Recommended + Security & Privacy
Apple’s Poor Patching Policies Potentially Make Users’ Security and Privacy Precarious
Posted on
by
Joshua Long

Apple’s practices regarding security updates are frustrating and perplexing, to say the least—and may endanger users.
The company often delays patching vulnerabilities for many months after researchers report them.
Apple frequently waits to disclose the fact that it patched a vulnerability for a month (or longer) before adding it to the list of issues resolved in a given update.
The company almost never publicly states its policies about how long a given operating system will get security updates, or what types of security issues will continue to get patched.
Apple also doesn’t explicitly state why it patches some vulnerabilities for some operating system versions but not others. Security-conscious users can only speculate:
“Perhaps this vulnerability just didn’t affect that version of the OS?”
“Maybe Apple didn’t feel the need to mention that a new OS was inherently safe and didn’t need a patch?”
“Could it be that Apple actually did patch that vulnerability, but simply forgot to mention it?”
“Or did Apple patch that vulnerability and intentionally not mention it for some reason?”
Apple’s lack of transparency can be particularly problematic in certain situations. I’ll get back to that shortly.
Confirmed: You need the latest macOS version
Last month, I spoke at Objective by the Sea v4.0, an Apple-focused security conference, about this very subject. Specifically, I focused on whether the two previous versions of macOS get the same treatment as the current macOS version when it comes to security updates.
I recommend watching the full talk if you have 30 minutes. You should also sign up to be notified when our upcoming white paper gets published, which documents my intriguing discoveries in much greater detail.
But the executive summary is this: being on the very latest version of macOS is mandatory to stay safe from every “actively exploited” (i.e. in the wild) vulnerability. Those are generally among the most problematic security issues, because bad guys are already using them against their targets.
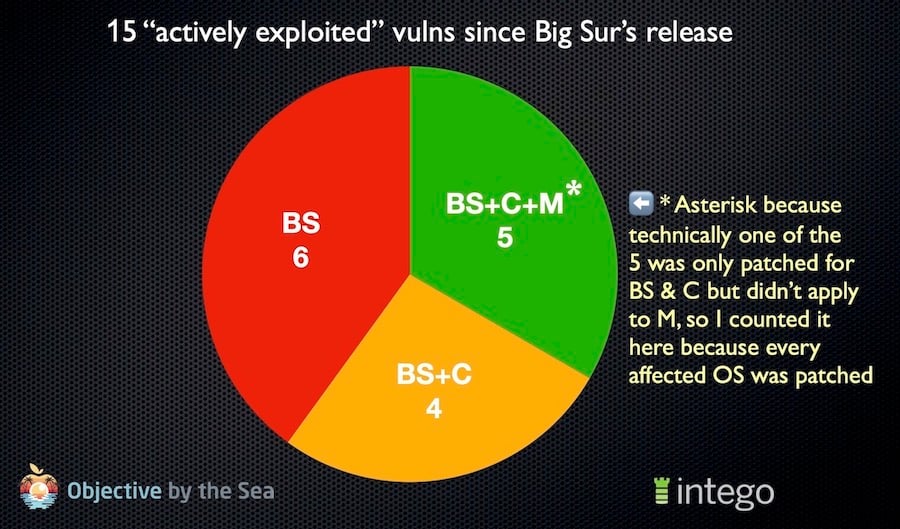
Of the 15 Big Sur-era “actively exploited” vulnerabilities, only Big Sur received all 15.
As mentioned in the talk and detailed in the upcoming white paper, macOS Mojave is—and presumably always will be—vulnerable to the “FORCEDENTRY” bug that has been actively exploited by the Pegasus spyware. There are other vulnerabilities that presumably affect macOS Mojave—and some, for now at least, that affect macOS Big Sur and Catalina—but remain unpatched.
You’d never know these facts based solely on Apple’s actions or statements. Most users assume that when they install security updates, Apple has fixed every known vulnerability, and their Mac is perfectly safe. But in reality, unless you’re running the very latest major version of macOS (now macOS Monterey), Apple’s updates provide only selective fixes along with a false sense of security.
