Recommended + Security & Privacy + Software & Apps
How safe is the Mac App Store? Privacy-violating apps uncovered
Posted on
by
Joshua Long

Security professionals often advise users that Apple’s Mac App Store is one of the safest places to download apps.
After all, Apple has a review process that’s supposed to help prevent potentially harmful apps from ever being published. Additionally, App Store apps are sandboxed, which is supposed to limit apps’ ability to engage in undesirable behavior. Together, Apple’s app review process and sandboxing theoretically make the App Store a more trustworthy software source than most.
Lo and behold, new information has come to light that calls into question the safety of the App Store platform. Many apps have recently been caught doing unscrupulous things, circumventing protections supposedly provided by the App Store, and invading users’ privacy.
So then, just how safe is the Mac App Store? And what should Mac users do?
Multiple independent sources find privacy-violating apps
Last Friday, a few Mac security researchers independently published their findings regarding a number of Mac App Store apps that employ questionable tactics, violate Apple’s guidelines, and spy on victims’ computer activity.
A Twitter user going by the name “Privacy 1st” (@privacyis1st) recently found some suspicious behavior in a popular App Store app, called Adware Doctor (full App Store title: “Adware Doctor:Anti Malware &Ad“) and began tweeting about it. Privacy 1st reached out to a Mac security researcher, Patrick Wardle, who did further investigation of his own.
Privacy 1st and Wardle discovered that Adware Doctor—which recently achieved App Store stardom as #1 in Top Paid Utilities and #4 in Top Paid Apps—was stealing users’ browsing history and more.
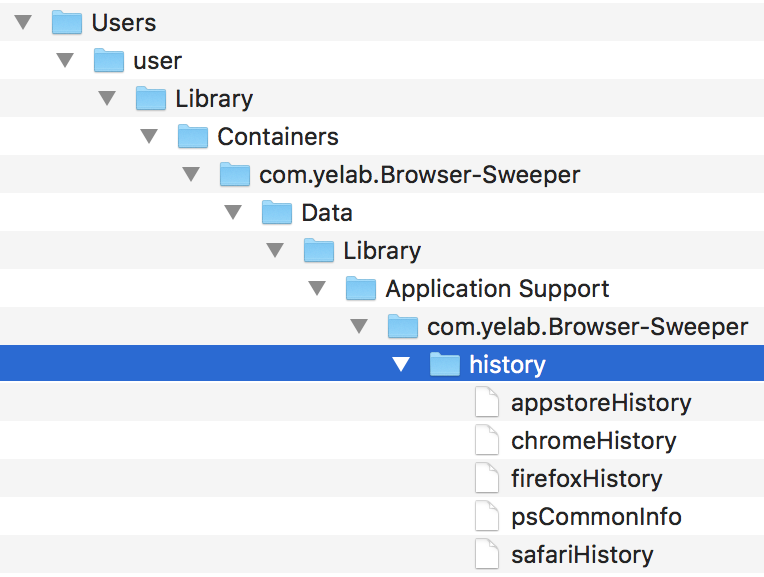
Adware Doctor steals Chrome, Firefox, and Safari browsing history, among other things. Image: Wardle
For an app that claims to search for adware on the user’s account, it’s no surprise that Adware Doctor requests access to the user’s home directory, since that’s where any adware would reside. However, after the user grants this access, the app proceeds to do some questionable things—unrelated to the adware scan—without informing the user.
In the background, Adware Doctor creates a password-protected zip archive containing the user’s Chrome, Firefox, and Safari browsing history, as well as the user’s App Store search history and a list of all the running apps, and then sends that zip archive to a server that’s evidently located in China.
All of this is done without the victim’s knowledge or consent.
This behavior is not at all justifiable. Another researcher, Thomas Reed, notes in a follow-up article that one could argue that a malware or adware cleaning app might want to check recently browsed sites in an attempt to identify and report back about the source of an infection; however, the user is never informed about or asked to consent to this activity, which takes place surreptitiously in the background—even when no adware is found on the system.
Web browsing history can contain very private, personal, or sensitive information. Often it can contain personally identifiable information, or strong clues as to the exact identity of the user. It may reveal things such as home and work addresses (e.g. via Google Maps searches), medical conditions (e.g. via search engine or medical site queries), sexual orientation or fetishes (e.g. via the types of dating sites visited), and a multitude of other things that should not be freely available to an app developer without obtaining the user’s explicit consent.
Which apps behaved this way?
Unfortunately, Adware Doctor was just the tip of the iceberg.
Researchers warned of several other Mac App Store apps that have been behaving in similar manner, collecting browser history without the user’s consent, and even compressing it into a password-protected zip file and sending it off to the developer, just like Adware Doctor was doing.
