Is Safari as private as Apple claims in its ads? Here are 6 reasons why it isn’t
Posted on
by
Joshua Long
For years, Apple has been using the tagline, “Privacy. That’s iPhone.” You’ll find it everywhere, from billboards to television commercials.
Apple’s latest series of ads features a creepy flock of steampunk security cameras with wings; the cameras follow people around and invade their privacy while they browse on their smartphones. Then a warning appears on screen: “Your browsing is being watched.” Moments later, a smugly smirking iPhone user taps on the Safari browser icon. Instantly, the flying security cameras begin to explode in the sky above, amid the words, “Safari. A browser that protects your privacy.” Followed by, of course: “Privacy. That’s iPhone.”
Clearly, one shouldn’t take the ad literally; you won’t find bird-like security cameras in the real world. (Not unless you live in The Incredibles’ reality, anyway.) But Apple’s intent is clear; the company wishes to portray that privacy needn’t be even the slightest concern if you’re using its Safari browser.
Is that really true, though? Can you trust Safari to fully protect your privacy? In this article, we’ll explore six reasons why Safari may not protect you as well as Apple would like you to believe.
In this article:
- What Safari does well
- Why Safari doesn’t offer 100% privacy protection
- Safari alternatives
- How can I learn more?
What Safari does well
But first, to be fair to Apple, it’s worth noting that Safari isn’t all bad when it comes to protecting your privacy. Let’s briefly examine a few positives of using Safari, from a privacy standpoint.
Intelligent Tracking Prevention and more
According to Apple, its Intelligent Tracking Prevention feature “uses the latest in machine learning and on-device intelligence to fight… cross-site tracking. It hides your IP address from trackers so what you look at on the web remains your business.” Apple says that Intelligent Tracking Prevention is on by default. Safari includes a Privacy Report feature to show you which specific trackers it has blocked, and on which sites.
Safari has built-in support for passkeys, a password replacement technology. This makes it possible to log into certain sites that support passkeys using your own biometrics—i.e. using Face ID or Touch ID—to prove it’s really you.
In recent versions of Safari, your Private Browsing windows lock automatically, requiring your device password (or Face ID or Touch ID), when you’re no longer actively using them.
There are a handful of other Safari features designed to protect your privacy; Apple even has a Safari Privacy Overview white paper PDF (although it’s a bit out of date; it was last updated in 2019) with additional details.
It isn’t based on Chromium—a double-edged sword
Additionally, there are some benefits of not being based on the Chromium architecture used by Google Chrome (and most other browsers besides Firefox). Chromium has the biggest target on its back; cybercriminals may be less likely to specifically target Safari’s core WebKit technology, unless they specifically intend to attack Apple devices.
Not being based on Chromium also means that you can’t use Chrome Web Store extensions with Safari. As we pointed out recently, Chrome extensions are a security nightmare—so one could arguably count this as a win for Safari.
Google doesn’t have a great reputation when it comes to privacy, while Apple does. But, as we’ll explore later, Chrome gets security updates much more frequently than Safari—and that’s important for protecting your privacy, too.
Now let’s get to what Safari doesn’t (or can’t) do well when it comes to protecting your privacy.
Why Safari doesn’t offer 100% privacy protection
No matter how convincing Apple’s ads might be, Safari is not a panacea when it comes to protecting your privacy; tapping on the Safari icon isn’t a cure-all. It won’t nuke security cameras or shoulder surfers. And there are some ways in which Safari falls short—and other ways in which it simply cannot fully protect your privacy, no matter how hard it may try.
Here are six reasons why Safari might not be as private as Apple would have you think.
1. Your IP address isn’t always hidden
Similar in some ways to your home address, an IP address more or less uniquely identifies you—at least for a period of time. When you’re at home, it’s likely that your IP address rarely changes; your Internet service provider (ISP) may not reset it regularly, so all devices at your home may share the same public IP address for months. An IP address will rarely, if ever, have a direct correlation with a specific home address. However, residential ISPs often make it easy enough to pinpoint your approximate location, such as the city where you live, simply by knowing your IP address. In some cases, your IP address can even reveal your location down to the neighborhood level.
