Malware + Security & Privacy + Security News
Apple Security: 2014 Year In Review
Posted on
by
Joshua Long
The computer security stories seemed to be virtually nonstop over the past year, so there’s a good chance you may have missed some stories. Make sure you haven’t missed anything important—read on for a quick review of some significant Apple-related security stories of 2014.
Perhaps the most widely publicized Apple security problem of 2014 was the celebrity photo leak a few months ago, when a number of celebrities’ private photographs were posted online, apparently facilitated by a flaw in iCloud security. (It’s worth mentioning that although Apple’s iCloud got the brunt of the blame, some of the leaked photos were evidently taken on Android devices and webcams.) Apple admitted that it had identified a way that attackers could brute-force iCloud passwords and stated that the issue had been rectified. Just last week, however, a hacker tool was released that again allowed attackers to brute-force iCloud passwords, but Apple fixed the problem early this week. In case similar flaws are found in the future, be sure to use a very strong password for your iCloud account and enable two-step verification.
 Apple also had a bit of public embarrassment when a developer revealed that he had discovered a way to obtain, by means of a bug in Apple’s developer site, the personal contact information of all Apple employees (all the way up to executives such as Tim Cook and Phil Schiller) and all registered developers (including, potentially, Flappy Bird developer Dong Nguyen, who was distressed by all the personal attention he received due to his iOS game’s unanticipated popularity). Apple quickly patched the bug.
Apple also had a bit of public embarrassment when a developer revealed that he had discovered a way to obtain, by means of a bug in Apple’s developer site, the personal contact information of all Apple employees (all the way up to executives such as Tim Cook and Phil Schiller) and all registered developers (including, potentially, Flappy Bird developer Dong Nguyen, who was distressed by all the personal attention he received due to his iOS game’s unanticipated popularity). Apple quickly patched the bug.
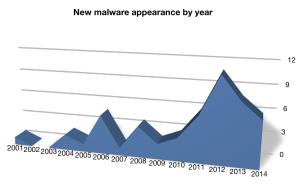
There were quite a few new samples of OS X malware that were discovered in 2014. Apple’s built-in Safe Downloads List (aka XProtect, the rudimentary unsafe-download blocker built into Snow Leopard and later) was updated 12 times throughout the year. Somewhat surprisingly, Apple has (for now) continued to release XProtect updates for Snow Leopard and Lion even though both OS X versions are no longer receiving security patches to the operating system itself. (Perhaps Apple is trying to prevent headlines about armies of Mac botnets; after all, Lion and earlier versions of OS X comprise roughly one-fifth of the Mac installed base, as I reported here.)
Independent security researcher Thomas Reed recently wrote up a list of the biggest malware threats he observed in 2014, if you’re interested in reading some technical details. While XProtect and standalone malware removal tools can certainly be helpful, they don’t provide the active security protection offered by full-fledged Mac antivirus products; might we recommend some options for your Mac?
The past year also seemed to follow a trend of nicknaming major security exploits, for example Heartbleed, Shellshock, and POODLE. The main thing you need to do in order to stay safe is to make sure you’re running a supported version of OS X and a fully updated Web browser. You may also need to change your passwords—if you haven’t already done so—on sites that may have been vulnerable to Heartbleed; you can find a partial list of sites here. As a follow-up note on Shellshock: Snow Leopard and older versions of OS X did not get an official patch from Apple, but you can patch it yourself.
Just before Christmas, Apple patched a widely publicized critical NTP vulnerability. This led to what some saw as a milestone in Apple OS security: it was the first time Apple has automatically patched a vulnerability on all supported versions of an OS without first prompting the user (unless you count XProtect, which updates in the background and, in addition to the aforementioned download blocking, also prevents highly exploited versions of Flash Player and Java from running in your Web browsers).
Last year also marked the mysterious death of TrueCrypt, which had been a cross-platform whole-drive encryption product that was available as freeware. Mac users of TrueCrypt can switch to FileVault 2, which is built into Lion and later versions of OS X.
With the recent release of OS X Yosemite (version 10.10), Apple stopped releasing security updates for Lion (10.7)—including the Lion version of OS X Server. Most Macs running Lion can be upgraded to Yosemite, which is a free* upgrade available from the Mac App Store; see my guide to which Macs can (and can’t) run Yosemite.
*Note that if you’re upgrading a Mac server, OS X Server is a paid upgrade ($19.99 in the Mac App Store) after upgrading the base operating system to Yosemite.
 Apple also stopped releasing iTunes updates for Mac OS X Snow Leopard (version 10.6), which had already stopped receiving base OS security updates when Mavericks (10.9) was released in 2013. Although the cessation of iTunes updates for Snow Leopard doesn’t have any immediate security implications, if future versions of iTunes include security fixes, they most likely won’t be made available to Snow Leopard users. However, if you’re still using Snow Leopard as a client OS at this point, it’s really time to move on, if at all possible; XProtect updates and antivirus software can’t always protect you from unpatched vulnerabilities in your core operating system. Again, see our upgrade guide if you’re not sure whether your Mac can be upgraded, and for tips on what to do if you can’t upgrade to a supported version of OS X.
Apple also stopped releasing iTunes updates for Mac OS X Snow Leopard (version 10.6), which had already stopped receiving base OS security updates when Mavericks (10.9) was released in 2013. Although the cessation of iTunes updates for Snow Leopard doesn’t have any immediate security implications, if future versions of iTunes include security fixes, they most likely won’t be made available to Snow Leopard users. However, if you’re still using Snow Leopard as a client OS at this point, it’s really time to move on, if at all possible; XProtect updates and antivirus software can’t always protect you from unpatched vulnerabilities in your core operating system. Again, see our upgrade guide if you’re not sure whether your Mac can be upgraded, and for tips on what to do if you can’t upgrade to a supported version of OS X.
There was also a plethora of password database breaches in 2014, which in some cases prompted companies to ask its users to change their passwords. I mentioned a few such occurrences back in May. As a standard best practice, it’s wise to use a unique password for each site. If you have accounts at a lot of sites and can’t memorize every password, consider using a reputable password management program; we shared some Mac and iOS options a couple years ago. (For thoughts about why storing your passwords in a single secure program might not be a bad idea, see this article, or you can take a look at our past articles on password security.)