Cross-Platform Adware Poses as Flash Player Update
Posted on
by
Lysa Myers
Once again, fraudulent developers are attempting to fool people into installing their adware by signing their file—which pretends to be an Adobe Flash Player update—with a Developer ID. This tactic is not new, but why try something new when the tried and true tactics are apparently still working?
This new adware has versions for both Windows and Mac OS X, and works as an extension for Chrome, Firefox and Safari to different extents based on the operating system. For Macs, because the installer is a Windows executable auto-extractor, there’s no direct installation.
This scam-extension appears to be found on a number of different types of websites, such as adult-themed and file-sharing sites. Once downloaded onto a user’s machine, it must then be installed in order to execute. Once it’s running, it places ads (sometimes pornographic in nature) into legitimate websites, which can make it appear that even children’s sites are serving these lascivious ads. The ads are not served by the usual mechanisms, so they are not blocked by ad-blockers.
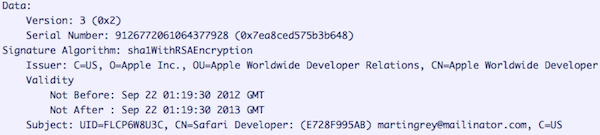
The adware installer is signed by an Apple Developer ID belonging to “[email protected],” which expires in a month (on September 22), at which point it will no longer be recognized as valid.
Hat tip to Jerome Segura of Malwarebytes for information on this threat.
Intego VirusBarrier users with up-to-date virus definitions will be protected against this threat, which is detected as OSX/ClickAgent.FLA. This is a great reminder that it’s always best to go directly to the source for software updates, rather than following pop-ups that purport to be updates.