Recommended + Security & Privacy + Security News
Intego exclusive: HP leaves Mac users vulnerable to fax hacks
Posted on
by
Joshua Long
On Sunday, at the annual DEF CON hacker conference, the world was warned about serious flaws that could allow an attacker to infiltrate a victim’s network via a fax machine.
Researchers from Check Point released information about the vulnerabilities they discovered in a wide range of HP multifunction and all-in-one printer devices that include fax capabilities.
The so-called “Faxploit” vulnerabilities had been responsibly disclosed, and HP had already released firmware updates for affected devices prior to Check Point’s public disclosure of the full technical details.
However, HP seems to have made a serious oversight regarding their release of firmware updates.
HP Leaves Mac Users Vulnerable to Fax Hacks
 Oftentimes when HP releases firmware updates for printers and multifunction devices, the company only makes the firmware available in the form of an EXE file — a Windows application. In spite of the severity of the Faxploit bugs, HP has not made an exception to this unfortunate practice.
Oftentimes when HP releases firmware updates for printers and multifunction devices, the company only makes the firmware available in the form of an EXE file — a Windows application. In spite of the severity of the Faxploit bugs, HP has not made an exception to this unfortunate practice.
Of the more than 150 affected models for which HP released firmware updates, approximately one quarter of them do not have a Mac-compatible firmware update installer available to download through HP’s support site. Later in this article is a complete list of devices for which Mac-compatible firmware installation methods are not currently available.
This leaves companies and home users that only use macOS or Linux in a difficult position: unplug your fax line, or remain vulnerable to serious attacks.
Fax Is, Surprisingly, Still Relevant
Although fax is an antiquated technology by today’s standards, a surprising number of businesses and homes still rely on the technology.
The health care, legal, and real estate industries, and many government entities, continue to use fax machines to transmit facsimilies of sensitive printed documents. Check Point estimates that “hundreds of millions” of fax machines are still in use worldwide.
What Can Mac Users Do About Affected Devices?
Check Point said earlier this week that the vulnerability was not known to be exploited in the wild yet. However, now that details have been made available to the public, and given that a plethora of potentially interesting targets openly share their fax numbers with the world, it is rather risky to keep a known-affected fax machine plugged into a landline.
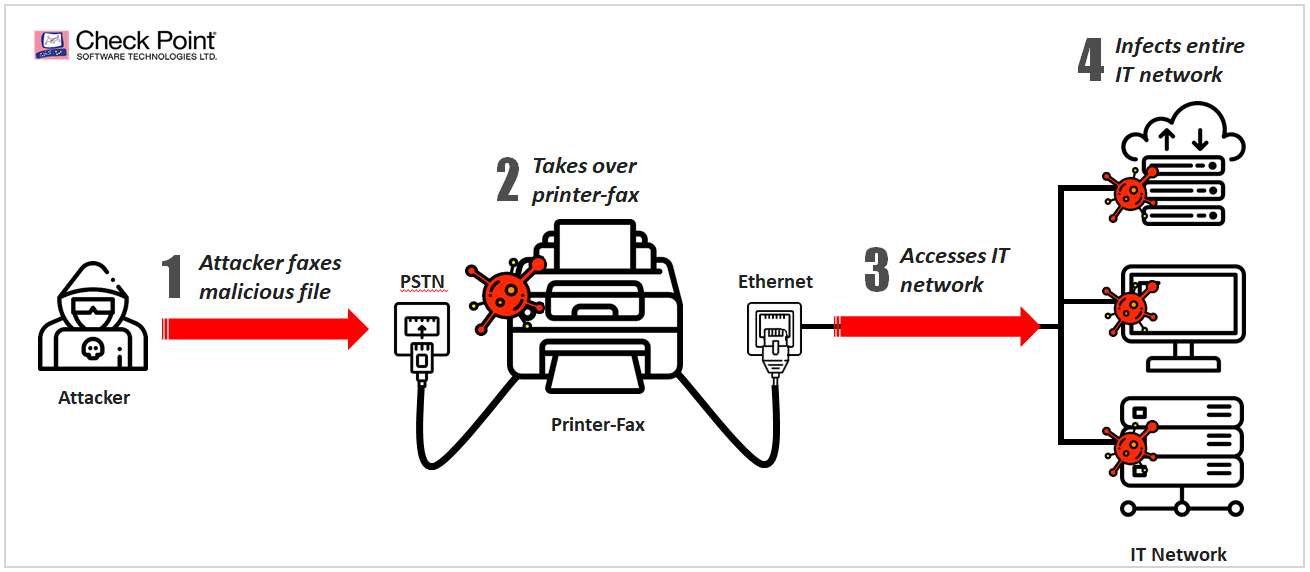
How a Faxploit attack works. Image: Check Point
If you have an affected device, but do not have access to a Windows computer, you may have a few options.
Use Boot Camp or a Windows VM
![]() If you happen to have Boot Camp already set up on your Mac, reboot into Windows to install the firmware update. If you do not have Boot Camp set up, you can buy a copy of Windows and then run the Boot Camp Assistant app to install Windows onto your Mac. Apple’s support site has instructions on how to set up Boot Camp and install Windows.
