Malware + Recommended + Security News
Komplex Malware: The Return of Sofacy’s XAgent
Posted on
by
Jay Vrijenhoek
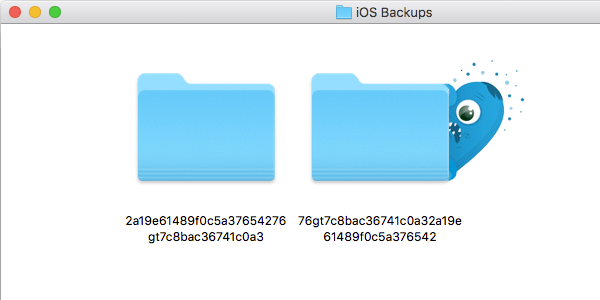
On Tuesday, BitDefender Labs announced the discovery of a new Komplex malware sample, which is a variant of XAgent, a previously known Windows and Linux malware. According to the report, the new malware was strengthened to not only steal passwords and screenshots, but also to steal iPhone backups from Macs.
While BitDefender’s report was intriguing, something didn’t add up. Important details were missing and, to be frank, the story seemed rushed, so we held back on joining the title wave of media reports that followed and instead dug down to investigate further. And boy are we glad we did!
A few hours after BitDefender’s post, Palo Alto Networks (PAN) released a story announcing the discovery of a new Komplex sample, named “XagentOSX.”
The security report from Palo Alto Networks was chock-full of details, and filled in all the gaps left open in BitDefender’s story. With all the proper details and a full analysis of XAgent available, we believe PAN to be the original source, and so in conjunction with our investigation we will use their findings to report on what we know about XAgent.
Some tasty tidbits from PAN’s report include:
We believe it is possible that Sofacy uses Komplex to download and install the XAgentOSX tool to use its expanded command set on the compromised system.
XagentOSX shares the name XAgent with one of Sofacy’s Windows-based trojans and references Apple’s previous name for macOS, OS X.
It appears the same actor developed both the Komplex and XAgentOSX tools, based on similarities within the following project paths found within the tools:
Komplex: /Users/kazak/Desktop/Project/komplex
XAgent OSX: /Users/kazak/Desktop/Project/XAgentOSX
The actor mentioned is Sofacy Group. Believed to be a state-backed Russian cyber espionage group, Sofacy Group is also known as Fancy Bear, APT28, Pawn Storm and Sednit. You may recall their involvement in not just the previously mentioned Komplex malware, but also the hacking of the world anti-doping agency as well as the Democratic National Committee (DNC) last year.
Palo Alto Networks found that, apart from expected functionality, such as gathering system information, controlling data by uploading, downloading or deleting it, taking screenshots and grabbing passwords stored in Firefox, the XAgent tool is able to check the system for iOS backups made through iTunes.
While various media outlets reported that XAgent steals iPhone backups, PAN reported that the command “showBackupIosFolder” is used to determine if a mobile device was backed up, but then speculates that the actors would use the other commands within XAgent to exfiltrate those files.
Snagging an iOS backup, which can be well over 30 GB in size, is not something easily accomplished without being detected. It is possible that XAgent looks for very specific data before it decides to take the risk of extracting a potentially large backup and being detected.
A Brief History of XAgent Malware
We encountered the name, XAgent, two years ago during a criminal hacking operation, called “Pawn Storm,” which was a spyware campaign that targeted the iOS devices of government officials and journalists. The hackers’ aim was to steal information and compromise the Windows computers of targets.
Once a high profile target’s Windows computer was successfully infected, the attackers attempted to install malware on iPhones or iPads running iOS 7 (iOS 8 at the time seemed to disable the spyware).
Apple has since improved iOS security greatly, and so going after iPhone data through backups appears to be the hackers new strategy. After all, pilfering iPhone backups makes the iOS version running on an iPhone or iPad irrelevant.
This brings forth some interesting questions. Did Sofacy Group simply re-purpose some of their old code? Has the old Pawn Storm spyware campaign merged with Komplex? It’s anyone’s guess at this point, but it is fascinating to see.
What is the Infection Vector?
As PAN pointed out, XAgent is believed to be downloaded and installed by the already present Komplex malware. Komplex was found to be distributed through spear-phishing in the form of a malicious PDF document. If Komplex is indeed the delivery mechanism, this puts the same groups of users at risk, which are those working in the aerospace industry. That said, Komplex may have also been used to attack other industries since it was found last year.
