How the Internet Works
Posted on
by
Kirk McElhearn

It’s become second nature to use the internet for web browsing, email, messaging, and streaming music and video. It’s a bit like how we use electricity: we have a vague idea how it’s generated and how it gets to us, but we are rarely concerned about the details.
The difference with the internet is that you share personal information with retailers and social networks, provide detailed financial information to banks and investment firms, and tell some of your deepest secrets to friends and family.
Security and privacy are (or at least should be) key concerns for internet users. To fully grasp why these are so important, it’s helpful to understand how the internet works. In this article, I’m going to give you an overview of how the internet works, how your data gets from one location to another, and why it’s important to protect your privacy and security online.
Introduction: TCP/IP
Before outlining how various internet services work, it can help to understand a bit about how most internet traffic is sent and received. The TCP/IP protocol, or the Internet protocol suite, describes how “data should be packetized, addressed, transmitted, routed, and received.” Entire books have been written about TCP/IP, but what is important to understand is how this protocol controls the way your data is sent from one computer to another.
When you send data, is it split into “packets,” or small bits of data. When you send a photo, it’s not sent as a whole; in fact, it’s broken up into packets that allow the data to be efficiently sent and reassembled when they get to their addressee. Each packet contains information about its final destination, so each router it passes through can direct it accordingly. Error correction is used so each packet is checked, using mathematical calculations, when it reaches its final destination; if there are mismatches, the computer receiving the data requests to the sender that they be resent. And all these packets are reassembled in order to reconstitute that photo, so your parents can see a picture of their grandchildren.
Because the data is fragmented, each packets can take a different route, perhaps going via different cities, or even countries. Your data doesn’t go in a straight line, or over an isolated connection between two computers, but rather through a vast network of devices.
