How to use a Security Key to protect sensitive online accounts
Posted on
by
Kirk McElhearn

Protecting your online accounts has become more important, as so much of our lives takes place on websites, via email, and through messaging. If someone gets access to some of your accounts – especially your email account – they can get access to others, and potentially usurp your identity.
In order to ensure security, most sensitive services now offer two-factor authentication (sometimes called two-step authentication). This combines something you know – your user name and password – with something you have, which is generally a code that is generated on demand. In many cases, these codes are sent by SMS text messages, and must be used within a few minutes. But SMS is inherently insecure, and other methods are needed to ensure optimal security.
Security keys are another way to add an additional authentication factor. They are portable, like flash drives, and easy to use. In this article, I’m going to explain why you might want to use a security key to protect certain accounts, how to set one up, and how to use it.
Why SMS is insecure
SMS is practical and fast, but it has security risks. SMSs are not encrypted, and can be intercepted in transit. Someone could steal your phone, and, even if they can’t unlock it, if you have your device set to show the content of your messages on the lock screen, they can see your codes as they arrive. Or someone could clone your phone, getting a SIM card with the same number as you, intercepting your messages in real time.
Authenticator apps are another option. They create unique, time-limited, one-time passwords. Each code is valid for thirty seconds, because both the server you’re logging into and the authenticator app know what time it is. Your authenticator app, or password manager handling these codes, shows a countdown as the time progresses, and generates a new code when the time runs out.

A security key is essentially a mini flash drive that contains a tiny bit of data, which is a cryptographic key. When you plug it into your computer, that data is read, and it works like a key in a lock, providing a second factor that unlocks a digital door. Unless someone has your security key, they can’t get into your account. They use the FIDO2 protocol, which has been widely adopted by major tech companies, but is far from universal.
Why use a security key?
You don’t use a security as much for your own logins but rather to prevent others from accessing your accounts. It may seem to be a hassle to have to stick a key into a USB port every time you log into a website with a new device, but you generally only have to do it once on each device. From that point on, you can choose to trust your device and you won’t need to use the key again for some time (many services require a new, full login, whether with a one-time code or security key, at regular intervals). And if you lose the security key, you can revoke it on the website, so no one else can use it to access your account.
Because of the various types of ports and connectors used on computing devices, security keys come in many versions. This can be a problem if you want to use a key with, say, an iMac, a MacBook Pro, an iPhone, and an iPad. Some keys work with NFC (near-field communication), allowing wireless recognition with iPhones, but not iPads, and others are available with Bluetooth. One brand, Yubico, makes its keys in the following versions:
- USB-C and Lightning
- USB-A
- USB-C
- USB-A and NFC
- USB-C and NFC
You can use adapters for the different USB plugs, so a USB-C key will also allow you to use it with a USB-A port or vice-versa.
Google’s Titan Security Key is available in a bundle that includes:
- USB-A and NFC
- Bluetooth
The Titan Security Key bundle includes a USB-A to USB-C adapter, and a mini-USB to USB-A adapter for the Bluetooth key, which allows it to work via USB, but also to charge the device which contains a battery.
I tried both of these security keys, each of which cost about $50, and the Google bundle was by far the most practical: Bluetooth is more widely supported than NFC, and all my portable Apple devices can work with this key.
Which services support security keys?
A wide range of services support security keys. You can protect your Google and Microsoft accounts, you can use a security key with Dropbox, Twitter, Facebook, Instagram, and YouTube, and a number of password managers support these devices.
Until 2023, one notable absence was Apple services. This was because Apple typically uses its own method for two-factor authentication based on the company’s chain of trust across devices. But as of 2023, you can opt in to protect your Apple ID using physical security keys, as long as all devices signed into your Apple ID are running macOS Ventura 13.2, iOS 16.3, or iPadOS 16.3, or later versions.
Even before Apple implemented security key support for Apple IDs, you could use a security key to protect your Mac, as a variant of the “smart card” authentication available since, macOS High Sierra 10.13. They key would be required every time you log into your Mac, and it’s a fairly complicated process, and should only be set up by experienced system administrators.
It’s worth noting that Google has an Advanced Protection Program for “users with high visibility and sensitive information, who are at risk of targeted online attacks.” Designed for journalists, activists, and politicians, this requires the use of a hardware key.
Setting up a security key
In general, setting up a security key is simple, but it’s not always easy. While Yubico lists many services that support security keys, some of them actually only use the Yubikey via the company’s Yubico Authenticator app to generate one-time codes. While using the key is slightly more secure than generating a code with an authenticator app, it’s probably not worth the extra step.
