Expect .zip and .mov domains to be used in phishing and malware attacks
Posted on
by
Joshua Long

Back in 2014, Google became the owner of several new “top-level domains.” Called a TLD for short, a top-level domain is the “dot-something” at the end of a domain name, for example .com or .net.
Two of the new TLDs that Google registered were .zip and .mov. You probably recognize that .zip is also a file name extension; when you download software from the Internet, it often comes bundled in a .zip archive. You may also recognize .mov as a common file name extension for video files, typically in an Apple QuickTime compatible format.
It’s hard to imagine exactly what Google was thinking. Giving the company the benefit of the doubt, perhaps they had altruistic motivations; maybe in 2014 they registered these TLDs to prevent bad guys from buying them up and abusing them. But then, just this week, Google opened the floodgates and began allowing the general public to register their own domains using these TLDs.
Could this really be so bad? Is there any reason such domains might be potentially dangerous? Let’s explore why .zip and .mov domains may put you at risk of phishing or malware attacks.
In this article:
- Apps and sites may turn .zip or .mov filenames into automatic links
- Is that long URL a link to a .zip file, or to a .zip domain?
- Is this a real threat, or is it it much ado about nothing?
- How can I learn more?
Apps and sites may turn .zip or .mov filenames into automatic links
One major problem with these new TLDs is that, depending on which app or site you use to check your e-mail, or which forums, social networks, or messaging apps you use, simply typing a file name may change your plaintext words into a link that the recipient can click or tap on—even if you didn’t intend for that to happen.
Take Twitter, for example. If you were to send someone a direct message and let them know you just sent them a file called invoices.zip, Twitter automatically turns it into a link to http://invoices.zip — without asking for confirmation or giving you the opportunity to remove the link. This is true regardless of whether the sender or recipient uses the Twitter app or a browser. Similarly, if you DM someone who’s at your home and tell them to open a movie file in your home theater library, say encanto.mov, Twitter will turn that into a link to http://encanto.mov as well.
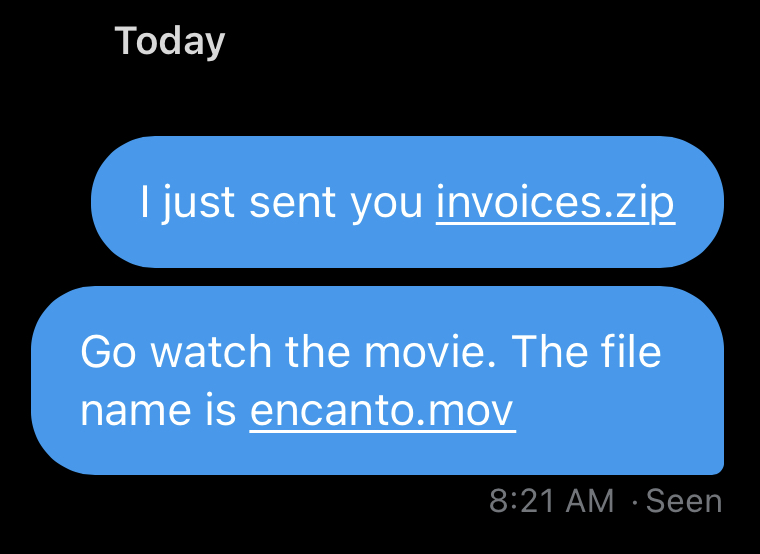
Example Twitter DMs with .zip and .mov filenames automatically displaying as clickable links. What could possibly go wrong?
Of course, you have no idea who owns such domains, or what would happen if you tapped or clicked on such links. And presumably, your recipient’s natural inclination will be to tap on those links to attempt to view the desired content.
Is that long URL a link to a .zip file, or to a .zip domain?
Security researcher Robert Graham observed that, due to an erroneous interpretation of a Web standard, browsers often allow http:// and https:// links to include a username:[email protected] format. As Graham points out, those who wrote the standard never intended for Web links to include usernames and passwords. And yet, most browsers have always supported this type of link.
So how does this relate to .zip and .mov domains? Researcher Bobby Rauch noted that, by using lookalike characters, attackers can trick victims into visiting URLs ending in .zip that appear to be hosted on known-legitimate sites, like GitHub. In reality, the domain might actually be the “.zip” that appears to be part of the file name. A site hosted at that .zip domain could potentially be designed to automatically download a .zip file upon visiting the link, so the user would be none the wiser.
Thus, it would be possible to trick a user into thinking they got a legitimate download from GitHub, when they may have actually downloaded Trojan horse malware instead.
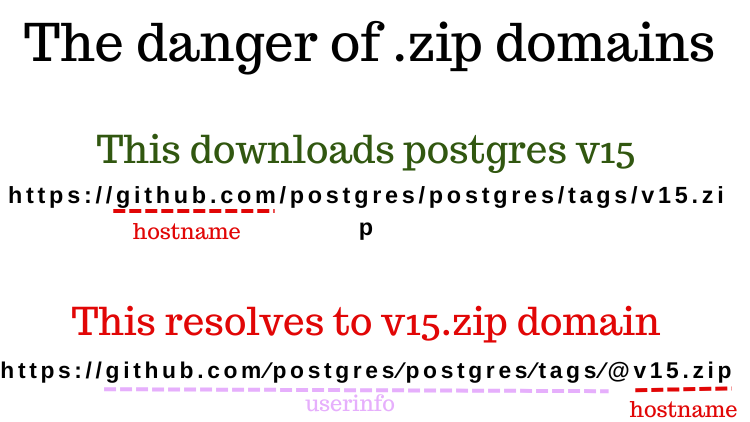
An example fake download URL that would lead to a .zip domain. Credit: Hussein Nasser.