Connecting
All activity over the internet starts with a request from a computer (which could be a desktop computer, a handheld device, or something as banal as a light bulb) to a server. A server is simply a computer that responds to requests by sending some information in return. This can be a web server (which hosts or generates web pages), a file server (which stores files, and allows you to download them), a time server (which returns the current time when a device requests it), and more.
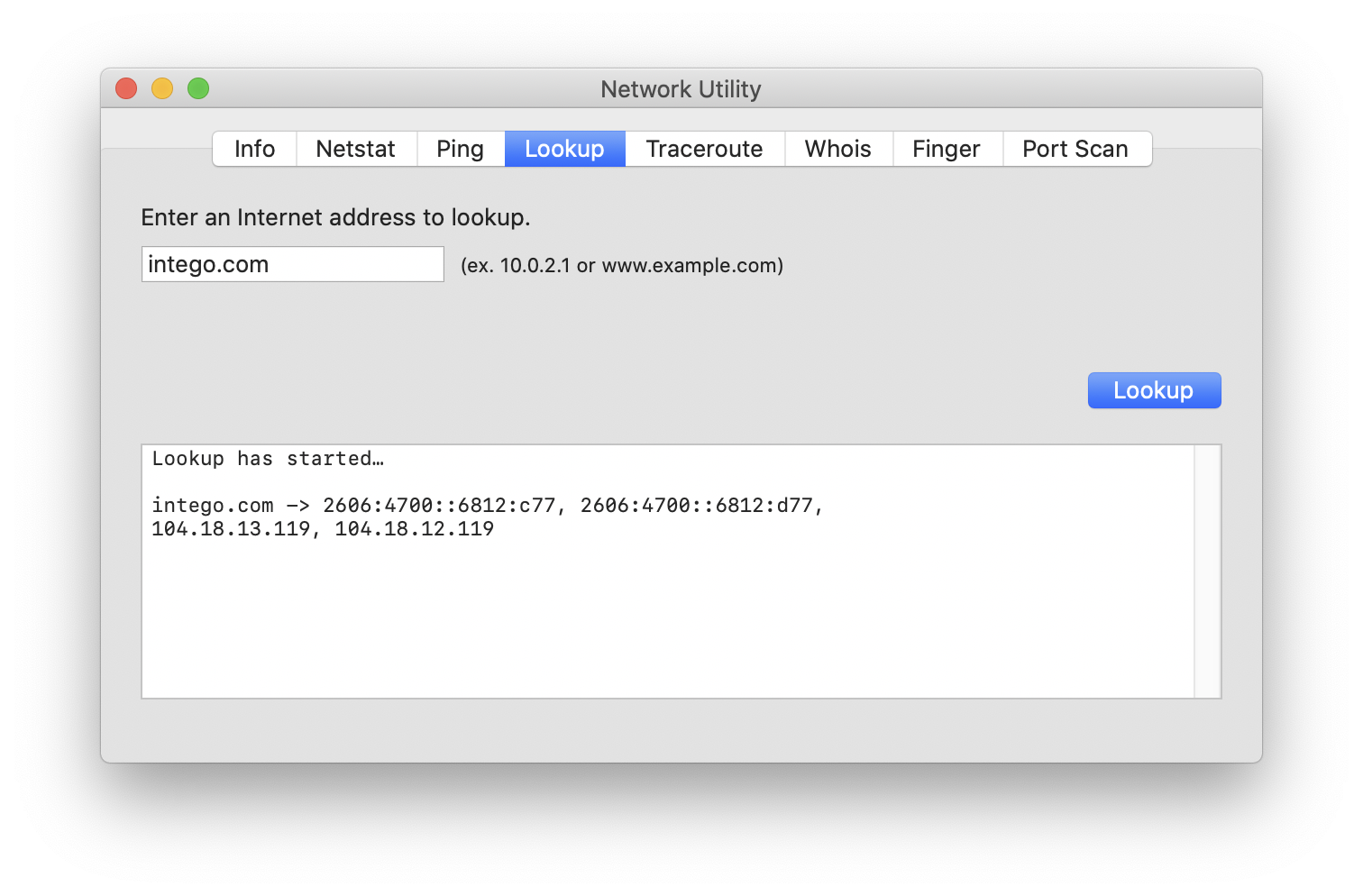
Many requests for internet resources begin by using the domain name system, or DNS, to translate an internet address (such as intego.com) into the precise IP address (internet protocol address) of a server. It’s much easier to remember “intego.com” than it is to remember “104.18.13.119,” so DNS allows servers to have much more memorable names.
Generally speaking, each server and each home router (or other device connected directly to the internet) has a unique IP address, sort of like a phone number (with its country code and area code, to ensure that all numbers are unique around the world). One way to find out the IP address behind a domain name is via the Network Utility app, which is in /Applications/Utilities on a Mac.
Once that numerical address is found, your request is sent. It goes through a number of devices to get to its destination, which may include:
- Your home router, if you are at home; a cellular mast, if you’re using a mobile device; a Wi-Fi access point, switches and routers, and a firewall, if you’re on a business network.
- A long series of cables, going underground, overground, and even underwater; or one or more satellites (though this form of communication is quite slow, because of the distance to geostationary satellites).
- Additional routers (devices that intelligently route and forward network traffic) in your town or city, in other cities, and even in other countries.
There’s no single straight line between any two points on the internet. When you send a request to a service, your data makes a number of hops, going through many other routers before reaching the destination server. You can see the path (or route) using Network Utility, on the Traceroute tab. Enter a domain name, then click Trace to see how many hops it takes to get to your destination.