Google doesn’t provide much information on how to use their Titan Security Key, other than what you will find for setting up your Google account. But Google’s instructions are a good way to see how this works, and most services have similar procedures to add a security key to your account.
If you haven’t yet turned on two-factor authentication for your account, then you must do so; the security key is the second factor. If you already have two-factor authentication enabled, then you’ll want to add the security key and turn off text messaging if you had that enabled.
You then “enroll” your security key; as you see in the screenshot below, I could use my iPhone as a security key, but if you click the second option, you can add a hardware key.
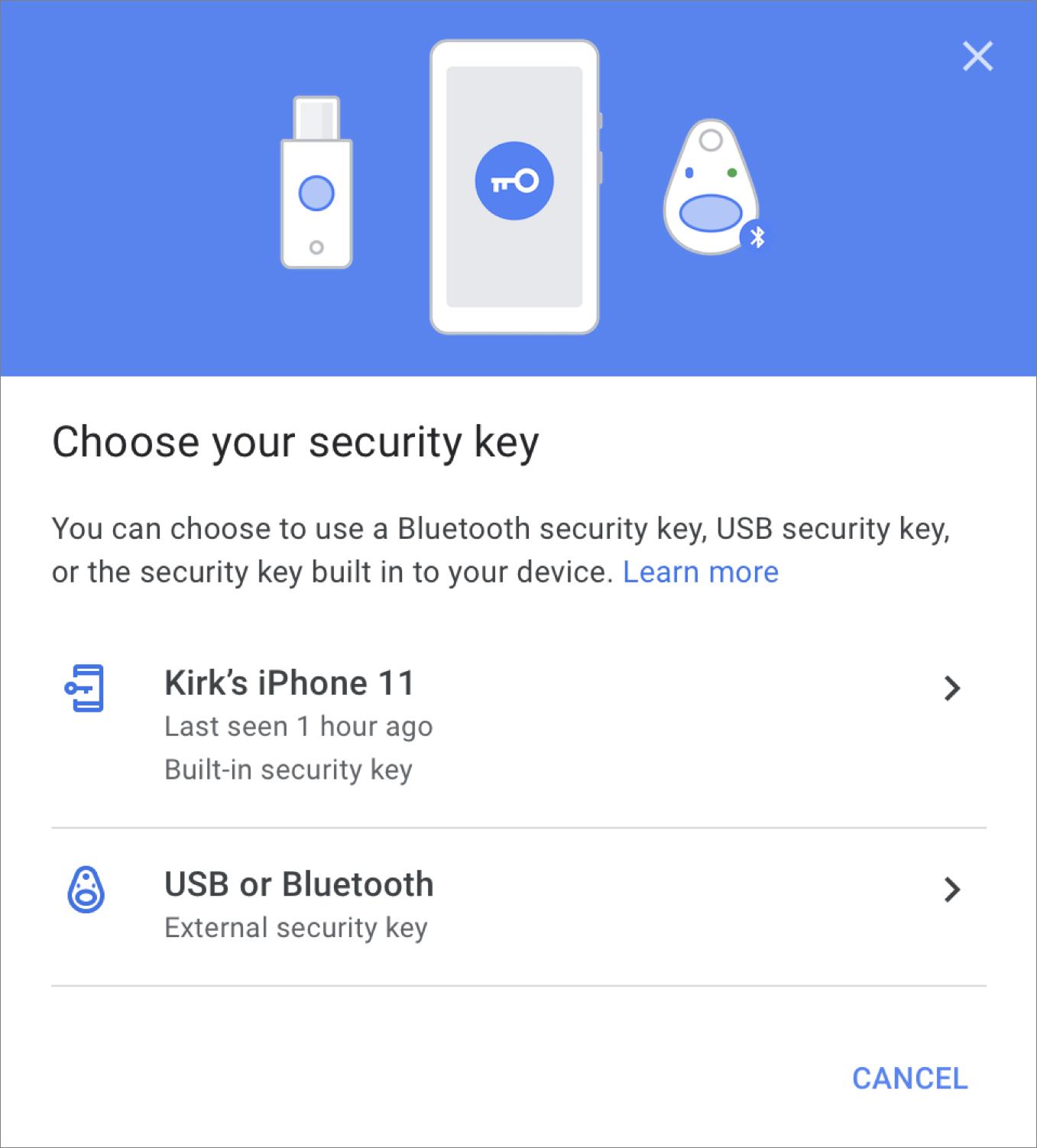
You then connect the security key, and Google registers it, and that’s all there is to do. It’s worth noting that to be able to use a Bluetooth security key on other devices, you need to first connect it physically to a computer when enrolling it, using the supplied cable. After that, you can use the device via Bluetooth to log in on an iPhone or iPad: just press a button on the Bluetooth security key when asked when logging in.
