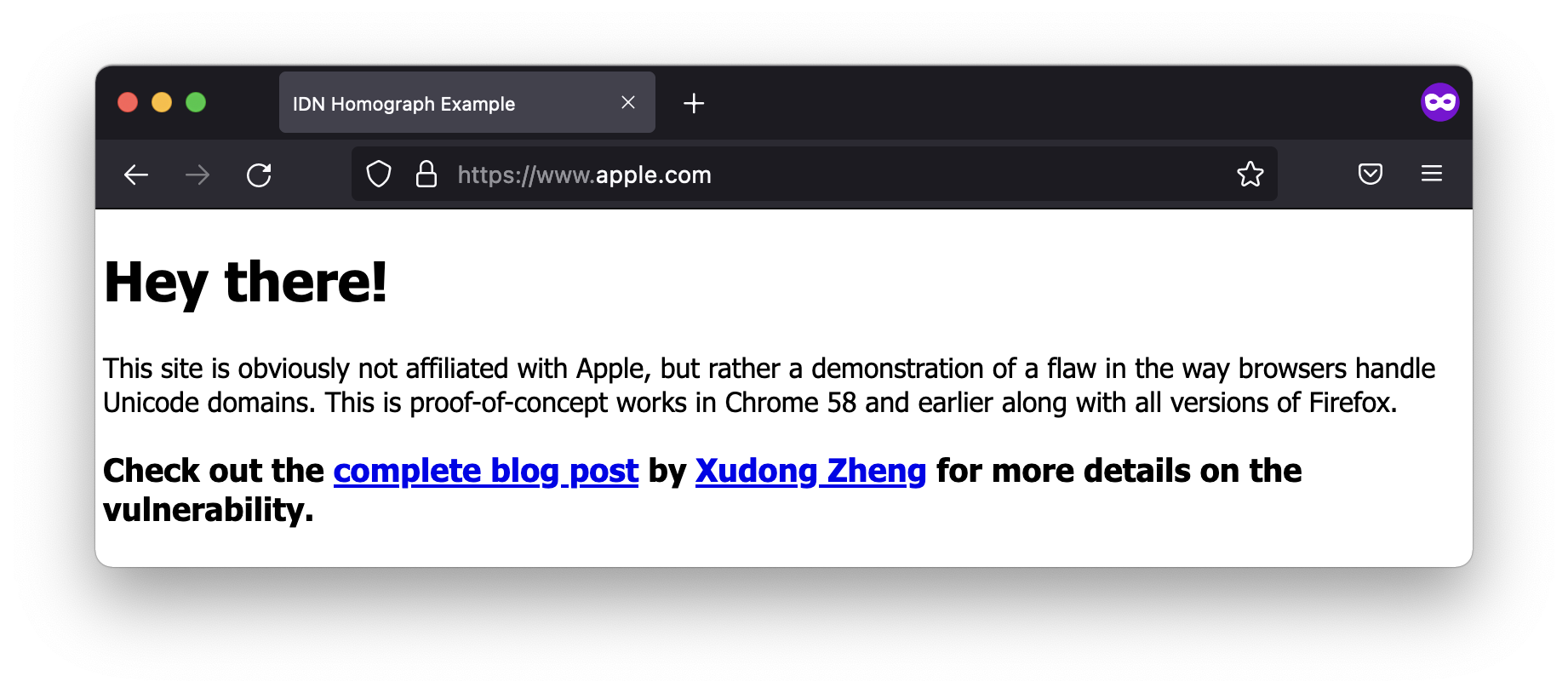
While those browsers are safer from IDN homograph attacks, the following browsers default to showing potentially deceptive domain names by default:
- Firefox version 90
- Tor Browser version 10.5
How can I configure Firefox or Tor Browser to not display IDNs?
