Cryptocurrency 101: Bitcoin, blockchain, and basic concepts
Posted on
by
Victor Agreda, Jr.

This is the first in a series of articles exploring Bitcoin, cryptocurrencies and their fundamental technologies, and how you might find these technologies useful and use them safely.
You’ve likely heard about Bitcoin, which is a type of cryptocurrency or digital currency, and perhaps you’ve wondered what all the fuss is about. What exactly are Bitcoins and cryptocurrency, and how does such a system work?
 You can think of Bitcoin as being a bit like the Apple II of cryptocurrency; just as Apple’s first mass-market computer was a revelation for personal computing, so Bitcoin is the first well-known application of an underlying technology called blockchain. The tech behind blockchain has been around since the 1990s, but wasn’t popularized until Bitcoin came along.
You can think of Bitcoin as being a bit like the Apple II of cryptocurrency; just as Apple’s first mass-market computer was a revelation for personal computing, so Bitcoin is the first well-known application of an underlying technology called blockchain. The tech behind blockchain has been around since the 1990s, but wasn’t popularized until Bitcoin came along.
Before diving too deep into explaining other aspects of digital currency systems, it’s helpful to first have a foundational understanding of what a blockchain is. Later, we’ll explore more fundamental concepts and key terminology. After you’ve finished reading this series, you’ll be able to better determine whether you might want to participate in the bleeding-edge world of electronic currency.
What is a blockchain?
Cryptocurrency is one of many applications made possible by blockchain technology, so think of cryptocurrency as a subset of that tech.
Blockchain is a technology that uses a set of records shared by a group of computers; a block is an individual record, and the chain is all the records comprising the full ledger. The network is comprised of computers that validate those blocks, and the corresponding chain as transactions occur. These transactions could track “money” in the form of cryptocurrency, or they could even track a vegetable from the farm to your table (which can, among other things, make pinpointing the source of a listeria outbreak in our food supply easier than ever).
The goals of a blockchain are to protect the integrity of the data, but do it in a decentralized manner, as opposed to one massive database that is controlled by one central authority. Aspects of blockchain that are particularly amenable to logistics applications include built-in privacy controls and measures to protect data integrity.
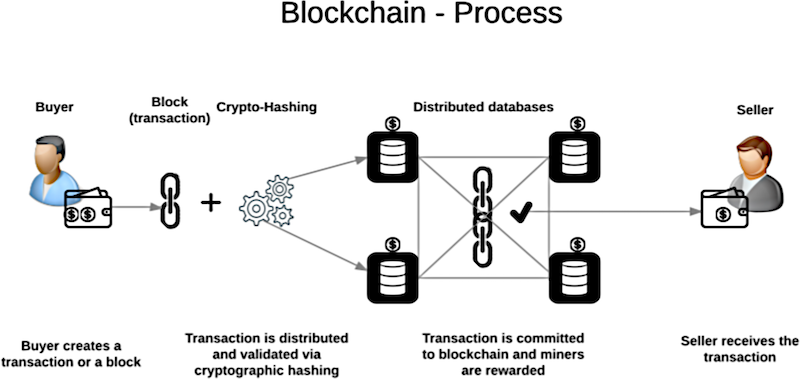
Image based on Blockchain Process by B140970324 (CC BY-SA 4.0)
How is blockchain integrity maintained?
To help visualize how a blockchain works, imagine a spreadsheet that is shared among hundreds of people. The spreadsheet is basically a bank ledger, keeping track of transactions over time. If you’ve ever worked on a database you know how important it is that changes aren’t made at the same time, which can cause data collisions. Blockchain is similar to a database in that it contains data, but there’s also logic built in to perform functions on that data. That logic, used to manage the decentralized nature of these records, is the key to how this is different from an ordinary database or ledger.
Here’s an example: two customers want to buy a product but there’s just one left in stock. Who gets it? Database administrators have a method for locking records so it’s difficult to accidentally sell that one item to two people. Blockchains, as distributed ledgers with built-in protocols, handle changes.
Transactions on the blockchain are “moderated” by the protocols of that network, which could be a consensus vote by all the computers on the chain. Bitcoin has its own blockchain network, and Ethereum and other cryptocurrencies (sometimes called “altcoins,” as in alternatives to Bitcoin) each have their own separate network. Each one has very specific rules about how ledger entries can be made.
Remember that there may be thousands of machines with a copy of this ledger. The distributed, decentralized nature of the blockchain, and therefore cryptocurrency, is one of the biggest advantages according to advocates, because decision-making has been baked into the protocols of the network itself.
Decentralized finance
The rules vary from network to network, but the idea is that a decentralized group of computers can make decisions without a centralized decision-maker. This is in contrast to how most of us use banks, which are centralized financial institutions. You trust a bank because it’s a bank, and there’s a group of people responsible for the security and veracity of your bank account’s information, and because our money is insured to a certain amount. But the government is also a central authority.
