Did Instagram leak your password?
Posted on
by
Joshua Long

Back in April, Instagram introduced a data export feature to comply with the General Data Protection Regulation (GDPR), a regulation in European Union law intended to protect citizens’ privacy.
But, in an ironic twist, the way in which Instagram implemented its data export feature inadvertently leaked some users’ passwords. The Facebook subsidiary notified affected users via e-mail in November.
What Happened?
![]()
Instagram’s “Download Your Data” feature worked correctly if a user clicked on the Submit button after entering their password.
However, if the user had instead pressed the Return or Enter key to submit their password, the site reportedly put the user’s password in plaintext in the URL of the resulting page. That’s a bad thing, because it means that in some very specific circumstances, it may have been possible for unauthorized parties to discover affected users’ passwords.
Instagram has since fixed the bug, so it’s safe to use the Download Your Data feature now.
Who Had Access to Leaked Passwords?
 Instagram’s server logs unintentionally collected these passwords in plaintext, so the company is reportedly deleting any passwords found in those logs.
Instagram’s server logs unintentionally collected these passwords in plaintext, so the company is reportedly deleting any passwords found in those logs.
Neither Instagram nor its parent company Facebook have responded to our inquiries about who may have had access to the affected logs or whether the log sanitization has been completed.
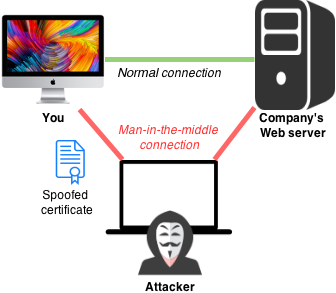
Historically it was much worse for a password to be found in a URL because it meant that any “man in the middle” (anyone in between your browser and the server to which you are connecting) could see the complete address. But now that most sites use HTTPS, only the domains—for example, instagram.com—are visible to in-between parties, not the full URLs.
Well, at least that’s true in most cases. If you or someone with access to your device has installed a special root certificate authority and configured your system to always trust it, then a man in the middle (MITM) who possesses the matching private key could even potentially see complete HTTPS URLs you’ve accessed.
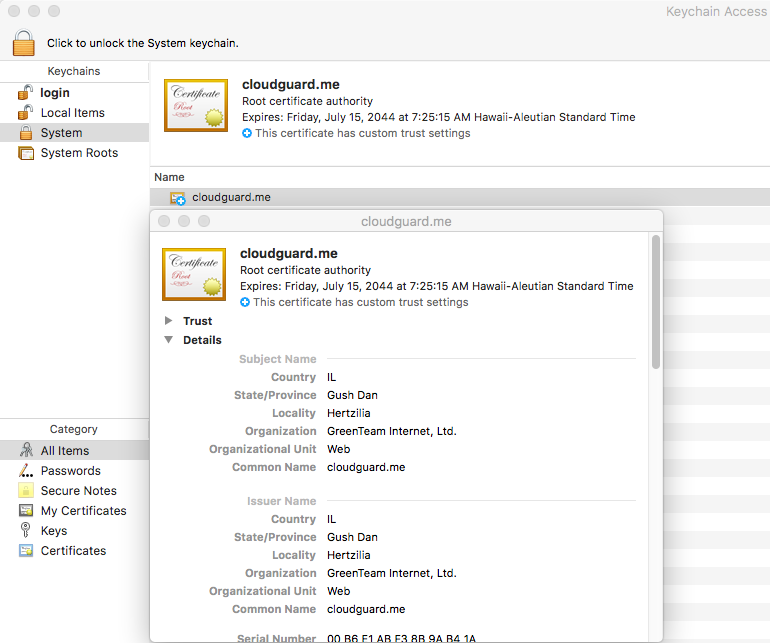
Example of an explicitly trusted, non-default root CA
The practice of leveraging an MITM certificate is common on enterprise or school networks for the purposes of monitoring employee or student activity. If a victim of the Instagram bug had such a certificate installed, then it’s possible that their password may have been stored in plaintext in their organization’s Web filter logs too.
Malware like OSX/MaMi can also engage in MITM attacks.
Of course, anyone with direct access to a victim’s device could also search the browser history to look for Instagram URLs that may contain a password. If you were unfortunate enough to have used a publicly shared computer to download your Instagram data, anyone who used the computer after you could have gotten your password unless you remembered to delete your browsing data. (For this and a plethora of other reasons, users should avoid logging into any accounts when using public kiosks at places like hotels, libraries, labs or Internet cafés.)
How Many Users Were Affected?
An Instagram spokesperson has stated that “a very small number of people” were affected by the bug, which was “discovered internally”—in other words, not reported to Instagram by a third party. Thus it seems plausible that very few people outside of Instagram were aware of the bug until after Instagram’s disclosure to affected users.
What To Do If You Might Have Been Affected
 If you’re not sure whether your Instagram account was affected, check your e-mail; you should have received notification from Instagram around November 15. If you didn’t receive an e-mail but you did use the data export feature before that date, it wouldn’t hurt to change your Instagram password and delete your browser history just to be safe. If you’ve used the same password on other sites, you’ll want to change your password elsewhere too and avoid reusing passwords across multiple sites in the future.
If you’re not sure whether your Instagram account was affected, check your e-mail; you should have received notification from Instagram around November 15. If you didn’t receive an e-mail but you did use the data export feature before that date, it wouldn’t hurt to change your Instagram password and delete your browser history just to be safe. If you’ve used the same password on other sites, you’ll want to change your password elsewhere too and avoid reusing passwords across multiple sites in the future.
How Can I Learn More?
 We discussed this topic on episode 59 of the Intego Mac Podcast. Each week we bring you engaging discussion of the latest Apple security news, so be sure to subscribe to the podcast to ensure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
We discussed this topic on episode 59 of the Intego Mac Podcast. Each week we bring you engaging discussion of the latest Apple security news, so be sure to subscribe to the podcast to ensure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
For a few additional details on this Instagram bug, you can refer to articles by Sarah Kuranda and Reed Albergotti and Lisa Vaas.
CloudGuard root CA screenshot credit: Patrick Wardle. Man in the middle diagram image credit: Nasanbuyn (CC BY-SA 4.0) and Apple; modified by Joshua Long. Girl holding CHANGE YOUR PASSWORD sign based on image by Kasuga~enwiki (CC BY-SA 3.0).