If you’re concerned that the default setting might lead you to get phished or hit with malware, you can reconfigure both Firefox and Tor Browser to display the actual domain (starting with "xn--") instead of the interpreted domain in the address bar. To do so, follow these steps:
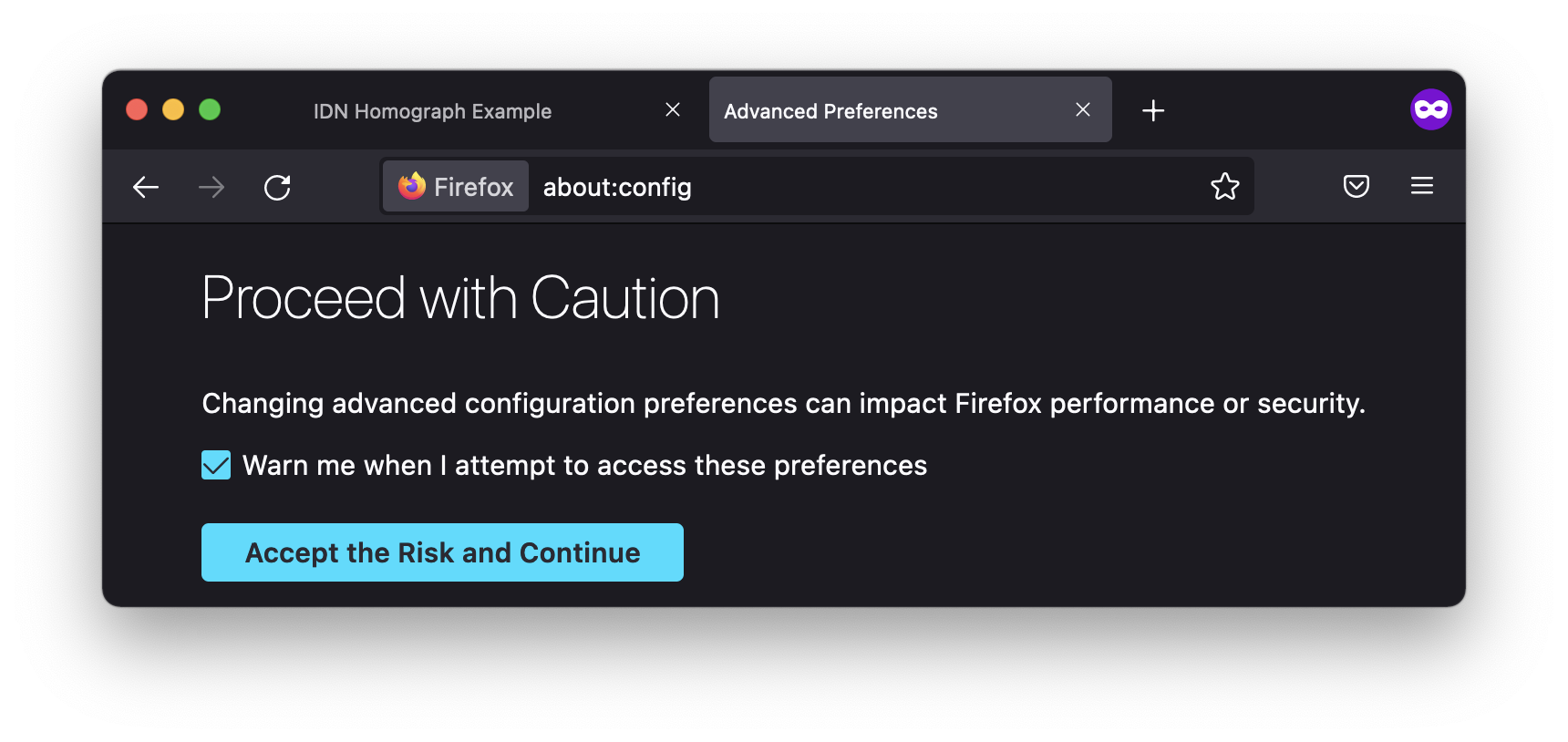
- Type about:config into the address bar and press Return or Enter on the keyboard.
- Clcik on the "Accept the Risk and Continue" button.