Advocates of “DeFi” (decentralized finance) say that trust comes from the privacy controls and rules embedded in cryptocurrency networks, and not from a central source like a bank’s database or a government’s oversight. DeFi is all about decentralizing authority, removing the power from a central authority and putting it in the hands of a self-governing network. Once the rules of the network are in place, no one person can control or own it fully.
Consensus
With traditional fiat currencies, monetary values depend on governmental policies and centralized banks. With cryptocurrencies, where there is no central authority to mediate, how can decentralized financial ledgers keep track of all these transactions without succumbing to data collisions or unauthorized changes? This is where things can get quite complicated, and different cryptocurrencies handle this problem in different ways. But one key principle is the idea of consensus.
To understand the basics of consensus, consider someone who wants to buy a coin of some cryptocurrency. (We’ll go into detail about how this is done in the real world in another article in this series, but for now let’s just look at the theory.) When a coin is purchased, a ledger line must be written indicating the purchase. Computers on the blockchain’s network vote on this change to the ledger, and if more than half agree, the line is written. If the network votes against the change, the line is not written into the ledger.
If you’d like to learn about some of the nerdier, much more technical details about consensus, you can read up on the Byzantine generals problem, proof of work, and proof of stake.
Fraud and forks
 In the world of cryptocurrency, the trust factor is a big issue, and is largely the result of cryptographic processes and the consensus methods employed by the network. In effect, it’s all math-based. You trust that the system is secure, and that transactions are properly vetted, and that the transactions will appear in your digital wallet accordingly.
In the world of cryptocurrency, the trust factor is a big issue, and is largely the result of cryptographic processes and the consensus methods employed by the network. In effect, it’s all math-based. You trust that the system is secure, and that transactions are properly vetted, and that the transactions will appear in your digital wallet accordingly.
But since crypto is an entirely new way of doing things, there have been hiccups. Security issues have made headlines, with either coins being stolen or entire ledgers requiring a “fork,” or branch, to undo changes that weren’t properly authorized or exploited flaws in the system. Sometimes forks are made pre-emptively to ensure security. While it’s easy to point to these as indications that cryptocurrency is too unreliable, keep in mind that humans have embezzled money from banks, and centralized financial institutions are not inherently immune to fraud, money laundering, or just plain bad investing.
Bitcoin is just the beginning
There are lots of cryptocurrencies out there—currently over 5,000, according to CoinMarketCap. Bitcoin, having been the first to really gain traction and work properly, has become a sort of role model for the industry. It has a hard ceiling when it comes to coins, also making it a bit like gold’s deflationary pressure. Ethereum, on the other hand, is more of a utility currency, and uses “gas” to reflect the fee for making transactions on its network.
Still other coins are implementing novel methods to verify their blockchain entries or differentiate themselves in other ways. “Stablecoins” are particularly notable, as they try to reduce price fluctuations by pegging their value to fiat currency. A coin or token might be 1:1 with the U.S. dollar, for example, which can be useful when exchanging coins, such as cashing out your holdings or moving from one coin to another.
What’s important to remember is that cryptocurrency is a living experiment in decentralized finance—that is, moving away from central banking, fiat currencies, and traditional chains of trust. It’s a bold new direction in modern computing, leveraging algorithms, encryption, computational power, and perhaps a bit of luck to create an alternative asset class. It’s a subset of blockchain technology, originally created as a distributed database with protocols to verify data as new blocks are added to the chain.
How to avoid losing cryptocurrency to fraud and malware
There are a couple of basic tips to keep in mind to avoid losing all of your cryptocurrency to scams or malware.
Never give out your seed phrase
Scammers, phishing sites, and malware will often try to trick you into sharing the seed phrase you were given when you set up your crypto wallet. A seed phrase is a sequence of words that effectively serves as a master password for your wallet; with it, anyone can drain your wallet of all of its assets, including cryptocurrencies, NFT (non-fungible token) artwork, and more.
Use trusted antivirus software to block crypto-stealer malware
Another critical step to keep your digital assets safe is to use a trusted antivirus.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware—including cryptocurrency stealer malware.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s current Mac operating system, macOS Sonoma.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware.
How can I learn more?
This week on episode 122 the Intego Mac Podcast, I joined Kirk and Josh to discuss the basics of cryptocurrency (as well as the latest Apple, security, and privacy news). Be sure to subscribe to make sure you never miss the latest episode!
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
Photo credits: Coin header photo adapted from Cryptocurrencies on a computer parts by Marco Verch, licensed under CC BY 2.0. Apple II photo by Rama; CC BY-SA 2.0.