Where Does XAgent Install?
Where on a Mac computer XAgent installs is currently unknown. The only indications that a Mac is infected is by watching http network traffic for the following domains and IP addresses:
23.227.196[.]215
apple-iclods[.]org
apple-checker[.]org
apple-uptoday[.]org
apple-search[.]info
In my testing, I noticed an additional IP address that was attempted to be contacted:
72.5.65[.]94
Should Mac Users be Concerned?
When we reported on the Komplex malware last year, we mentioned:
While Komplex does not appear to be doing anything malicious after installing itself, this can change instantly if the Sofacy Group decides to send commands for the C&C servers to relay.
The recent finding of XAgent this week shows that this did indeed happen. Mac users in the aerospace industry as well as journalists and government officials have reason to be concerned. Not just because of Komplex or XAgent, but because the fields and industries they work in are more frequently under attack. We also noted:
A group like this is not likely to go away any time soon, so more malware from them can be expected.
XAgent is just the latest discovery linked to Sofacy Group, and it very likely won’t be the last. With that in mind, it is important to have your defenses up at all times.
What Steps Can Mac Users Take to Protect Yourself?
Though first reported on February 14, fortunately for Intego customers, we received the sample on February 8 and immediately updated our VirusBarrier anti-malware definitions to protect Mac users from this threat, identified as OSX/Sofacy.gen.
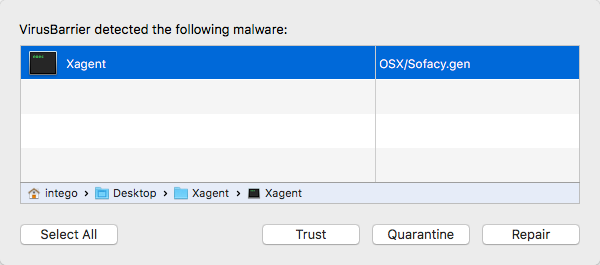
The Intego Malware Team is always hard at work looking for the latest potential threats and XAgent was already flagged as one of them—before initial reports surfaced in the media. However, because XAgent is capable of operating independently, it could have been left behind and still active on infected systems. This shows how important it is to always stay on top of the latest developments.
How to Tell if Your Mac is Infected
To manually check if a Mac is infected, the only thing you can do right now is look for Komplex components.
From the Finder menu, choose “Go,” select “Go to Folder,” and then copy/paste each of the following paths (replace $USER with your own home folder name):
• /Users/$USER/Library/LaunchAgents/com.apple.updates.plist
• /Users/Shared/.local/kextd
If the files are found, your Mac is probably infected. Move the files to your trash and restart your Mac, and then empty the trash and check the locations again. Your Mac should now be clear of Komplex, but XAgent may still be present. The exact location XAgent installs is currently unknown, so your best bet is to clear the infection by running an anti-virus solution, such as Intego VirusBarrier, which will scan the entire system and rid your machine of XAgent, if it’s present.
Before You Go, Encrypt Your iPhone Backups
With Mac malware now going after (or at least looking for) iOS backups, it’s a very good idea to use encryption to protect those backups. To do this, connect the device to iTunes and open your device’s information panel. From there, under the “Backups” section of the window, you will see the option to enable backup encryption.
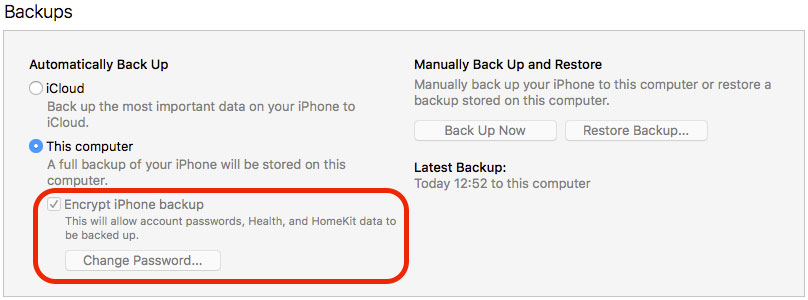
Make sure you protect your backup with a long and strong password, and consider saving it in a password manager. Without that password, restoring the backup at a later date will be impossible.