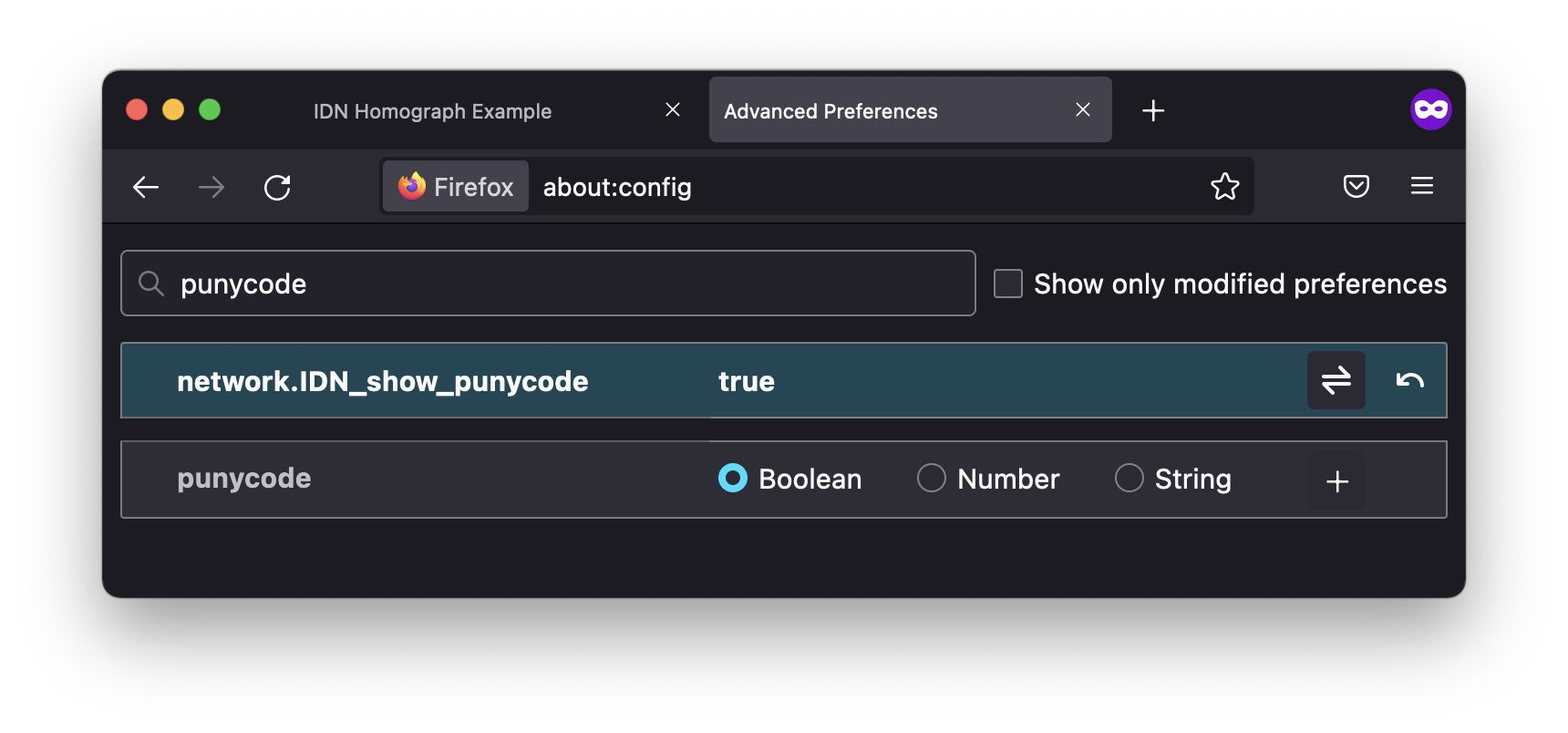
- Search for network.IDN_show_punycode (it’s easiest to just start typing "puny").
- Double-click on that entry (or click on the Toggle button on the same line) to change from the default “false” setting to “true”.
After making this change, Firefox or Tor Browser will retain this setting even after you quit the browser. Note that if you have multiple user accounts on your Mac, you’ll need to configure this setting for each user.