Although Apple brags that it hides your IP address from trackers, there should be an asterisk attached to that claim. It may indeed hide your IP address from some trackers, but it likely won’t recognize all of them. Blocking trackers is a cat-and-mouse game; organizations that block trackers must monitor tracking servers closely and keep their block lists up to date. (Apple relies on DuckDuckGo Tracker Radar behind the scenes.)
Moreover, unless you’re paying for an iCloud+ subscription—and also enable iCloud Private Relay—your IP address is always exposed to every site that Apple doesn’t identify as a tracker. You can work around this by using a VPN, such as Intego Privacy Protection (or another trusted VPN provider). VPNs have the advantage of protecting all Internet traffic from your device—not merely Safari’s traffic. They create a secure tunnel between your device and the VPN provider, which has other advantages—such as making it much safer to use unencrypted public Wi-Fi networks.
2. Your ISP can still track you
On a related note, unless you’re paying for either iCloud Private Relay or a VPN service, your Internet service provider can still track where you go online. This can reveal a lot about you, such as your hobbies, your political leanings, or even your sexual proclivities. Furthermore, if your government monitors your ISP’s traffic, then the government may also be able to track where you’ve been. And if you browse at work, your IT department may also be able to see which sites you visit.
This problem isn’t specific to Safari, of course. But it’s yet another reason why Safari isn’t a magic bullet for privacy protection.
Again, the paid feature iCloud Private Relay can offer additional privacy protection specifically when using Safari. Or a reputable VPN can help protect you from your own ISP or government snooping on your Internet usage, regardless of which browsers or apps you use. Just be sure that you trust your VPN provider; consider that when your VPN is enabled, all your Internet traffic gets routed through their servers. This is why it’s important to choose a VPN provider that uses the best technologies and also has strict policies in place to protect your security and privacy. For example, your VPN should have a no-logs policy that has been independently audited; this helps ensure that nobody—not even the VPN company’s employees—can know your browsing history.
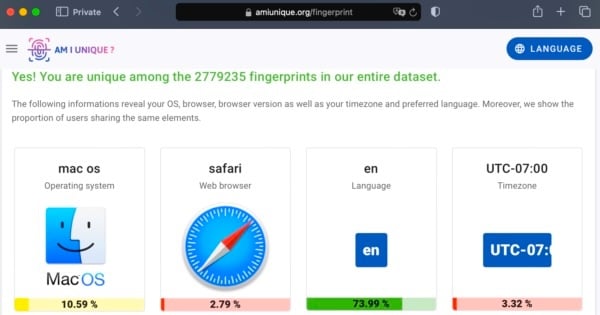
3. Safari’s “fingerprinting defense” is weak
Fingerprinting is a way for sites to uniquely identify a visitor based on metadata that can be gleaned from them. Apple claims that “Safari presents a simplified version of the system configuration so more devices look identical to trackers, making it harder to single yours out.” This functionality is even enabled by default; all of this sounds great.
But unfortunately, Apple’s supposed “fingerprinting defense” techniques seem to do little to mask your identity. Open up a site like “Am I Unique?” in Safari and you’ll see why. Very few users will have exactly the same browser fingerprint that your Safari browser does. In fact, you might even find that your browser is unique (meaning one of a kind) among the millions of fingerprints in their entire dataset. Combine that fingerprint with your IP address, and you’re potentially uniquely identifiable to virtually any site that tries hard enough to track you.
4. Apple takes too long to patch vulnerabilities
Security vulnerabilities are a major threat to user privacy.
So far in calendar year 2024, Apple has only released five security updates (each fixing multiple vulnerabilities) for Safari on macOS, iOS, iPadOS, and visionOS. On average, the Mac, iPhone, and iPad updates for Safari have been about 46 days apart from each other; for Vision Pro, it’s about 45 days. The biggest gap between Safari security updates was a whopping 77 days—from May 13 to July 29—for iOS, iPadOS, and macOS; or 81 days, from March 21 to June 10, for visionOS.