Quick update: #Safari 15.1 was released for Big Sur & Catalina yesterday, & its release notes indicate that 5 of the 7 #WebKit vulnerabilities were fixed. Two appear to remain unpatched for 11.x and 10.15.x: CVEs 2021-30823 (Gullasch @0x41414141) & 2021-30861 (@_r3ggi & Pickren).
— Josh Long (the JoshMeister) (@theJoshMeister) October 28, 2021
The release of macOS Monterey this week unfortunately hasn’t brought about any improvements.
Are iOS and iPadOS similarly impacted?
Too little time has elapsed since Apple released iOS (and iPadOS) 15 to determine how similar the situation will be for iOS vulnerabilities. Before iOS 15’s September release, Apple only fully supported iOS 14, with occasional sparse updates for iOS 12. So far, it appears we can expect to see much of the same with iOS as with macOS.
Today, Apple fully supports iOS 15, and also “important security updates” for iOS 14 by publicly stated policy. The company seems to still occasionally release security updates for iOS 12, apparently limited to “actively exploited” vulnerabilities. (Apple has never actually made a public statement about its continued limited support of iOS 12.)
It seems a bit strange that Apple has chosen to continue supporting iOS 14, intentionally fragmenting its installed base. Android has received criticism about its OS fragmentation for years, so this seems like an odd decision for Apple. Because iOS 15 supports exactly the same hardware as iOS 14, no one would have had to miss out on security updates if Apple had stopped supporting iOS 14. All iOS 14 users could have simply updated to iOS 15 to continue getting security updates.
But now, as with macOS, there seems to be some disparity between what gets patched for iOS 15 versus iOS 14.
Most notably, the iOS 15 (and 15.0.1, 15.0.2, and 15.1) release notes don’t mention two “actively exploited” vulnerabilities patched in iOS 14.8. One of those is CVE-2021-30860, aka FORCEDENTRY—a vulnerability that the Pegasus spyware exploited.
Apple never stated whether or not iOS 15.x fixes the vulnerability. Other vulnerabilities are listed in both iOS 14.8’s and iOS 15’s release notes, but the two “actively exploited” ones are only mentioned in iOS 14.8’s notes. Once again, this leaves the issue open to speculation.
Apple has not responded to multiple requests for comment about this issue.
I have reached out to other researchers in the community who are familiar with the FORCEDENTRY vulnerability. If anyone confirms whether or not iOS 15.1 is still vulnerable, I will update this article with their findings.
Update: Researchers Tom McGuire and Mickey Jin both confirmed to me that the public (non-beta) releases of iOS 15.0 and later are not affected by the FORCEDENTRY vulnerability. (Jin and McGuire have also both confirmed that macOS Mojave remains affected.) It is mystifying that Apple would list 14 other vulnerabilities simultaneously in both iOS 14.8’s and iOS 15’s release notes, while a vulnerability that was fixed in both operating systems and was “actively exploited” was not listed in iOS 15’s release notes.
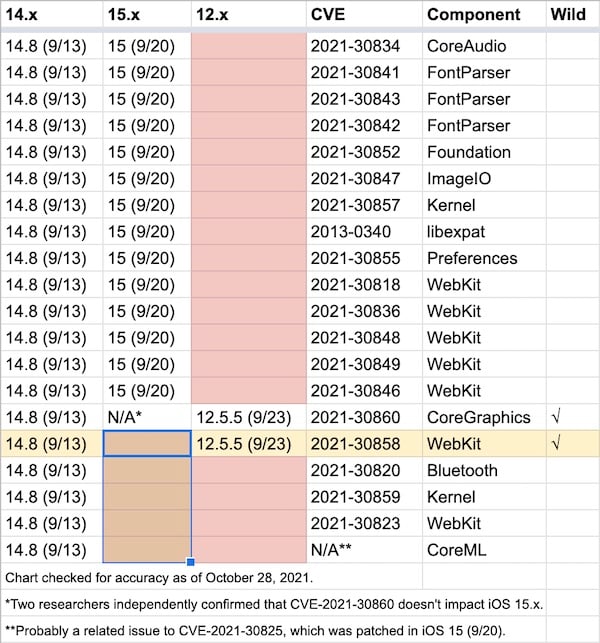
A list of iOS 14.8 patches. Apple’s release notes seemed to indicate that 14 of the 20 were also addressed in iOS 15. A 15th has been confirmed. But what about the remaining five?