Are older browsers subject to IDN homograph attacks, too?
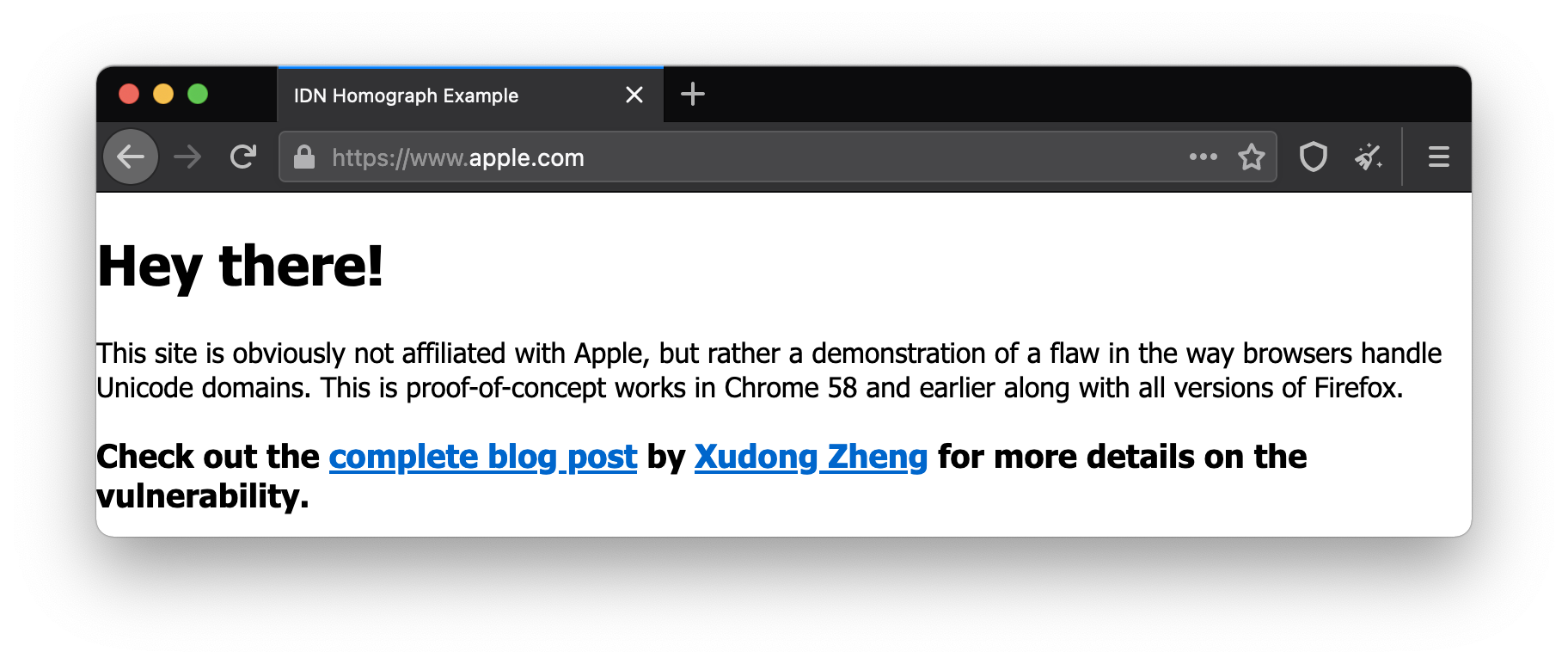
We originally reported on Punycode domain attacks in April 2017, when researchers warned that healthcare sites and even apple.com could be spoofed in many popular browsers.
If you happen to still use a very old and outdated browser, particularly one that was last updated before 2017 (such as Chrome 57 and earlier, and Opera 44 and earlier) may also be subject to IDN homograph attacks. If your browser is very old, update to a newer browser to ensure that you’re protected from recently patched vulnerabilities.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: Facebook, Instagram, Twitter, and YouTube.