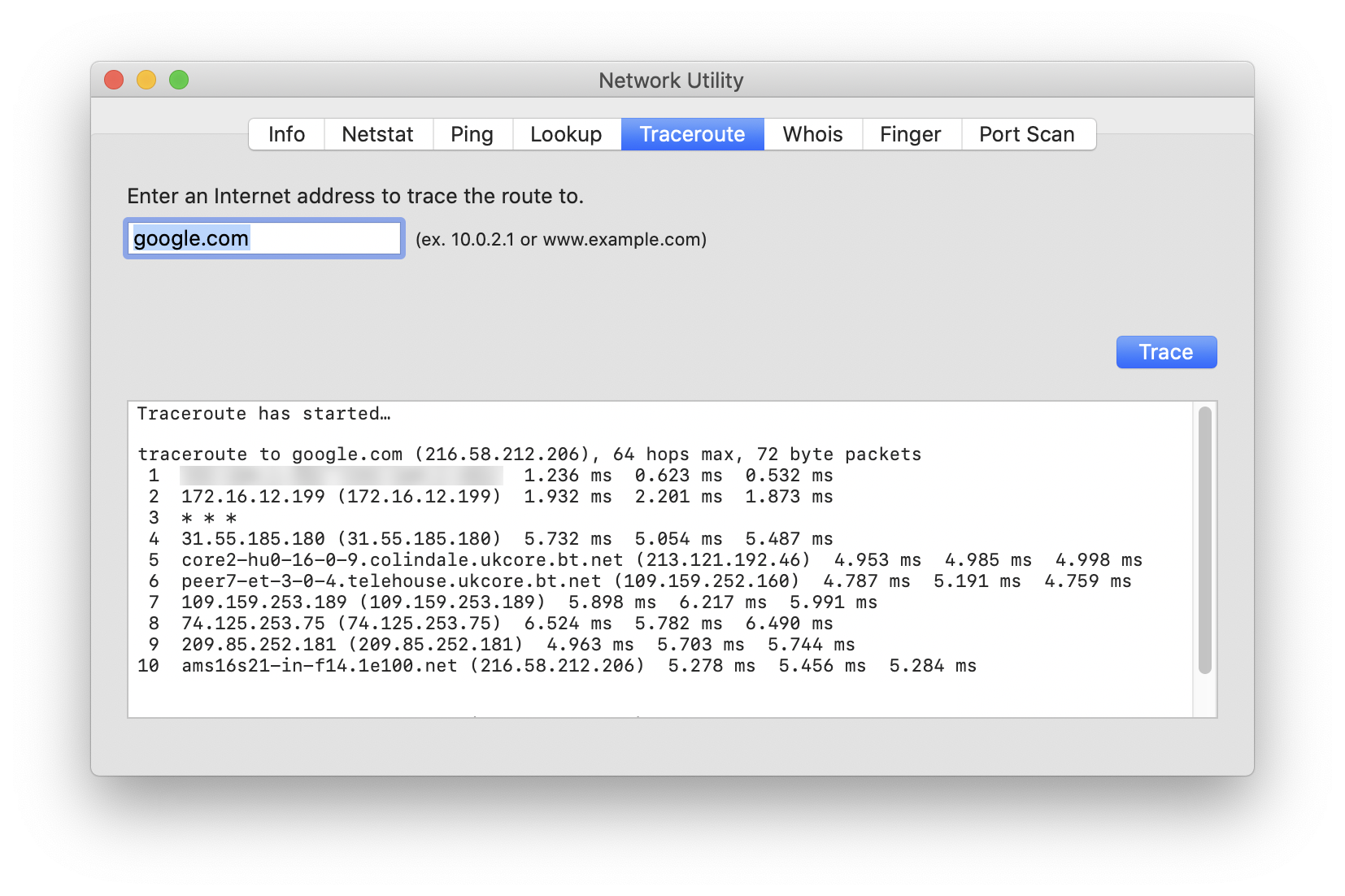
Note that some routers don’t respond to the types of packets sent when you run a traceroute, so you may see asterisks (***) in the results.
How websites work
Originally, websites worked with a series of individual pages, each of which could contain links to others. If you wanted to view www.intego.com, a web server would get your request and load the default page for that domain, usually at an address like http://www.intego.com/index.html, and display its content. That page would be static, until someone manually changed its code.