For comparison’s sake, Google has released 32 security updates for Chrome so far this calendar year (specifically looking at stable channel updates for desktop). This happens to be the thirty-second week of the year, meaning that Chrome security updates are released once per week, on average. (Some weeks, Google releases more than one update if necessary to patch vulnerabilities that are being actively exploited in the wild.) This is admittedly a bit of an apples-to-oranges comparison, because Safari and Chrome have different technologies under the hood. And, as mentioned earlier, Chrome and Chromium-based browsers dominate the market and are thus bigger targets for most hackers than Safari and its technologies.
Perhaps part of the reason for Apple’s delays may stem from the fact that Safari’s underlying technologies, including WebKit, are integrated with Apple’s operating systems. So the delays between patches likely have more to do with Apple’s patch management cycle, rather than anything specific to Safari.
It seems likely that Apple could find a way to release security updates more frequently—if this were a priority. Apple has tens of billions of dollars’ worth of cash on hand; it could certainly hire more teams dedicated to fixing vulnerabilities.
5. Safari’s default search engine is Google
Google pays Apple $20 billion per year to enshrine Google Search as Safari’s default search engine. Yes, even Apple, the supposed champion of user privacy, evidently has a price at which it’s willing to sell out.
Admittedly, Google does have one of the best search engines in terms of how it indexes the Web and ranks search results; aside from the revenue stream, that’s reportedly one of the main reasons why Apple prefers to default to Google Search. But even setting aside the discomfort of Google’s less-than-stellar privacy record (which we’ve covered in the past), there’s another major reason why making Google the default search engine is a poor choice for user privacy.
Google Search has a malvertising problem
Repeatedly throughout 2023 and 2024, malware researchers have caught malicious Google Ads at the top of search results. These ads convincingly impersonate software developers; if you’re not careful, they can lead to malware infections. Yes—even on a Mac (and hypothetically, on iOS devices in the EU). Most malware for macOS or Windows that’s distributed through Google Ads malvertising is of the “stealer” variety; such malware will attempt to gather and exfiltrate your passwords, browser cookies that keep you logged into sites, cryptocurrency wallets, and more.
In short, using Google as your default search engine can, if you’re not careful, lead you to inadvertently download privacy-violating malware. This can potentially happen with other search engines that display ads, such as Bing, but there are numerous documented cases of dangerous Google Ads in the past year alone.
(Even before it became in vogue to buy malicious Google Ads, search engine poisoning has been a thing for at least 15 years; I wrote about several different examples of this on Google and Bing in 2009. Most malware makers will likely put more effort into ranking highly in Google or Bing search results than any other search engine; Google has 91% market share, followed by Bing at just under 4%.)
Thankfully, Safari does allow you to switch your default search engine. One of the options is DuckDuckGo, a privacy-focused search engine. Apple doesn’t support Brave Search, however. (Learn how to change your Safari search engine on Mac, iPhone, iPad, or Apple Vision Pro.)
6. Private browsing windows last indefinitely
There’s an oddity in the way Safari handles private browsing windows and tabs. Namely, they all come back after quitting the browser, or even restarting your device. To my knowledge, Safari is the only browser in the world designed to behave this way by default.
Some might see that as a benefit; you can restart your Mac or iPhone to install security updates, and then pick up where you left off. (Well, more or less; you may have to sign in again, if you were logged into a site in a private tab.)
But is this actually ideal behavior for a private browsing window? It really depends on the specific reason you use private browsing.
If your goal is to prevent anyone else who shares the device with you from seeing where you’ve been, then you’ll have to remember to manually close all private browsing tabs and windows before quitting Safari.
Safari alternatives
Of course, there are alternative browsers available for Mac, for iPhone and iPad, and even for visionOS. Some may protect your privacy better than others. Brave is one of the most privacy-oriented browsers, and it defaults to Brave Search—a privacy-focused and AI-enhanced alternative to Google Search.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()