Not all services allow you to use multiple security keys, but Google does, and this can be practical to ensure you have backups.
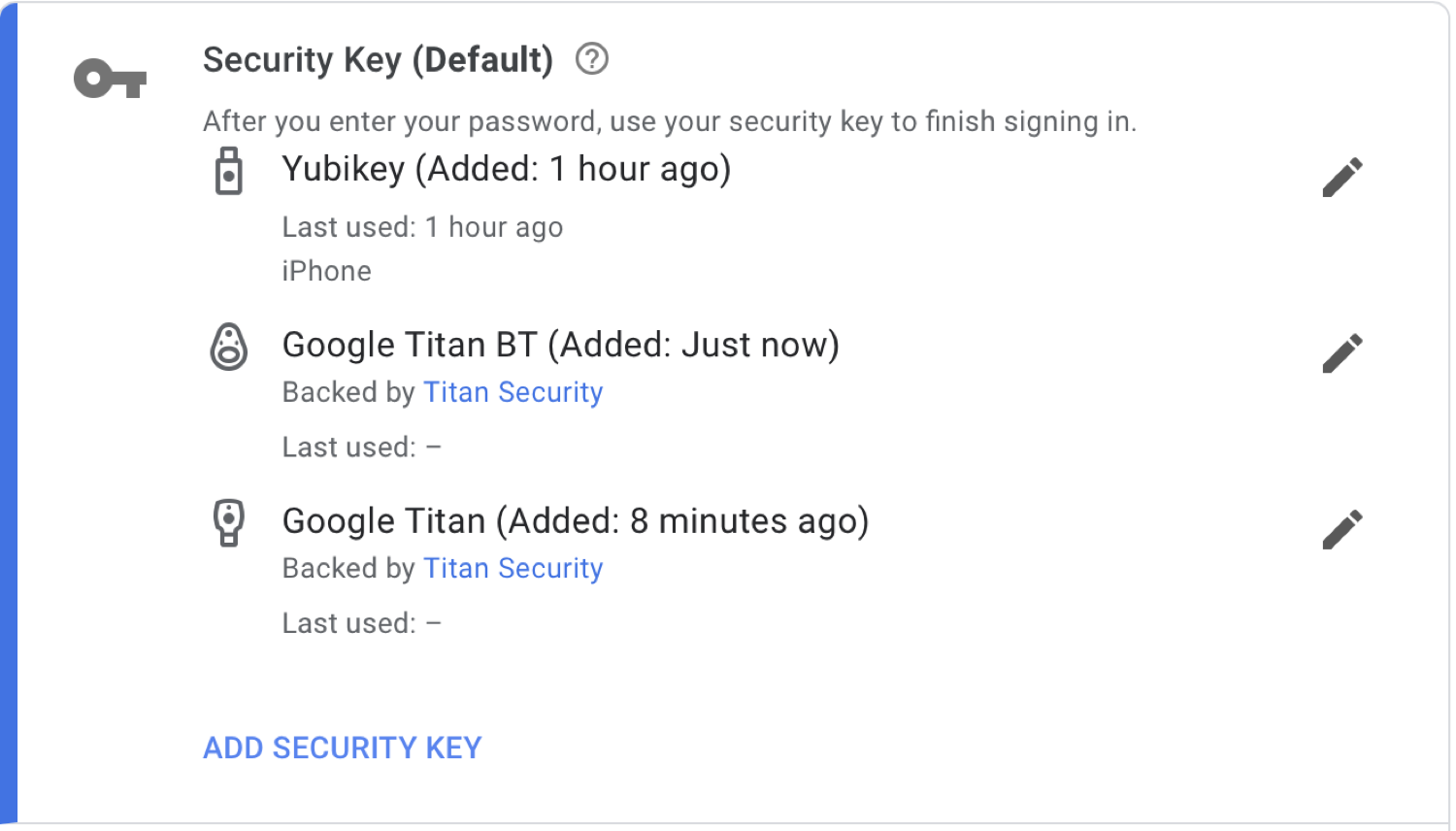
With some services, you can choose to have multiple authentication methods active. For example, Twitter allows you to use text messages, an authenticator app, and/or a security key, but notes that you can’t use a security key with their mobile app.