We still don’t know (and may never know) whether the anonymously reported, “actively exploited” CVE-2021-30858 WebKit vulnerability affects iOS 15. But one thing we can fairly confidently infer from Apple’s documentation is that iOS 15 is getting more patches than iOS 14 and iOS 12.
Here’s a ridiculously tall chart showing everything #Apple’s said (so far) has been patched in #iOS/iPadOS since 14.8’s release, for 15.x, 14.x, and 12.x. Seems evident that #iOS15, like #macOSMonterey, is getting the most patches and is a safer choice than its predecessors. pic.twitter.com/VbeC3gGkCi
— Josh Long (the JoshMeister) (@theJoshMeister) October 29, 2021
What Apple can and should be doing better
It shouldn’t have to be this way. The public shouldn’t be left to wonder which Apple operating systems are actually safe to use and which ones have, shall we say, lackadaisical security.
Following are several things that Apple can and should be doing better.
1. Apple needs to be transparent about which issues it hasn’t and won’t fix, and why.
People outside of Apple shouldn’t have to figure out what has been patched or not. Apple itself should clearly state the reasons for the lack of parity between OS patches. Nobody should ever be left wondering why certain vulnerabilities evidently aren’t patched for certain operating systems.
Similarly, Apple should never give anyone a false sense of security. When older OS versions only get some patches and not others, Apple needs to make this extremely clear. This will encourage users to upgrade to the latest (and fully supported) major OS, which is generally a good thing for both Apple and users.
2. Apple needs to state its security update and OS support policies publicly and clearly.
Microsoft actually does a great job at this; its products have a clearly defined date on which they will no longer receive security updates. Apple could learn a thing or two from Microsoft in this regard.
3. Apple needs to respond to researchers and journalists within 24 hours about security issues.
The company should have a policy to respond within one business day (or less) to security reports and media inquiries. Apple should never leave security researchers or journalists feeling ignored.
If the lack of quick responses is due to staffing issues, Apple should spend some of its billions of dollars in cash on hand to hire more people.
4. Apple needs to resolve security issues within 90 days.
Resolution within 90 days is the industry standard. Google Project Zero and other groups give companies 90 days to patch before disclosing security issues to the public. When researchers work directly with Apple, they sometimes find that Apple takes much longer than this to patch a vulnerability.
Again, if the lack of quick patching is due to staffing issues, Apple can afford to hire more people.
5. Apple needs to improve its bug bounty program.
There is room for improvement in terms of both the scope (the types of issues for which Apple will pay bounties) and the payout amounts of Apple’s bug bounty program. Many researchers who have responsibly disclosed valuable security vulnerabilities directly to Apple have found the process and the results frustrating.
Apple should be rewarding responsible security researchers much better than it currently does. There are many better bug bounty programs than Apple’s. The company needs to get feedback from researchers and bug bounty program experts and then implement improvements.
How can I learn more?
For more discussion of Apple’s patching disparities, watch my 30-minute conference talk, sign up to get notified about the upcoming white paper, and follow our weekly Intego Mac Podcast where we’ve been discussing this topic in recent weeks.
Each week on the podcast, we discuss the latest Apple news, security and privacy stories, and more. Be sure to follow the podcast in Apple Podcasts (or wherever else you listen) to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
Image credits: iPhone by Rafael Fernandez (CC BY-SA 4.0); Pegasus by Nicolas Raymond (CC BY 2.0); composition by Joshua Long, Intego (CC BY-SA 4.0).