This isn’t the first time that the username:[email protected] format in URLs has led to a potential security risk. Back in iOS 11, when scanning a QR code, the Camera app would misinterpret domains in such a way that the app would show a false domain in the scan preview.
Having way too much fun with @faker_'s iOS 11 QR code vulnerability. 😜#Apple #iOS #iOS11 #QRcode #vulnerability pic.twitter.com/sGDJq7bS0q
— Josh Long (the JoshMeister) (@theJoshMeister) April 14, 2018
Is this a real threat, or is it it much ado about nothing?
While many .zip domain registrations within the past week have been done for humorous purposes, another security researcher noticed that the domain microsoft-office.zip appeared to be an actual phishing site.
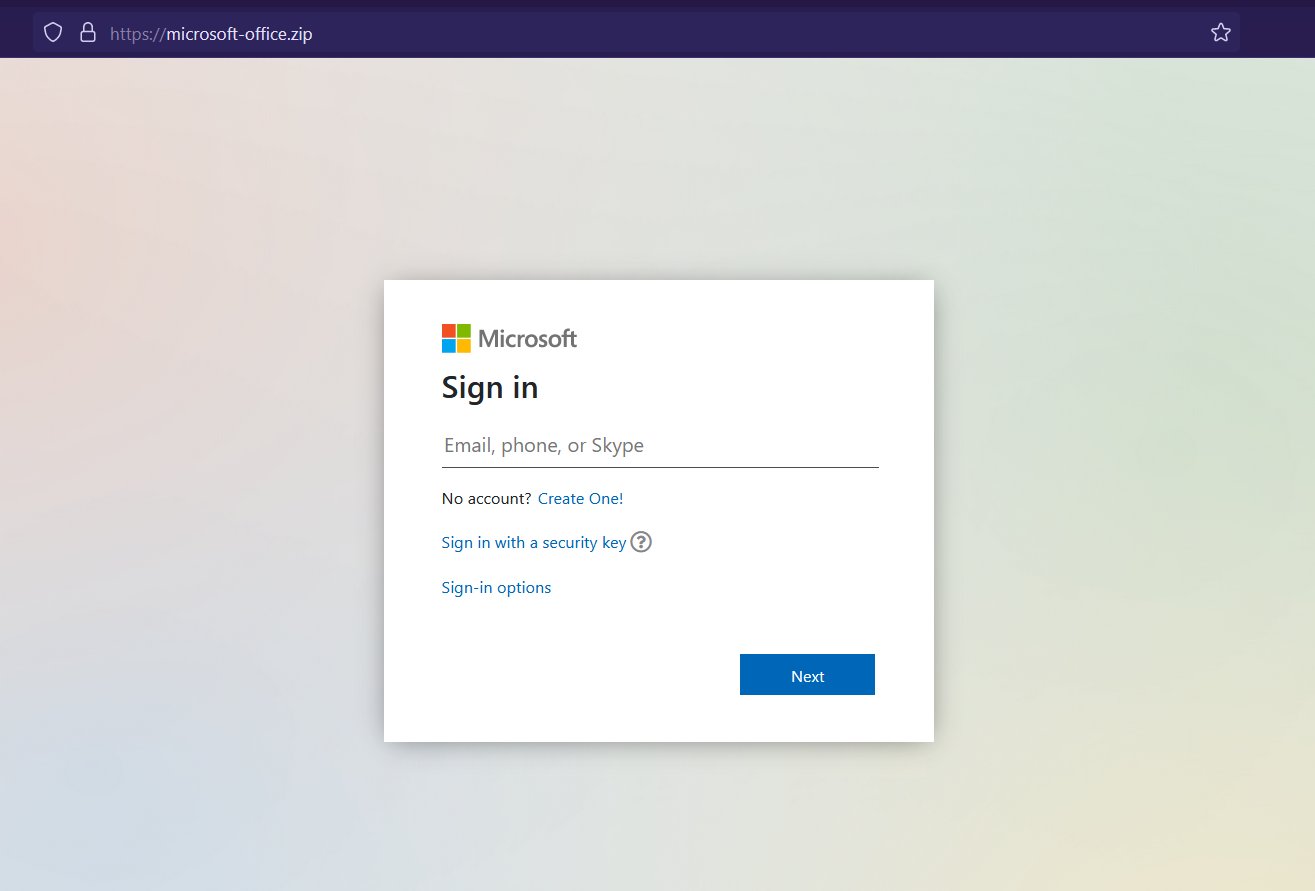
A possible Microsoft phishing site hosted at a .zip domain. Credit: Germán Fernández.
Many other domains—most of which were probably registered as jokes—give some idea of the potential for misuse:
chrome-installer.zip csgo.zip [implying a Counter-Strike game] gta6.zip [implying a Grand Theft Auto game] honeymoonpictures.zip hunterbidenlaptop.zip keygen.zip microsoftwindows.zip photoshop-cracked.zip picsofyourwife.zip setupwizard.zip statementsofwork.zip taylorswiftnudes.zip terminationletter.zip trumpclassifieddocuments.zip windowsinstaller.zip
Again, most of the specific domains above, and many other domains similar to these, were probably registered as jokes. Nevertheless, there’s a strong possibility that we’ll see real-world examples of phishing sites and malware hosted at .zip or .mov domains in the coming weeks and months. Watch out for errant links, and stay vigilant. Consider sharing this article with friends and colleagues to raise their awareness of the danger.
How can I learn more?
For more details on this story, see also Dan Goodin’s write-up at Ars Technica.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()