Nowadays, most web pages are dynamic, meaning that they don’t exist as pages, but rather as elements in a database that are assembled on request. So if you go to www.intego.com, a database on Intego’s web server receives your request, and builds the page for you. This process means that pages can update automatically as the different elements in a page are updated. And the process is a lot more efficient than storing thousands, or potentially hundreds of thousands of pages, on large websites such as newspapers. And they can update automatically as new data arrives, such as the time, the temperature, or new stories on a newspaper’s home page.
With big websites, you often go through a content delivery network, or CDN, which consists of many servers located throughout the world. CDNs ensure that content can be provided quickly to users anywhere in the world, rather than all requests being served by a single server in one location. If a server gets more requests than it can handle because too many people are trying to access it simultaneously, it may be slow, or may even be unable to respond to users’ requests.
A company like Apple—which has tremendous demands for content such as pages on their website, downloads from the iOS App Store and Mac App Store, streaming music and video, and more—uses massive content delivery networks to meet the needs of users.
Websites and security
Website addresses start with either http:// or https://. The former means hypertext transfer protocol, and the S in the latter means secure. HTTPS websites use certificates that are guaranteed by trusted third parties, companies or organizations that certify the ownership of websites, and that allow encryption to be initiated between your device and the web server you contact. When you connect to a secure website, web browsers display a padlock in the address bar, and browsers alert you when you visit a site whose certificate is invalid or expired.
Once a secure connection is established, you can be sure that data you send, for example credit card information, is encrypted; this helps ensure that your data cannot be intercepted or modified en route. The same is true for data sent to you by a website. So, if you access your email via your web browser, it cannot be intercepted by someone who may intercept your traffic. (See below for more about email.)
It’s worth noting that some web browsers protect your privacy more than others. Have a look at two articles about the most private browsers for Mac, and the best private browsers for iOS and iPadOS.
How email works
Email is one of the most common forms of messaging in the world. Yet email is inherently insecure. As you saw above, your data travels from server to server in packets, and is reassembled when it reaches its destination. Even if you have a secure connection to your email provider, that email might be stored unencrypted when it reaches its mail servers (and your emails may be forwarded through many servers, and may be replicated on multiple servers to ensure quick access and redundancy).
Emails generally remain on servers for a long time—you may have years of emails you’ve sent and received in your account—so they may be vulnerable until deleted. And when you send someone an email, you have no idea what they will do with it. They could, for example, forward it to someone else without your knowledge. You also have no control over what happens when your email reaches the destination server or a recipient’s mail app; at times the contents of your message may not be stored securely.
When sending an email, imagine that it is like a postcard. Assume that someone else besides the intended recipient may read it.
Thankfully, there are ways to encrypt email to ensure that only the intended recipient can view it; we discuss some such services in this article.
Instant messaging
While email has some inherent insecurities, not all instant messaging is based on the same standards, and as such not all instant messaging services are created equal. They can be extremely secure, if they use end-to-end encryption (E2EE). Apple’s iMessage and FaceTime use E2EE. When you send a message via Apple’s Messages app to another iPhone user, the text bubble background color will be blue, which means it was sent via iMessage and was encrypted during transit. (A green background indicates that it was sent as an SMS or MMS, which are less secure.)
If someone’s computer or device is compromised, then it may be possible for an attacker to read all of someone’s instant messages, even if they were sent using E2EE.
In addition to Apple’s iMessage, other services, such as Signal, Telegram, and WhatsApp also provide secure messaging. But don’t assume that common messaging platforms like Facebook, Instagram, or Twitter are secure; as we explain in The Great Twitter Hack of 2020, hackers accessed troves of instant messages on Twitter.
Summing up
There’s a lot more to the internet than what I’ve discussed in this article, but I’ve covered several of the main services and how they function, in order to highlight some security risks inherent in internet communication. It’s important to be aware of the risks involved when you send or share sensitive information, so you can be more aware of how your data may be handled in transit, and when it is protected.