Adware Doctor and two other apps (“Komros Anti Malware & Adware” and “AdBlock Master:Block Popup Ads“) by the same developer, Yongming Zhang, were removed from the Mac App Store on Friday after the publication of Wardle’s article—a month after Privacy 1st and Wardle reported the illegitimate behavior to Apple.
But it wasn’t just a single rogue developer engaging in these privacy-compromising tactics.
Three additional apps, evidently developed by the 30-year-old security company Trend Micro, were called out by Reed and a forum user known as “PeterNopSled” for using the same technique to exfiltrate users’ browsing history as far back as December 2017:
- Dr. Antivirus
- Dr. Cleaner
- Open Any Files: RAR Support
The latter app, Open Any Files, seems to have been removed from the App Store sometime over the weekend.
On Sunday, eight more Trend Micro apps were pulled from the Mac App Store, including the aforementioned Dr. Antivirus and Dr. Cleaner apps, and Dr. Unarchiver which was called out by 9to5Mac’s Guilherme Rambo:
- Dr. Antivirus: Remove Malware
- Dr. Cleaner: Disk, Mem Clean
- Dr. Cleaner Pro: System Clean
- Dr. Cleaner Elite – Disk, Memory, System Optimizer
- Dr. Unarchiver: RAR & Zip Tool
- Dr. Battery: Health Monitor
- Duplicate Finder – File Clean
- No Sleep:Keep screen light on
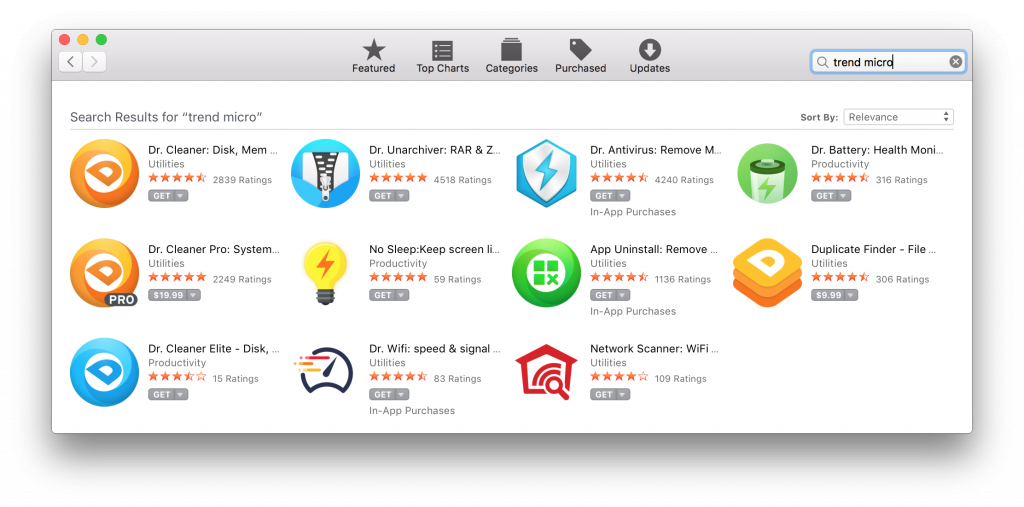
Several apps evidently published by Trend Micro were removed from the Mac App Store on Sunday and early Monday—all the apps shown here except for the two Wi-Fi apps.
In the early hours of Monday morning, another app, App Uninstall: Remove Application and Its Service Files for Complete Uninstallation, was removed from the App Store, leaving only two Trend Micro apps remaining in the store: “Dr. Wifi: speed & signal test” and “Network Scanner: WiFi Security.”
Incidentally, Microsoft’s Windows application store still lists Windows 10 versions of at least two of these apps, Dr. Cleaner and Dr. Unarchiver. It is not yet known whether the Windows versions attempt to exfiltrate similar data, but early observations suggest that the apps may have been ported from Mac to Windows, so it’s possible that they might contain similar functionality. Trend Micro has issued a statement, saying, “Windows products and enterprise products do not have this feature”; see below to read more from the statement.
Did Trend Micro really develop spyware?
One might reasonably ask whether the apps listed above are really from Trend Micro, or whether they were created by someone merely claiming to be Trend Micro to benefit from the company’s reputation.
Evidence suggested but did not conclusively prove that the apps may have been developed by Trend Micro. The zip files collected by the apps are uploaded to update.appletuner.trendmicro․com, a subdomain of Trend Micro’s main site. Additionally, a May 2018 article on Trend Micro’s blog advertises and links to Dr. Cleaner, Dr. Antivirus, Dr. Unarchiver, and Dr. Battery in the Mac App Store.
What remained unclear is when and why the data exfiltration began.