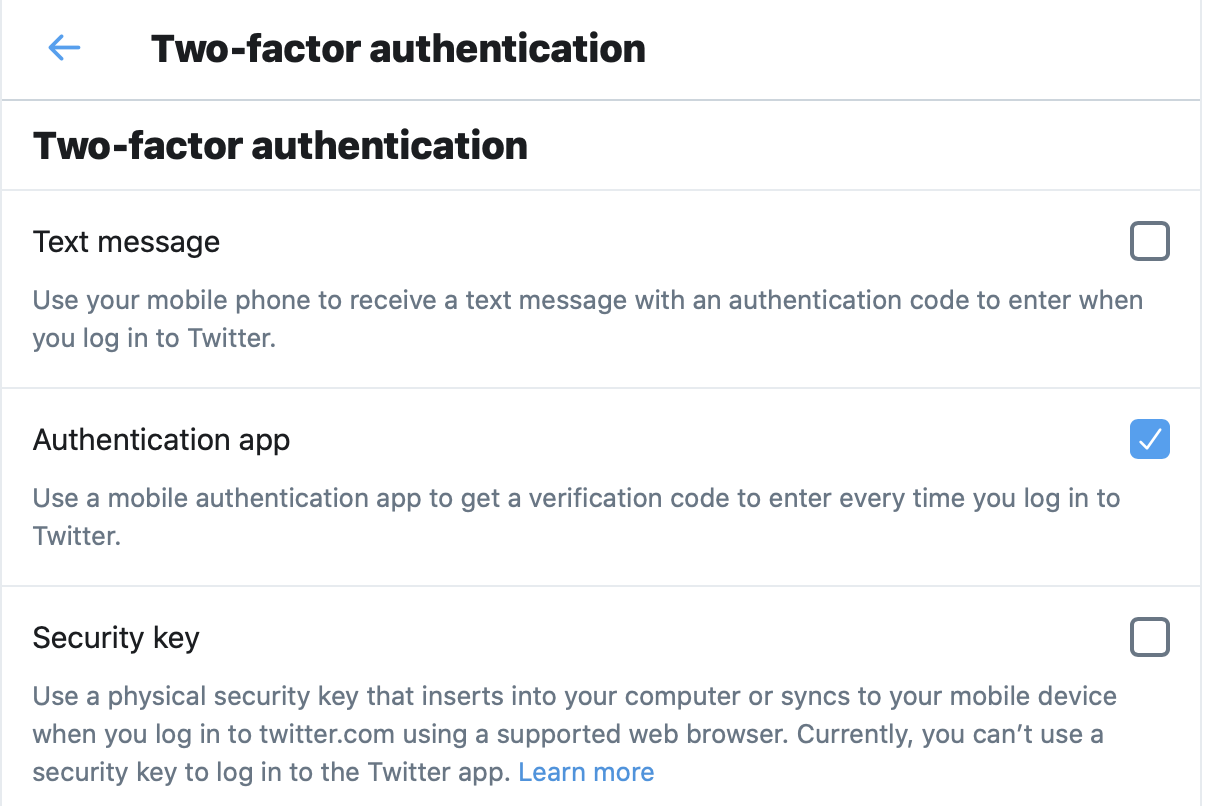
If you want to use security keys to sign into your Apple ID, see our separate article on how to protect your Apple ID account with security keys on iPhone, iPad, or Mac.
How to protect your Apple ID account with Security Keys on iPhone, iPad, or Mac
There are risks that these hardware devices may not always work, because the device you’re using to log in isn’t compatible, or because you’ve lost the security key. Most services that offer two-factor authentication with an authenticator app or security key also provide backup codes, which you can use if your preferred method isn’t available. With some services, such as on Twitter, this is a single code, in others, such as Google, you get ten single-use codes; once you’ve used a code, you can’t use it again (but you can always generate new codes). But if, as above, you can use both a security key and an authenticator app with Twitter, it might be best to allow both options.
Computer security is always a trade-off between robustness and convenience. While a hardware security key is one of the most secure ways of protecting your accounts, it is not the most convenient. But that extra step is generally something you only need to do occasionally: unless you log into public or shared computers often, you use them only when you log into a new device, or every month or so, depending on how often the service wants to you reconfirm your identity.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()