If you happen to have Boot Camp already set up on your Mac, reboot into Windows to install the firmware update. If you do not have Boot Camp set up, you can buy a copy of Windows and then run the Boot Camp Assistant app to install Windows onto your Mac. Apple’s support site has instructions on how to set up Boot Camp and install Windows.
Regarding the safety and efficacy of installing the firmware via a Windows virtual machine (i.e. via software such as VMware Fusion, Parallels Desktop, or Oracle VirtualBox), an HP representative told us, “It is safe to run the Windows compatible firmware update utilities on a Windows-based virtual machine running on Mac OS or OS X. The firmware updaters can find printers over both networked and USB connections.”
Unplug when not in use
 For home users and small businesses, if you primarily use your fax machine to send faxes but not to receive faxes, it is best to disconnect the phone line from your fax machine or multifunction printer and leave it unplugged when not in use. When you are expecting a fax, you can reconnect the landline to the machine until you receive the desired fax, and then unplug the phone cord from the machine again.
For home users and small businesses, if you primarily use your fax machine to send faxes but not to receive faxes, it is best to disconnect the phone line from your fax machine or multifunction printer and leave it unplugged when not in use. When you are expecting a fax, you can reconnect the landline to the machine until you receive the desired fax, and then unplug the phone cord from the machine again.
Other solutions
For organizations that rely on receiving frequent faxes, leaving the fax machine unplugged may not be an option. You will need to weigh the risks, and consider whether to bring in a technical support consultant with a Windows laptop to install the firmware update for you, or wait and see if HP releases a Mac-compatible firmware update method for your device; otherwise, you may consider replacing your fax machine with a different brand or model that is not (yet) known to be affected by Faxploit or similar vulnerabilities.
Affected Models
 HP has made a list of all devices known to be affected by the Faxploit vulnerabilities, which includes more than 150 devices in total. About three quarters of these devices have a firmware update available that can be installed from a Mac.
HP has made a list of all devices known to be affected by the Faxploit vulnerabilities, which includes more than 150 devices in total. About three quarters of these devices have a firmware update available that can be installed from a Mac.
Following is a list of HP multifunction devices for which the manufacturer is not currently offering a macOS-compatible firmware update method:
- HP Deskjet 4615 All-in-One Printer
- HP DeskJet 5000 series
- HP DeskJet 5275 All-in-One Printer
- HP ENVY 5000 All-in-One Printer series
- HP ENVY Photo 6200 All-in-One Printer series
- HP ENVY Photo 7100 All-in-One Printer series
- HP Officejet 4610 All-in-One Printer series
- HP OfficeJet 5200 All-in-One Printer series
- HP Officejet 6220*
- HP Officejet Pro 251dw Printer series
- HP Officejet Pro 3610 e-All-in-One Printer series
- HP Officejet Pro 3620 e-All-in-One Printer series
- HP OfficeJet Pro 7720 Wide Format All-in-One Printer series
- HP OfficeJet Pro 7730 Wide Format All-in-One Printer series
- HP OfficeJet Pro 7740 Wide Format All-in-One Printer series
- HP OfficeJet Pro 8210 Printer series
- HP OfficeJet Pro 8216 Printer
- HP Officejet Pro 8600 e-All-in-One Printer series
- HP Officejet Pro 8600 Plus e-All-in-One Printer series
- HP Officejet Pro 8600 Premium e-All-in-One Printer series
- HP OfficeJet Pro 8730 All-in-One Printer series
- HP OfficeJet Pro 8732M All-in-One Printer
- HP OfficeJet Pro 8740 All-in-One Printer series
- HP Officejet Pro X451 Printer series
- HP Officejet Pro X476 MFP series
- HP Officejet Pro X551 Printer series
- HP Officejet Pro X576 MFP series
- HP PageWide 352dw Printer series
- HP PageWide 377dw MFP
- HP PageWide Managed P55250dw Printer series
- HP PageWide Managed P57750dw MFP series
- HP PageWide Pro 452dn Printer series
- HP PageWide Pro 452dw Printer series
- HP PageWide Pro 477dn MFP series
- HP PageWide Pro 477dw MFP series
- HP PageWide Pro 552dw Printer series
- HP PageWide Pro 577dw MFP series
- HP PageWide Pro 577z MFP series
*Although HP lists the Officejet 6220 as an affected device, it doesn’t appear in HP’s software and drivers search results, so even Windows users may not have a way to update its firmware. HP has not responded to a request for clarification about this model.
HP’s Response to Intego
Shortly before publication time, an HP representative responded to our inquiries stating that it’s safe to install the firmware from a Windows virtual machine running on a Mac. Of course, this requires the purchase and installation of Windows, which is not practical for all Mac users.
As for whether HP will release macOS-compatible firmware updates for the affected devices listed above, the representative only stated that there are “more [Mac firmware updates] to be released,” but did not specify which specific devices would get Mac-compatible updates, or when those updates might become available.
This article will be updated if HP provides further information or clarifications.