Had exfiltration always been a “feature” of these products, or was it only added recently, and what was the purpose of collecting this private data? Was the company massively compromised by an attacker? Was there a rogue developer within the company? Did the company somehow forget to ask users’ permission before taking their private data? Even if the apps were acquired by Trend Micro through an acquisition (which is merely one theory), that would not fully explain how the data began to be exfiltrated to a Trend Micro server without the company knowing it was collecting users’ browser history.
On Monday, Trend Micro issued a statement, which reads, in part:
Trend Micro has completed an initial investigation of a privacy concern related to some of its MacOS [sic] consumer products. The results confirm that Dr Cleaner, Dr Cleaner Pro, Dr. Antivirus, Dr. Unarchiver, Dr. Battery, and Duplicate Finder collected and uploaded a small snapshot of the browser history on a one-time basis, covering the 24 hours prior to installation. This was a one-time data collection, done for security purposes (to analyze whether a user had recently encountered adware or other threats, and thus to improve the product & service). The data collected was explicitly identified to the customer in the data collection policy and is highlighted to the user during the install. The browser history data was uploaded to a U.S.-based server hosted by AWS and managed/controlled by Trend Micro.
Trend Micro is taking customer concerns seriously and has decided to remove this browser history collection capability from the products.
Following Trend Micro’s statement, Reed stated publicly that when he had installed the apps, he had looked for any notification within the apps that disclosed the data collection but “did not find any,” and that he was willing to share those versions of the apps with other researchers who wished to verify this.
Trend Micro further updated their statement on Tuesday, adding that they “have permanently dumped all legacy logs,” but they made no statement about what they would do to either prevent or automatically delete future logs that old versions of the app may attempt to upload. The company also stated:
[…] we believe we identified a core issue which is humbly the result of the use of common code libraries. We have learned that browser collection functionality was designed in common across a few of our applications and then deployed the same way for both security-oriented as well as the non-security oriented apps such as the ones in discussion. This has been corrected.
The implication is that Dr. Antivirus was supposed to have collected browser history as an intended feature, but several other Trend Micro consumer Mac apps had reused the same code.
What can be done about this?
Apple has removed the known offending apps from the Mac App Store.
However, a more thorough investigation of App Store apps is certainly warranted. The Mac App Store contains a plethora of obscure and questionable-looking apps that claim to “clean” or “scan” one’s system, all of which presumably request full access to the user’s home directory and could potentially exhibit similar behaviors.
If you’ve purchased or downloaded an app within the last 90 days that you believe may be malicious, you can go to https://reportaproblem.apple.com (or e-mail [email protected] with a link to the offending app) to file a report with Apple or to request a refund.
Of course, if your private information has already been exfiltrated, you won’t be able to get it back.
Can the App Store be trusted?
In spite of the rather unfortunate news about the misbehavior of App Store apps and the delays of up to nine months prior to Apple removing them, obtaining software through the Mac App Store is still probably somewhat safer than doing a Google search for an app and clicking on whatever you happen to see in the results. It still takes a bit more effort for shady developers to circumvent Apple’s review process, and Apple should certainly learn from this incident and add detection for similar behavior into its app review workflow.
It’s clear that one should not blindly trust everything in the App Store—on macOS or even on iOS.
(Incidentally, Forbes reported late Friday that an iOS security researcher, Will Strafach, warned about iPhone apps “covertly” selling users’ location data.)
How to stay safe when shopping in Apple’s Mac or iOS App Stores:
- Whenever possible, stick with developers you already know and trust. If you must download an app from a developer you don’t know, check out their other apps, and try to look up the developer to see if you can find out anything about their reputation.
- Don’t automatically trust excessively positive app reviews or apps with an unusually high volume of positive reviews; sometimes fake or paid reviews are mixed in to make an app seem more popular or trustworthy than it really is.
- Check out what the more critical reviews have said by selecting “Most Critical” from the “Sort By:” menu.
- Read the app’s privacy policy; all App Store apps submitted or updated on or after October 3, 2018 will be required to have a privacy policy.
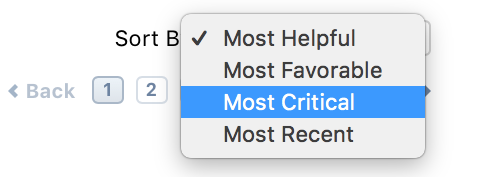
In the Mac App Store, you can sort user reviews by most critical first.
While not foolproof, these tips should help you make more informed choices about the apps you choose to download from the iOS and Mac App Stores.
Where can I learn more?
Keep an eye on The Mac Security Blog for updates on this story as well as other Mac news and security and privacy stories.
We’ll talk about the safety of the App Store on an upcoming episode of the Intego Mac Podcast. Subscribe now to make sure you don’t miss an episode!
Further reading:
- Weighing the Pros and Cons of Apple’s Mac App Store
- How to Manage Privacy Settings on Popular iOS Apps
- Unwanted Cryptomining Debuts (Briefly) in Mac App Store
